AES (acronym of Advanced Encryption Standard) is a symmetric encryption algorithm. The algorithm was developed by two Belgian cryptographer Joan Daemen and Vincent Rijmen. AES was designed to be efficient in both hardware and software, and supports a block length of 128 bits and key lengths of 128, 192, and 256 bits. Key generators are constructed using one of the getInstance class methods of this class. KeyGenerator objects are reusable, i.e., after a key has been generated, the same KeyGenerator object can be re-used to generate further keys. There are two ways to generate a key: in an algorithm-independent manner, and in an algorithm-specific manner. Not all key generation methods are created equal, and you may want to explicitly choose e.g. The key generation method of a provider. This is especially of use for providers for security tokens. For AES though, the random number generator may be of more importance - you may for instance want to use a slower, more secure, FIPS certified random number generator instead of the default. Such use may be expressed as DK = KDF(key, salt, iterations), where DK is the derived key, KDF is the key derivation function, key is the original key or password, salt is a random number which acts as cryptographic salt, and iterations refers to the number of iterations of a sub-function. The derived key is used instead of the original key. The AES key is nothing more than a specific sized byte array (256-bit for AES 256 or 32 bytes) that is generated by the keytool(see above). Alternative Parameteters.
In cryptography, a key derivation function (KDF) is a cryptographic hash function that derives one or more secret keys from a secret value such as a master key, a password, or a passphrase using a pseudorandom function.[1][2] KDFs can be used to stretch keys into longer keys or to obtain keys of a required format, such as converting a group element that is the result of a Diffie–Hellman key exchange into a symmetric key for use with AES. Keyed cryptographic hash functions are popular examples of pseudorandom functions used for key derivation.[3]
Uses of KDFs[edit]
- In conjunction with non-secret parameters to derive one or more keys from a common secret value (which is sometimes also referred to as 'key diversification'). Such use may prevent an attacker who obtains a derived key from learning useful information about either the input secret value or any of the other derived keys. A KDF may also be used to ensure that derived keys have other desirable properties, such as avoiding 'weak keys' in some specific encryption systems.
- The most common[citation needed] use of KDFs is the password hashing approach to password verification, as used by the passwd file or shadow password file. KDFs happen to have the characteristics desired for a 'password hash function', even though they were not originally designed for this purpose.[citation needed] The non-secret parameters are called 'salt' in this context.
- In 2013 a Password Hashing Competition was announced to choose a new, standard algorithm for password hashing. On 20 July 2015 the competition ended and Argon2 was announced as the final winner. Four other algorithms received special recognition: Catena, Lyra2, Makwa and yescrypt.[4]
- As components of multiparty key-agreement protocols. Examples of such key derivation functions include KDF1, defined in IEEE Std 1363-2000, and similar functions in ANSI X9.42.
- To derive keys from secret passwords or passphrases.
- To derive keys of different length from the ones provided: one example of KDFs designed for this purpose is HKDF.
- Key stretching and key strengthening.
Key stretching and key strengthening[edit]
Key derivation functions are also used in applications to derive keys from secret passwords or passphrases, which typically do not have the desired properties to be used directly as cryptographic keys. In such applications, it is generally recommended that the key derivation function be made deliberately slow so as to frustrate brute-force attack or dictionary attack on the password or passphrase input value.
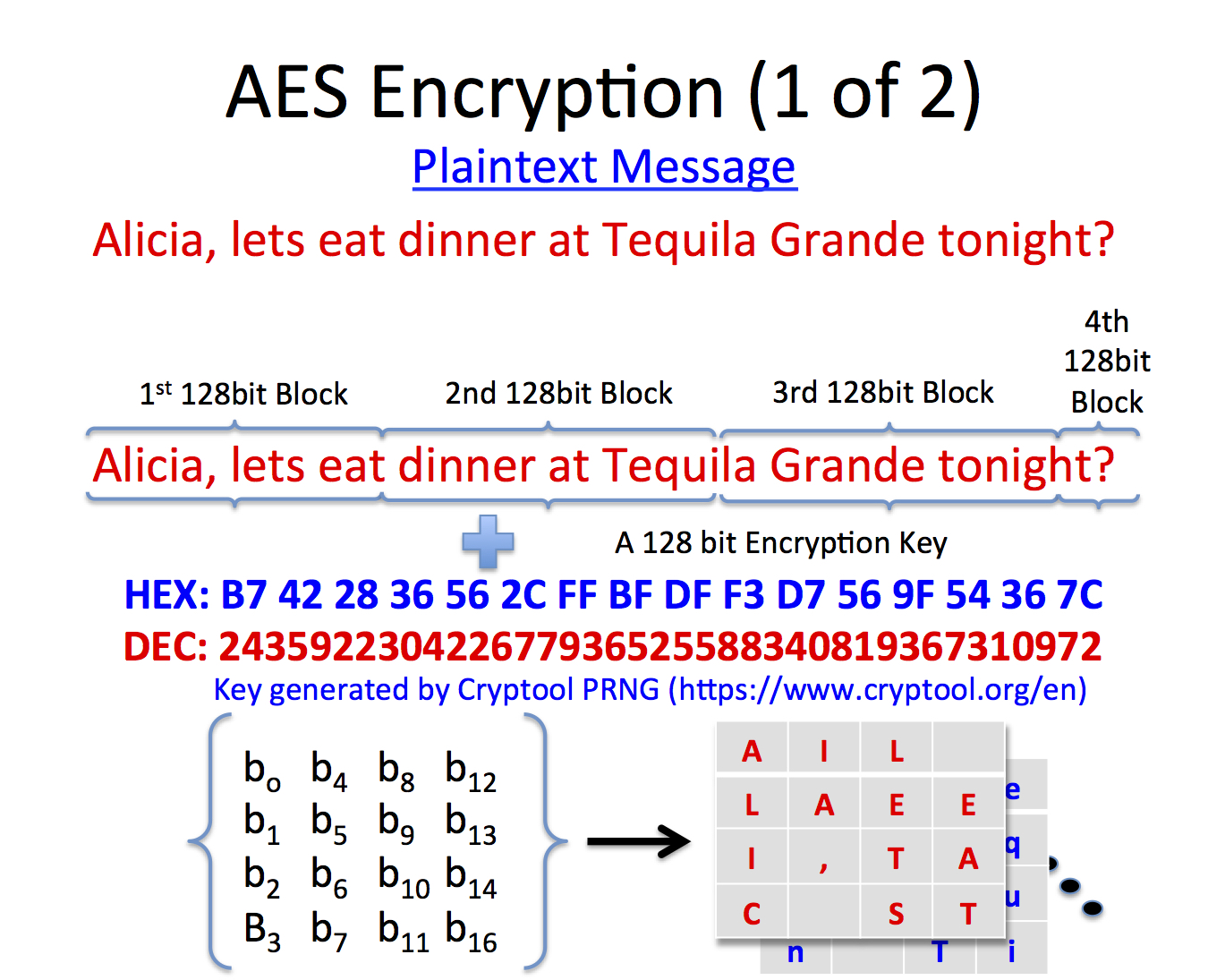
Such use may be expressed as DK = KDF(key, salt, iterations), where DK is the derived key, KDF is the key derivation function, key is the original key or password, salt is a random number which acts as cryptographic salt, and iterations refers to the number of iterations of a sub-function. The derived key is used instead of the original key or password as the key to the system. The values of the salt and the number of iterations (if it is not fixed) are stored with the hashed password or sent as cleartext (unencrypted) with an encrypted message.[5]
The difficulty of a brute force attack increases with the number of iterations. A practical limit on the iteration count is the unwillingness of users to tolerate a perceptible delay in logging into a computer or seeing a decrypted message. The use of salt prevents the attackers from precomputing a dictionary of derived keys.[5]
An alternative approach, called key strengthening, extends the key with a random salt, but then (unlike in key stretching) securely deletes the salt.[6] This forces both the attacker and legitimate users to perform a brute-force search for the salt value.[7] Although the paper that introduced key stretching[8] referred to this earlier technique and intentionally chose a different name, the term 'key strengthening' is now often (arguably incorrectly) used to refer to key stretching.
History[edit]
The first[citation needed] deliberately slow (key stretching) password-based key derivation function was called 'crypt' (or 'crypt(3)' after its man page), and was invented by Robert Morris in 1978. It would encrypt a constant (zero), using the first 8 characters of the user's password as the key, by performing 25 iterations of a modified DES encryption algorithm (in which a 12-bit number read from the real-time computer clock is used to perturb the calculations). The resulting 64-bit number is encoded as 11 printable characters and then stored in the Unix password file.[9] While it was a great advance at the time, increases in processor speeds since the PDP-11 era have made brute-force attacks against crypt feasible, and advances in storage have rendered the 12-bit salt inadequate. The crypt function's design also limits the user password to 8 characters, which limits the keyspace and makes strong passphrases impossible.[citation needed]
Modern password-based key derivation functions, such as PBKDF2 (specified in RFC 2898), use a cryptographic hash, such as SHA-2, more salt (e.g. 64 bits and greater) and a high iteration count (often tens or hundreds of thousands).
Aes Key Generator Java
NIST requires at least 128 bits of random salt and a NIST-approved cryptographic function, such as the SHA series or AES (MD5 is not approved).[10] Although high throughput is a desirable property in general-purpose hash functions, the opposite is true in password security applications in which defending against brute-force cracking is a primary concern. The growing use of massively-parallel hardware such as GPUs, FPGAs, and even ASICs for brute-force cracking has made the selection of a suitable algorithms even more critical because the good algorithm should not only enforce a certain amount of computational cost not only on CPUs, but also resist the cost/performance advantages of modern massively-parallel platforms for such tasks. Various algorithms have been designed specifically for this purpose, including bcrypt, scrypt and, more recently, Lyra2 and Argon2 (the latter being the winner of the Password Hashing Competition). The large-scale Ashley Madison data breach in which roughly 36 million passwords hashes were stolen by attackers illustrated the importance of algorithm selection in securing passwords. Although bcrypt was employed to protect the hashes (making large scale brute-force cracking expensive and time-consuming), a significant portion of the accounts in the compromised data also contained a password hash based on the general-purpose MD5 algorithm which made it possible for over 11 million of the passwords to be cracked in a matter of weeks.[11]
In June 2017, NIST issued a new revision of their digital authentication guidelines, NIST SP 800-63B-3,[12]:5.1.1.1 stating that: 'Verifiers SHALL store memorized secrets [i.e. passwords] in a form that is resistant to offline attacks. Memorized secrets SHALL be salted and hashed using a suitable one-way key derivation function. Key derivation functions take a password, a salt, and a cost factor as inputs then generate a password hash. Their purpose is to make each password guessing trial by an attacker who has obtained a password hash file expensive and therefore the cost of a guessing attack high or prohibitive.' and that 'The salt SHALL be at least 32 bits in length and be chosen arbitrarily so as to minimize salt value collisions among stored hashes.'
References[edit]
- ^Bezzi, Michele; et al. (2011). 'Data privacy'. In Camenisch, Jan et al. (eds.). Privacy and Identity Management for Life. Springer. pp. 185–186. ISBN9783642203176.CS1 maint: uses editors parameter (link)
- ^Kaliski, Burt; RSA Laboratories. 'RFC 2898 – PKCS #5: Password-Based Cryptography Specification, Version 2.0'. IETF.
- ^Zdziarski, Jonathan (2012). Hacking and Securing IOS Applications: Stealing Data, Hijacking Software, and How to Prevent It. O'Reilly Media. pp. 252–253. ISBN9781449318741.
- ^'Password Hashing Competition'
- ^ ab'Salted Password Hashing – Doing it Right'. CrackStation.net. Retrieved 29 January 2015.
- ^Abadi, Martın, T. Mark A. Lomas, and Roger Needham. 'Strengthening passwords.' Digital System Research Center, Tech. Rep 33 (1997): 1997.
- ^U. Manber, 'A Simple Scheme to Make Passwords Based on One-Way Functions Much Harder to Crack,' Computers & Security, v.15, n.2, 1996, pp.171–176.
- ^Secure Applications of Low-Entropy Keys, J. Kelsey, B. Schneier, C. Hall, and D. Wagner (1997)
- ^Morris, Robert; Thompson, Ken (3 April 1978). 'Password Security: A Case History'. Bell Laboratories. Archived from the original on 22 March 2003. Retrieved 9 May 2011.
- ^NIST SP 800-132 Section 5.1
- ^Goodin, Dan (10 September 2015). 'Once seen as bulletproof, 11 million+ Ashley Madison passwords already cracked'. Ars Technica. Retrieved 10 September 2015.
- ^Grassi Paul A (June 2017). 'SP 800-63B-3 – Digital Identity Guidelines, Authentication and Lifecycle Management'. NIST. doi:10.6028/NIST.SP.800-63b.Cite journal requires
journal=(help)
Further reading[edit]
- Percival, Colin (May 2009). 'Stronger Key Derivation via Sequential Memory-Hard Functions'(PDF). BSDCan'09 Presentation. Retrieved 19 May 2009.
In order to be able to create a digital signature, you need a private key. (Its corresponding public key will be needed in order to verify the authenticity of the signature.)
In some cases the key pair (private key and corresponding public key) are already available in files. In that case the program can import and use the private key for signing, as shown in Weaknesses and Alternatives.
In other cases the program needs to generate the key pair. A key pair is generated by using the KeyPairGenerator class.
Openpgp.js generate key pair. In this example you will generate a public/private key pair for the Digital Signature Algorithm (DSA). You will generate keys with a 1024-bit length.
Generating a key pair requires several steps:
Create a Key Pair Generator
The first step is to get a key-pair generator object for generating keys for the DSA signature algorithm.
As with all engine classes, the way to get a KeyPairGenerator object for a particular type of algorithm is to call the getInstance static factory method on the KeyPairGenerator class. This method has two forms, both of which hava a String algorithm first argument; one form also has a String provider second argument.
A caller may thus optionally specify the name of a provider, which will guarantee that the implementation of the algorithm requested is from the named provider. The sample code of this lesson always specifies the default SUN provider built into the JDK.
Put the following statement after the
line in the file created in the previous step, Prepare Initial Program Structure:
Initialize the Key Pair Generator
The next step is to initialize the key pair generator. All key pair generators share the concepts of a keysize and a source of randomness. The KeyPairGenerator class has an initialize method that takes these two types of arguments.
The keysize for a DSA key generator is the key length (in bits), which you will set to 1024.
The source of randomness must be an instance of the SecureRandom class that provides a cryptographically strong random number generator (RNG). For more information about SecureRandom, see the SecureRandom API Specification and the Java Cryptography Architecture Reference Guide .
The following example requests an instance of SecureRandom that uses the SHA1PRNG algorithm, as provided by the built-in SUN provider. The example then passes this SecureRandom instance to the key-pair generator initialization method.
Some situations require strong random values, such as when creating high-value and long-lived secrets like RSA public and private keys. To help guide applications in selecting a suitable strong SecureRandom implementation, starting from JDK 8 Java distributions include a list of known strong SecureRandom implementations in the securerandom.strongAlgorithms property of the java.security.Security class. When you are creating such data, you should consider using SecureRandom.getInstanceStrong(), as it obtains an instance of the known strong algorithms.
Generate the Pair of Keys
Aes Key Generation In Java Free
The final step is to generate the key pair and to store the keys in PrivateKey and PublicKey objects.