- Digital Communication Tutorial
- Digital Communication Resources
- Selected Reading
Phase-shift keying (PSK) is a digital modulation process which conveys data by changing (modulating) the phase of a constant frequency reference signal (the carrier wave).The modulation is accomplished by varying the sine and cosine inputs at a precise time.
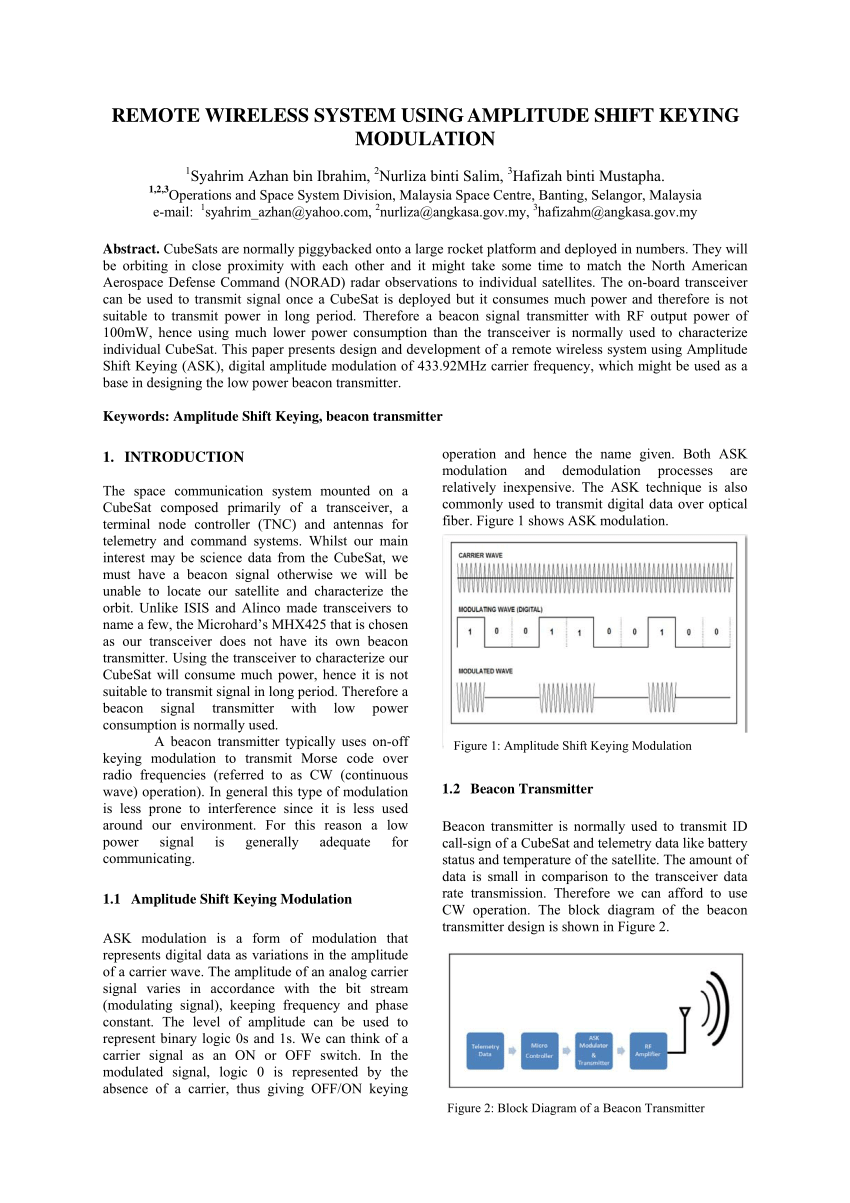
Amplitude Shift Keying (ASK) is a type of Amplitude Modulation which represents the binary data in the form of variations in the amplitude of a signal.
Any modulated signal has a high frequency carrier. The binary signal when ASK modulated, gives a zero value for Low input while it gives the carrier output for High input.
The following figure represents ASK modulated waveform along with its input.
To find the process of obtaining this ASK modulated wave, let us learn about the working of the ASK modulator.
ASK Modulator
The ASK modulator block diagram comprises of the carrier signal generator, the binary sequence from the message signal and the band-limited filter. Following is the block diagram of the ASK Modulator.
The carrier generator, sends a continuous high-frequency carrier. The binary sequence from the message signal makes the unipolar input to be either High or Low. The high signal closes the switch, allowing a carrier wave. Hence, the output will be the carrier signal at high input. When there is low input, the switch opens, allowing no voltage to appear. Hence, the output will be low.
The band-limiting filter, shapes the pulse depending upon the amplitude and phase characteristics of the band-limiting filter or the pulse-shaping filter.
ASK Demodulator
There are two types of ASK Demodulation techniques. They are −
- Asynchronous ASK Demodulation/detection
- Synchronous ASK Demodulation/detection
The clock frequency at the transmitter when matches with the clock frequency at the receiver, it is known as a Synchronous method, as the frequency gets synchronized. Otherwise, it is known as Asynchronous.
Asynchronous ASK Demodulator
The Asynchronous ASK detector consists of a half-wave rectifier, a low pass filter, and a comparator. Following is the block diagram for the same.
The modulated ASK signal is given to the half-wave rectifier, which delivers a positive half output. The low pass filter suppresses the higher frequencies and gives an envelope detected output from which the comparator delivers a digital output.
Synchronous ASK Demodulator
Synchronous ASK detector consists of a Square law detector, low pass filter, a comparator, and a voltage limiter. Following is the block diagram for the same.
The ASK modulated input signal is given to the Square law detector. A square law detector is one whose output voltage is proportional to the square of the amplitude modulated input voltage. The low pass filter minimizes the higher frequencies. The comparator and the voltage limiter help to get a clean digital output.
| Analog modulation |
|---|
| Digital modulation |
| Hierarchical modulation |
| Spread spectrum |
| See also |
Amplitude-shift keying (ASK) is a form of amplitude modulation that represents digitaldata as variations in the amplitude of a carrier wave.In an ASK system, the binary symbol 1 is represented by transmitting a fixed-amplitude carrier wave and fixed frequency for a bit duration of T seconds. If the signal value is 1 then the carrier signal will be transmitted; otherwise, a signal value of 0 will be transmitted.
Any digital modulation scheme uses a finite number of distinct signals to represent digital data. ASK uses a finite number of amplitudes, each assigned a unique pattern of binary digits. Usually, each amplitude encodes an equal number of bits. Each pattern of bits forms the symbol that is represented by the particular amplitude. The demodulator, which is designed specifically for the symbol-set used by the modulator, determines the amplitude of the received signal and maps it back to the symbol it represents, thus recovering the original data. Frequency and phase of the carrier are kept constant.
Like AM, an ASK is also linear and sensitive to atmospheric noise, distortions, propagation conditions on different routes in PSTN, etc. Both ASK modulation and demodulation processes are relatively inexpensive. The ASK technique is also commonly used to transmit digital data over optical fiber. For LED transmitters, binary 1 is represented by a short pulse of light and binary 0 by the absence of light. Laser transmitters normally have a fixed 'bias' current that causes the device to emit a low light level. This low level represents binary 0, while a higher-amplitude lightwave represents binary 1.
The simplest and most common form of ASK operates as a switch, using the presence of a carrier wave to indicate a binary one and its absence to indicate a binary zero. This type of modulation is called on-off keying (OOK), and is used at radio frequencies to transmit Morse code (referred to as continuous wave operation),
More sophisticated encoding schemes have been developed which represent data in groups using additional amplitude levels. For instance, a four-level encoding scheme can represent two bits with each shift in amplitude; an eight-level scheme can represent three bits; and so on. These forms of amplitude-shift keying require a high signal-to-noise ratio for their recovery, as by their nature much of the signal is transmitted at reduced power.
ASK system can be divided into three blocks. The first one represents the transmitter, the second one is a linear model of the effects of the channel, the third one shows the structure of the receiver. The following notation is used:
- ht(f) is the carrier signal for the transmission
- hc(f) is the impulse response of the channel
- n(t) is the noise introduced by the channel
- hr(f) is the filter at the receiver
- L is the number of levels that are used for transmission
- Ts is the time between the generation of two symbols
Different symbols are represented with different voltages. If the maximum allowed value for the voltage is A, then all the possible values are in the range [−A, A] and they are given by:
the difference between one voltage and the other is:
Considering the picture, the symbols v[n] are generated randomly by the source S, then the impulse generator creates impulses with an area of v[n]. These impulses are sent to the filter ht to be sent through the channel. In other words, for each symbol a different carrier wave is sent with the relative amplitude.
Out of the transmitter, the signal s(t) can be expressed in the form:
In the receiver, after the filtering through hr (t) the signal is:
SSH stands for Secure Shell or sometimes Secure Socket Shell protocol used for accessing network services securely from a remote computer. Github generate ssh public key.
where we use the notation:
where * indicates the convolution between two signals. After the A/D conversion the signal z[k] can be expressed in the form:
In this relationship, the second term represents the symbol to be extracted. The others are unwanted: the first one is the effect of noise, the third one is due to the intersymbol interference. Norton antivirus product key generator.

If the filters are chosen so that g(t) will satisfy the Nyquist ISI criterion, then there will be no intersymbol interference and the value of the sum will be zero, so:
the transmission will be affected only by noise.
Probability of error[edit]
The probability density function of having an error of a given size can be modelled by a Gaussian function; the mean value will be the relative sent value, and its variance will be given by:
where is the spectral density of the noise within the band and Hr (f) is the continuous Fourier transform of the impulse response of the filter hr (f).
The probability of making an error is given by:
where, for example, is the conditional probability of making an error given that a symbol v0 has been sent and is the probability of sending a symbol v0.
If the probability of sending any symbol is the same, then:
If we represent all the probability density functions on the same plot against the possible value of the voltage to be transmitted, we get a picture like this (the particular case of is shown):
The probability of making an error after a single symbol has been sent is the area of the Gaussian function falling under the functions for the other symbols. It is shown in cyan for just one of them. If we call the area under one side of the Gaussian, the sum of all the areas will be: . The total probability of making an error can be expressed in the form:
We now have to calculate the value of . In order to do that, we can move the origin of the reference wherever we want: the area below the function will not change. We are in a situation like the one shown in the following picture:
it does not matter which Gaussian function we are considering, the area we want to calculate will be the same. The value we are looking for will be given by the following integral:
where is the complementary error function. Putting all these results together, the probability to make an error is:
from this formula we can easily understand that the probability to make an error decreases if the maximum amplitude of the transmitted signal or the amplification of the system becomes greater; on the other hand, it increases if the number of levels or the power of noise becomes greater.
This relationship is valid when there is no intersymbol interference, i.e. is a Nyquist function.
Amplitude Shift Keying Pdf
See also[edit]
Amplitude Shift Keying Ppt
- Frequency-shift keying (FSK)