- Ascii Armored Pgp Public Key Generator Reviews
- What Is Ascii Armored Pgp Public Key
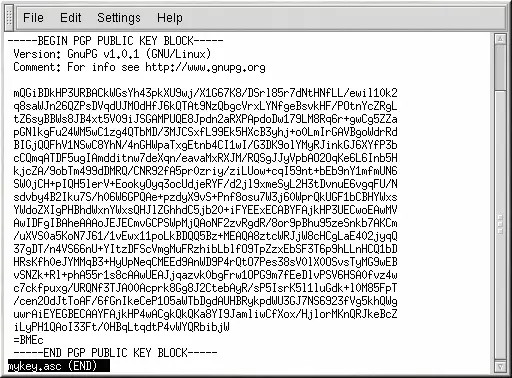
- Pgp Public Key Block
- Open PGP Studio is perfect for encrypting, decrypting, signing, and verifying documents with PGP. An integrated key manager in the product allows you to quickly create, import, export, and manage the keys you need to secure your files. You can also use it to encase encrypted documents in ASCII armor and compress output files. Ready to get started?
- Jan 08, 2014 Decrypting an ASCII armored GPG encrypted string using a private key (no passphrase) in ASCII armor format - decryptgpgarmorprivatekey.go.
- Export/Publish your public OpenPGP Key. Press Alt+F2 and run gnome-terminal; Create an ASCII armored version of your public key for exporting by typing: gpg -export -a mykey.asc; You’ve just exported your ASCII armored OpenPGP public key to the file mykey.asc in the folder you were in (your home directory, if you opened a.
A binary-to-text encoding is encoding of data in plain text. More precisely, it is an encoding of binary data in a sequence of printable characters. These encodings are necessary for transmission of data when the channel does not allow binary data (such as email or NNTP) or is not 8-bit clean. PGP documentation (RFC4880) uses the term ASCII armor for binary-to-text encoding when referring to Base64.
May 28, 2015 How to generate PGP keys using GPG 1.4.5 on Linux. Generator a better chance to gain enough entropy. Export the public key (including subkey) in ASCII format. PGP key files and encrypted files may be saved in a format referred to as ASCII armored. This format is an encrypted representation of a file consisting entirely of printable ASCII (or text-mode only) characters.
Description[edit]
The ASCII text-encoding standard uses 128 unique values (0–127) to represent the alphabetic, numeric, and punctuation characters commonly used in English, plus a selection of control codes which do not represent printable characters. For example, the capital letter A is ASCII character 65, the numeral 2 is ASCII 50, the character } is ASCII 125, and the metacharactercarriage return is ASCII 13. Systems based on ASCII use seven bits to represent these values digitally.
In contrast, most computers store data in memory organized in eight-bit bytes. Files that contain machine-executable code and non-textual data typically contain all 256 possible eight-bit byte values. Many computer programs came to rely on this distinction between seven-bit text and eight-bit binary data, and would not function properly if non-ASCII characters appeared in data that was expected to include only ASCII text. For example, if the value of the eighth bit is not preserved, the program might interpret a byte value above 127 as a flag telling it to perform some function.
It is often desirable, however, to be able to send non-textual data through text-based systems, such as when one might attach an image file to an e-mail message. To accomplish this, the data is encoded in some way, such that eight-bit data is encoded into seven-bit ASCII characters (generally using only alphanumeric and punctuation characters—the ASCII printable characters). Upon safe arrival at its destination, it is then decoded back to its eight-bit form. This process is referred to as binary to text encoding. Many programs perform this conversion to allow for limit of some SMTP software, as allowed by RFC2821.

By using a binary-to-text encoding on messages that are already plain text, then decoding on the other end, one can make such systems appear to be completely transparent.This is sometimes referred to as 'ASCII armoring'. For example, the ViewState component of ASP.NET uses base64 encoding to safely transmit text via HTTP POST,in order to avoid delimiter collision.
Encoding standards[edit]
The table below compares the most used forms of binary-to-text encodings. The efficiency listed is the ratio between number of bits in the input and the number of bits in the encoded output.
| Encoding | Data type | Efficiency | Programming language implementations | Comments |
|---|---|---|---|---|
| Ascii85 | Arbitrary | 80% | awk, C, C (2), C#, F#, Go, JavaPerl, Python, Python (2) | There exist several variants of this encoding, Base85, btoa, et cetera. |
| Base32 | Arbitrary | 62.5% | ANSI C, Java, Python | |
| Base36 | Arbitrary | ~64% | bash, C, C++, C#, Java, Perl, PHP, Python, Visual Basic, Swift, many others | Uses the Arabic numerals 0–9 and the Latin letters A–Z (the ISO basic Latin alphabet). Commonly used by URL redirection systems like TinyURL or SnipURL/Snipr as compact alphanumeric identifiers. |
| Base58 | Integer | ~73% | C++, Python | Similar to Base64, but modified to avoid both non-alphanumeric characters and letters which might look ambiguous when printed. |
| Base64 | Arbitrary | 75% | awk, C, C (2), Python, many others | |
| Base85 (RFC1924) | Arbitrary | 80% | C, PythonPython (2) | Revised version of Ascii85. |
| BinHex | Arbitrary | 75% | Perl, C, C (2) | MacOS Classic |
| Decimal | Integer | ~42% | Most languages | Usually the default representation for input/output from/to humans. |
| Hexadecimal (Base16) | Arbitrary | 50% | Most languages | Exists in uppercase and lowercase variants |
| Intel HEX | Arbitrary | ~<50% | C library, C++ | Typically used to program EPROM, NOR-Flash memory chips |
| MIME | Arbitrary | See Quoted-printable and Base64 | See Quoted-printable and Base64 | Encoding container for e-mail-like formatting |
| S-record (Motorola hex) | Arbitrary | 49.6% | C library, C++ | Typically used to program EPROM, NOR-Flash memory chips. 49.6% assumes 255 binary bytes per record. |
| Percent encoding | Text (URIs), Arbitrary (RFC1738) | ~40%[a] (33–70%[b]) | C, Python, probably many others | |
| Quoted-printable | Text | ~33–100%[c] | Probably many | Preserves line breaks; cuts lines at 76 characters |
| Uuencoding | Arbitrary | ~60% (up to 70%) | Perl, C, Java, probably many others | Largely replaced by MIME and yEnc |
| Xxencoding | Arbitrary | ~75% (similar to Uuencoding) | C | Proposed (and occasionally used) as replacement for Uuencoding to avoid character set translation problems between ASCII and the EBCDIC systems that could corrupt Uuencoded data |
| yEnc | Arbitrary, mostly non-text | ~98% | C | Includes a CRC checksum |
| RFC1751 (S/KEY) | Arbitrary | 33% | C,[1]Python, .. | 'A Convention for Human-readable 128-bit Keys'. A series of small English words is easier for humans to read, remember, and type in than decimal or other binary-to-text encoding systems.[2]Each 64-bit number is mapped to six short words, of one to four characters each, from a public 2048-word dictionary.[1]Free download photoshop cs3 key generators. |
The 95 isprint codes 32 to 126 are known as the ASCII printable characters.
Some older and today uncommon formats include BOO, BTOA, and USR encoding.
Most of these encodings generate text containing only a subset of all ASCII printable characters: for example, the base64 encoding generates text that only contains upper case and lower case letters, (A–Z, a–z), numerals (0–9), and the '+', '/', and '=' symbols.
Some of these encoding (quoted-printable and percent encoding) are based on a set of allowed characters and a single escape character. The allowed characters are left unchanged, while all other characters are converted into a string starting with the escape character. This kind of conversion allows the resulting text to be almost readable, in that letters and digits are part of the allowed characters, and are therefore left as they are in the encoded text.These encodings produce the shortest plain ASCII output for input that is mostly printable ASCII.
Some other encodings (base64, uuencoding) are based on mapping all possible sequences of six bits into different printable characters. Since there are more than 26 = 64 printable characters, this is possible. A given sequence of bytes is translated by viewing it as stream of bits, breaking this stream in chunks of six bits and generating the sequence of corresponding characters. The different encodings differ in the mapping between sequences of bits and characters and in how the resulting text is formatted.
Ascii Armored Pgp Public Key Generator Reviews
Some encodings (the original version of BinHex and the recommended encoding for CipherSaber) use four bits instead of six, mapping all possible sequences of 4 bits onto the 16 standard hexadecimal digits.Using 4 bits per encoded character leads to a 50% longer output than base64, but simplifies encoding and decoding—expanding each byte in the source independently to two encoded bytes is simpler than base64's expanding 3 source bytes to 4 encoded bytes.
Out of PETSCII's first 192 codes, 164 have visible representations when quoted: 5 (white), 17–20 and 28–31 (colors and cursor controls), 32–90 (ascii equivalent), 91–127 (graphics), 129 (orange), 133–140 (function keys), 144–159 (colors and cursor controls), and 160–192 (graphics).[3] This theoretically permits encodings, such as base128, between PETSCII-speaking machines.
Notes[edit]
What Is Ascii Armored Pgp Public Key
- ^For arbitrary data; encoding all 189 non-unreserved characters with three bytes, and the remaining 66 characters with one.
- ^For text; only encoding each of the 18 reserved characters.
- ^One byte stored as =XX. Encoding all but the 94 characters which don't need it (incl. space and tab).
References[edit]
- ^ abRFC1760 'The S/KEY One-Time Password System'.
- ^RFC1751'A Convention for Human-Readable 128-bit Keys'
- ^http://sta.c64.org/cbm64pet.html et al