Cryptographic Key Generation From Fingerprint 4,5/5 9067 reviews
- H Choi, K Choi, J Kim, “Fingerprint Matching Incorporating Ridge Features With Minutiae,” IEEE Transactions on Information Forensics and Security, vol. 6, pp. 338–345, 2011.Google Scholar
- A. K. S. Li, “Fingerprint Combination for Privacy Protection,” IEEE Transactions on Information Forensics and Security, vol. 8, pp. 350–360, 2013.Google Scholar
- A Nagar, K. Nandakumar, A Jain, “Multibiometric Cryptosystems Based on Feature-Level Fusion,” IEEE Transactions on Information Forensics and Security, vol. 7, pp. 255–268, 2012.Google Scholar
- M. Upmanyu, A. Namboodiri, K. Srinathan, C. Jawahar, “Blind Authentication: A Secure Crypto-Biometric Verification Protocol,” IEEE Transactions on Information Forensics and Security, vol. 5, pp. 255–268, 2010.Google Scholar
- A. Jain, K Nandakumar, “Biometric authentication: System security and user privacy,” Computer, vol. 45(11), pp. 87–92, Nov. 2012.Google Scholar
- D. Stinson, Crypto. Theory and Practice, 2, Ed. CRC Press, 1995.Google Scholar
- “NIST Special Database 4 (Fingerprint),” Dec. 2013. [Online]. Available: http://www.nist.gov/srd/nistsd4.cfm
- FVC2004 Fingerprint Databases. [Online]. Available: http://bias.csr.unibo.it/fvc2004/Downloads
- F. Hao, R. Anderson, J. Daugman, “Combining Crypto with Biometrics Effectively,” IEEE TC, vol. 55, no. 9, pp. 1081–1088, 2006.Google Scholar
- K. Martin, H. Lu, F. Bui, N. Konstantinos, D. Hatzinakos, “A Biometric Encryption System for the Self-Exclusion Scenario of Face Reco.” IEEE SJ., vol. 3, no. 4, pp. 440–450, Dec. 2009.Google Scholar
- K. Nandakumar, A. Jain, S. Pankanti, “Fingerprint-Based Fuzzy Vault: Implementation and Performance,” IEEE Transactions on Information Forensics and Security, vol. 2, no. 4, pp. 744–757, Dec. 2007.Google Scholar
- W. Sheng, G. Howells, M. Fairhurst, and F. Deravi, “Template-Free Biometric-Key Generation by Means of Fuzzy Genetic Clustering,” IEEE Transactions on Information Forensics and Security, vol. 3, no. 2, pp. 183–191, 2008.Google Scholar
- Y. Lee, K. Park, S. Lee, K. Bae, J. Kim, “A new method for generating an invariant iris private key based on the fuzzy vault sys.” IEEE Trans. on Sys. Man and Cybernetics, vol. 38, no. 5, pp. 1302–1313, Oct. 2008.Google Scholar
- L. Eryun, Z. Heng, L. Jimin, P. Liaojun, X. Min, C. Hongtao, L. Yanhua, L. Peng, T. Jie, “A key binding system based on n-nearest minutiae structure of fingerprint,” Pattern Recognition Letters (Elsevier), vol. 32, pp. 666–675, 2011.Google Scholar
- L. Peng, X. Yang, K. Cao, X. Tao, “An alignment-free fingerprint cryptosystem based on fuzzy vault scheme,” Journal of Network and Computer Appl. (Elsevier), vol. 33, pp. 207–220, 2010.Google Scholar

Cryptographic Key Management
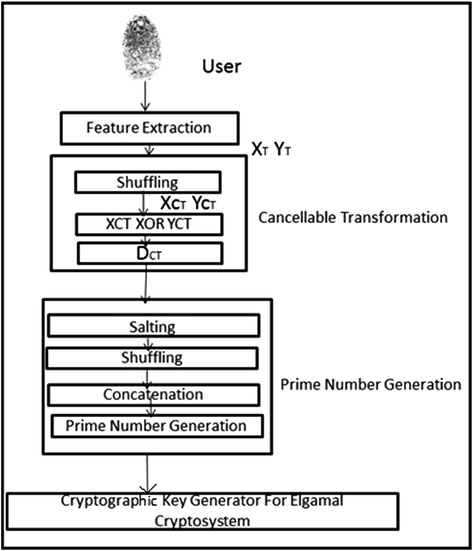
The proposed approach is composed of three modules namely, 1) Feature extraction, 2) Multimodal biometric template generation and 3) Cryptographic key generation. Mediafire download key doesn't generate file. Initially, the features, minutiae points and texture properties are extracted from the fingerprint and iris images respectively.
