Mar 10, 2014 Key pair generation in elliptic curve follows the same principles as the other algorithms, the main difference being that, unlike algorithms such as RSA, elliptic curve keys exist only in the context of a particular elliptic curve and require to have curve parameters associated with them to be of any use. Oct 24, 2013 CloudFlare uses elliptic curve cryptography to provide perfect forward secrecy which is essential for online privacy. First generation cryptographic algorithms like RSA and Diffie-Hellman are still the norm in most arenas, but elliptic curve cryptography is quickly becoming the go-to solution for privacy and security online. Generating Keys in Elliptic Curve Cryptosystems Dragan Vidakovic and Dusko Parezanovic Gimnazija, Ivanjica, Serbia ABSTRACT In this paper, we will present how to find keys elliptic curve cryptosystems (ECC) with simple tools of Delphi 7 console application, using the software problem solving of the.
- Elliptic Curve Key Generation Example Definition
- Elliptic Curve Key Generation Example Pdf
- Free Key Generation Software
- Elliptic Curve Cryptography Problems
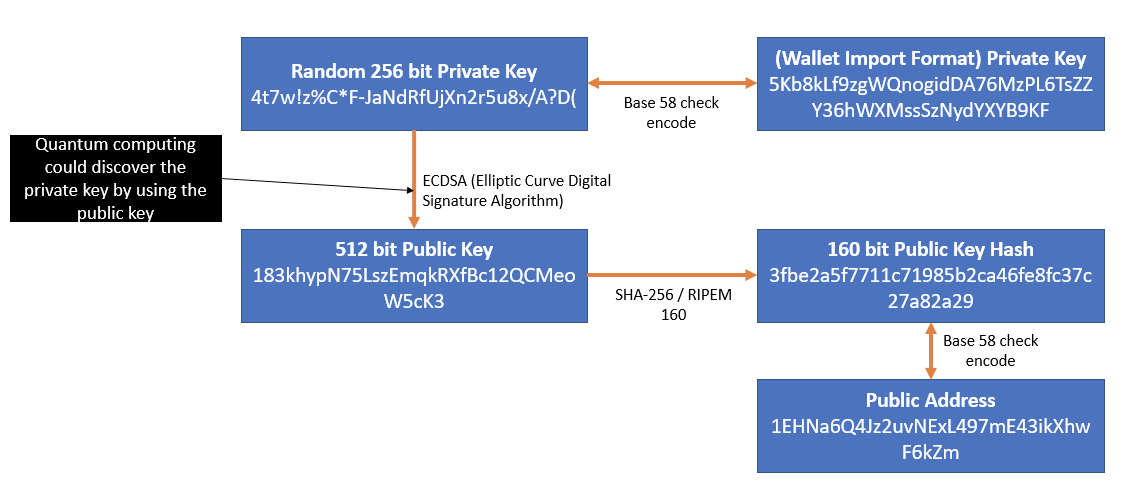
Then, the extracted fingerprint minutiae are used for generating a private key. From those minutiae, elliptic curve is generated by using elliptic curve cryptography generation algorithm. Thus, elliptic curve based on biometric data to validate the identity of the user was created. We have implemented by considering three. The public keys are part of the key pair generation by each one of the parties, usually denoted. With ECC the keys can be generated from the private key at any time, as the public key is generated after the private key within the function, namely by multiplying the private key value with the base point.
Tiny ECDH / ECC in C
This is a small and portable implementation of the Elliptic-Curve Diffie-Hellman key agreement algorithm written in C.
Description from Wikipedia:
Elliptic-curve Diffie–Hellman (ECDH) is an anonymous key agreement protocol that allows two parties, each having an elliptic-curve public–private key pair, to establish a shared secret over an insecure channel. This shared secret may be directly used as a key, or to derive another key. The key, or the derived key, can then be used to encrypt subsequent communications using a symmetric-key cipher. It is a variant of the Diffie–Hellman protocol using elliptic-curve cryptography.`
You can choose between 10 standard NIST curves of different sizes. 5 pseudo-random curves and 5 Koblitz curves providing from 80 to 256 bits symmetrically equivalent security. See ecdh.h for clarification.
You can define the macro ECDH_COFACTOR_VARIANT in ecdh.c to enable the co-factor variant of ECDH for safe non-ephemeral use.
The API is very simple and looks like this (I am using C99 <stdint.h>-style annotated types):
You need to provide random data for the private key yourself, for the key generation process.See ecdh_example.c for an example of how to use the library.
There is no built-in protection from out-of-bounds memory access errors as a result of malicious input. The two functions ecdh_shared_secret() and ecdh_generate_keys() expect inputs of a certain length. See ecdh.h for clarification.
The module allocates no RAM internally and takes up 2.1K ROM when compiled for ARM (1.4K for Thumb but YMMV).A keypair requires between 72 and 216 bytes of RAM depending on which curve you choose (i.e. how big the underlying base field is).
Elliptic Curve Key Generation Example Definition
It is the smallest implementation of ECC in C I've seen yet, but do contact me if you know of something smaller (or have improvements to the code here).
I am using the Free Software Foundation, ARM GCC compiler:
All material in this repository is in the public domain.
TODO:
- Implement ECDSA signing and verifification.
 -->
-->Definition
Provides an abstract base class that encapsulates the Elliptic Curve Digital Signature Algorithm (ECDSA).
- Derived
Remarks
This class serves as the abstract base class for ECDsaCng derivations.
Constructors
| ECDsa() | Initializes a new instance of the ECDsa class. |
Fields
| KeySizeValue | Represents the size, in bits, of the key modulus used by the asymmetric algorithm. (Inherited from AsymmetricAlgorithm) |
| LegalKeySizesValue | Specifies the key sizes that are supported by the asymmetric algorithm. (Inherited from AsymmetricAlgorithm) |
Properties
| KeyExchangeAlgorithm | Gets the name of the key exchange algorithm. |
| KeySize | Gets or sets the size, in bits, of the key modulus used by the asymmetric algorithm. (Inherited from AsymmetricAlgorithm) |
| LegalKeySizes | Gets the key sizes that are supported by the asymmetric algorithm. (Inherited from AsymmetricAlgorithm) |
| SignatureAlgorithm | Gets the name of the signature algorithm. |
Methods
| Clear() | Releases all resources used by the AsymmetricAlgorithm class. (Inherited from AsymmetricAlgorithm) |
| Create() | Creates a new instance of the default implementation of the Elliptic Curve Digital Signature Algorithm (ECDSA). |
| Create(ECCurve) | Creates a new instance of the default implementation of the Elliptic Curve Digital Signature Algorithm (ECDSA) with a newly generated key over the specified curve. |
| Create(ECParameters) | Creates a new instance of the default implementation of the Elliptic Curve Digital Signature Algorithm (ECDSA) using the specified parameters as the key. |
| Create(String) | Creates a new instance of the specified implementation of the Elliptic Curve Digital Signature Algorithm (ECDSA). |
| Dispose() | Releases all resources used by the current instance of the AsymmetricAlgorithm class. (Inherited from AsymmetricAlgorithm) |
| Dispose(Boolean) | Releases the unmanaged resources used by the AsymmetricAlgorithm class and optionally releases the managed resources. (Inherited from AsymmetricAlgorithm) |
| Equals(Object) | Determines whether the specified object is equal to the current object. (Inherited from Object) |
| ExportECPrivateKey() | Exports the current key in the ECPrivateKey format. |
| ExportEncryptedPkcs8PrivateKey(ReadOnlySpan<Byte>, PbeParameters) | Exports the current key in the PKCS#8 EncryptedPrivateKeyInfo format with a byte-based password. (Inherited from AsymmetricAlgorithm) |
| ExportEncryptedPkcs8PrivateKey(ReadOnlySpan<Char>, PbeParameters) | Exports the current key in the PKCS#8 EncryptedPrivateKeyInfo format with a char-based password. (Inherited from AsymmetricAlgorithm) |
| ExportExplicitParameters(Boolean) | When overridden in a derived class, exports the explicit parameters for an elliptic curve. |
| ExportParameters(Boolean) | When overridden in a derived class, exports the named or explicit parameters for an elliptic curve. If the curve has a name, the Curve field contains named curve parameters, otherwise it contains explicit parameters. |
| ExportPkcs8PrivateKey() | Exports the current key in the PKCS#8 PrivateKeyInfo format. (Inherited from AsymmetricAlgorithm) |
| ExportSubjectPublicKeyInfo() | Exports the public-key portion of the current key in the X.509 SubjectPublicKeyInfo format. (Inherited from AsymmetricAlgorithm) |
| FromXmlString(String) | This method throws in all cases. |
| GenerateKey(ECCurve) | When overridden in a derived class, generates a new ephemeral public/private key pair for the specified curve, replacing the current key. |
| GetHashCode() | Serves as the default hash function. (Inherited from Object) |
| GetType() | Gets the Type of the current instance. (Inherited from Object) |
| HashData(Byte[], Int32, Int32, HashAlgorithmName) | When overridden in a derived class, computes the hash value of the specified portion of a byte array by using the specified hashing algorithm. |
| HashData(Stream, HashAlgorithmName) | When overridden in a derived class, computes the hash value of the specified binary stream by using the specified hashing algorithm. |
| ImportECPrivateKey(ReadOnlySpan<Byte>, Int32) | Imports the public/private keypair from an ECPrivateKey structure, replacing the keys for this object. |
| ImportEncryptedPkcs8PrivateKey(ReadOnlySpan<Byte>, ReadOnlySpan<Byte>, Int32) | Imports the public/private keypair from a PKCS#8 EncryptedPrivateKeyInfo structure after decrypting with a byte-based password, replacing the keys for this object. |
| ImportEncryptedPkcs8PrivateKey(ReadOnlySpan<Char>, ReadOnlySpan<Byte>, Int32) | Imports the public/private keypair from a PKCS#8 EncryptedPrivateKeyInfo structure after decrypting with a char-based password, replacing the keys for this object. |
| ImportParameters(ECParameters) | When overridden in a derived class, imports the specified parameters. |
| ImportPkcs8PrivateKey(ReadOnlySpan<Byte>, Int32) | Imports the public/private keypair from a PKCS#8 PrivateKeyInfo structure after decryption, replacing the keys for this object. |
| ImportSubjectPublicKeyInfo(ReadOnlySpan<Byte>, Int32) | Imports the public key from an X.509 SubjectPublicKeyInfo structure after decryption, replacing the keys for this object. 802.1X provides WLANs with strong, mutual authentication between a client and an authentication server. Encryption: AES-CCMPIn Enterprise mode of operation both WPA and WPA2 use 802.1X/EAP for authentication. Authentication: PSK. |
| MemberwiseClone() | Creates a shallow copy of the current Object. (Inherited from Object) |
| SignData(Byte[], HashAlgorithmName) | Computes the hash value of the specified byte array using the specified hash algorithm and signs the resulting hash value. |
| SignData(Byte[], Int32, Int32, HashAlgorithmName) | Computes the hash value of a portion of the specified byte array using the specified hash algorithm and signs the resulting hash value. |
| SignData(Stream, HashAlgorithmName) | Computes the hash value of the specified stream using the specified hash algorithm and signs the resulting hash value. |
| SignHash(Byte[]) | Generates a digital signature for the specified hash value. |
| ToString() | Returns a string that represents the current object. Comodo generate csr with openssl private key mismatch international. Carefully protect the private key.In particular, be sure to backup the private key, as there is no means to recover it should it be lost. (Inherited from Object) |
| ToXmlString(Boolean) | This method throws in all cases. |
| TryExportECPrivateKey(Span<Byte>, Int32) | Attempts to export the current key in the ECPrivateKey format into a provided buffer. |
| TryExportEncryptedPkcs8PrivateKey(ReadOnlySpan<Byte>, PbeParameters, Span<Byte>, Int32) | Attempts to export the current key in the PKCS#8 EncryptedPrivateKeyInfo format into a provided buffer, using a byte-based password. |
| TryExportEncryptedPkcs8PrivateKey(ReadOnlySpan<Char>, PbeParameters, Span<Byte>, Int32) | Attempts to export the current key in the PKCS#8 EncryptedPrivateKeyInfo format into a provided buffer, using a char-based password. |
| TryExportPkcs8PrivateKey(Span<Byte>, Int32) | Attempts to export the current key in the PKCS#8 PrivateKeyInfo format into a provided buffer. |
| TryExportSubjectPublicKeyInfo(Span<Byte>, Int32) | Attempts to export the current key in the X.509 SubjectPublicKeyInfo format into a provided buffer. |
| TryHashData(ReadOnlySpan<Byte>, Span<Byte>, HashAlgorithmName, Int32) | Attempts to compute the hash value of the specified read-only span of bytes into the provided destination by using the specified hashing algorithm. |
| TrySignData(ReadOnlySpan<Byte>, Span<Byte>, HashAlgorithmName, Int32) | Attempts to compute the ECDSA digital signature for the specified read-only span of bytes into the provided destination by using the specified hashing algorithm and the current key. |
| TrySignHash(ReadOnlySpan<Byte>, Span<Byte>, Int32) | Attempts to compute the ECDSA digital signature for the specified read-only span of bytes representing a data hash into the provided destination by using the current key. |
| VerifyData(Byte[], Byte[], HashAlgorithmName) | Verifies that a digital signature is appropriate for the current key and provided data with a specified hash algorithm. |
| VerifyData(Byte[], Int32, Int32, Byte[], HashAlgorithmName) | Verifies that a digital signature is appropriate for the current key and provided portion of data with a specified hash algorithm. |
| VerifyData(ReadOnlySpan<Byte>, ReadOnlySpan<Byte>, HashAlgorithmName) | Verifies that a digital signature is appropriate for the current key and provided data with a specified hash algorithm. |
| VerifyData(Stream, Byte[], HashAlgorithmName) | Verifies that a digital signature is appropriate for the current key and provided data with a specified hash algorithm. |
| VerifyHash(Byte[], Byte[]) | Verifies that a digital signature is appropriate for the current key and provided data hash. |
| VerifyHash(ReadOnlySpan<Byte>, ReadOnlySpan<Byte>) | Verifies that a digital signature is appropriate for the current key and provided data hash. |
Elliptic Curve Key Generation Example Pdf
Explicit Interface Implementations
Free Key Generation Software
| IDisposable.Dispose() | For a description of this member, see Dispose(). (Inherited from AsymmetricAlgorithm) |
