EC2 is Amazon Elastic Compute Cloud 2 is a web cloud service that enabled developers to access web scalable cloud computing more easily and provides a secure, resizable compute capacity in the cloud. It can also be used to manage storage, configure security and host virtual servers.
The Server Key
To add SSH access to an existing Amazon EC2 instance. 1) Add two additional parameters to the template to pass in the name of an existing Amazon EC2 key pair and SSH location. 2) Add the KeyName property to the Amazon EC2 instance. 3) Add port 22 and the SSH location to the ingress rules for the Amazon EC2 security group.
This service used a public key to protect and encrypt the information in the cloud and server like login authentication. When you have data stored in the cloud, a public key is used to encrypt that data, then you get a private key to be able to decrypt that data on your end. This enables users to secure their data with server keys instead of a username and password.
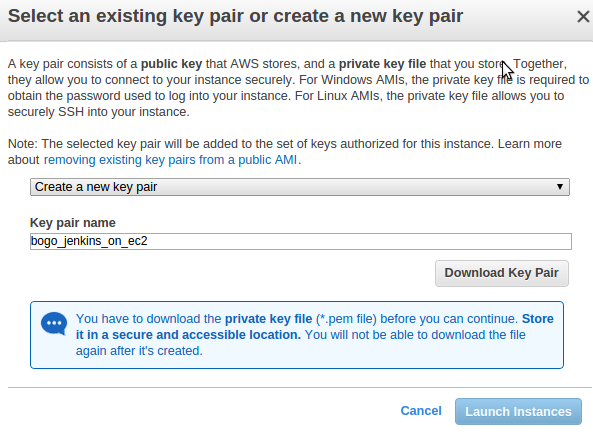
Name Your Key
The first step to creating a key pair is the name. It’s essential to give the key a name you can remember. This name will become what is associated with that particular key. The private key is your property, you can store it on your local drive or Google Docs. Whoever can access that key will also be able to access the information in the instance associated with the key. Amazon EC2 saves only the public key. Amazon EC2 supports only 2048-bit SSH-2 RSA keys and is extendable to five thousand keys in a region. An amazon key pair is created along with the instance that is being encrypted.
There are two ways to create a key for an instance. You can create indirectly at your amazon console or you can create it in your project condole and import it. To do so, log into Amazon Console. In the menu bar, select the option to choose Key Pairs and navigate to Create a key pair. Here you will be prompted to enter a name key pair. Enter a name that corresponds with the instance created for easy remembrance.
You will need to specify the File format before saving. You can either chose pem, to open with OpenSSH, or choose, ppk to open with PuTTY. When this is done, you can then save your new pair keys for that instance. Keep in mind that Amazon does not save your server keys, so it’s not possible to retrieve them from Amazon when you lose them. If you misplace or forget a key to an instance that’s not an EBS backed Linux instance, the best thing to do is delete or terminate that instance and start a new one. But if it’s Linux, then you might be able to retrieve it.
Import Your Key
Generate New Key Pair Ec2 Server
To import your public key to Amazon EC2, create an RSA key pair using a third-party platform. After this is done, you can import the key to Amazon EC2. Most of the programming languages like Python, Java, C#, C++ come with their standard libraries that enable RSA pair key generation.
EC2 only accepts keys with the following formats, OpenSSH public key format (the format in ~/.ssh/authorized_keys), SSH2 format, Base64 encoded DER format, and SSH public key file format as specified in RFC4716. It however does not support DSA Keys. The keys can have lengths between 1024, 2048, 4096, 2048 and 4096. The last two are for connected instance API.
Create Your Key
To create the key, go to the console of your third party app and type in the following:
create-key-pair
–key-name <value>
[–dry-run –no-dry-run][–cli-input-json <value>][–generate-cli-skeleton <value>]
This will create a 2048-bit RSA key pair with the specified name. Remember to put in your desired name in the Key-name attribute.
Save Your Key
For the public key, you can choose any file extension you want and then save it to a local file. The file extension of the private key is, however, important. It is recommended that you save the private key to a file location different from the public key with a .pem extension
It is very important to save the private file in a location that you won’t mistakenly delete it or it can easily assessed by third parties. You will need this key anytime you want to connect to that instance or launch it. Your private key should look something like this
“ —–BEGIN RSA PRIVATE KEY—–
EXAMPLEKEYKCAQEAy7WZhaDsrA1W3mRlQtvhwyORRX8gnxgDAfRt/gx42kWXsT4rXE/b5CpSgie/
vBoU7jLxx92pNHoFnByP+Dc21eyyz6CvjTmWA0JwfWiW5/akH7iO5dSrvC7dQkW2duV5QuUdE0QW
Z/aNxMniGQE6XAgfwlnXVBwrerrQo+ZWQeqiUwwMkuEbLeJFLhMCvYURpUMSC1oehm449ilx9X1F
G50TCFeOzfl8dqqCP6GzbPaIjiU19xX/azOR9V+tpUOzEL+wmXnZt3/nHPQ5xvD2OJH67km6SuPW
oPzev/D8V+x4+bHthfSjR9Y7DvQFjfBVwHXigBdtZcU2/wei8D/HYwIDAQABAoIBAGZ1kaEvnrqu
/uler7vgIn5m7lN5LKw4hJLAIW6tUT/fzvtcHK0SkbQCQXuriHmQ2MQyJX/0kn2NfjLV/ufGxbL1
mb5qwMGUnEpJaZD6QSSs3kICLwWUYUiGfc0uiSbmJoap/GTLU0W5Mfcv36PaBUNy5p53V6G7hXb2
bahyWyJNfjLe4M86yd2YK3V2CmK+X/BOsShnJ36+hjrXPPWmV3N9zEmCdJjA+K15DYmhm/tJWSD9
81oGk9TopEp7CkIfatEATyyZiVqoRq6k64iuM9JkA3OzdXzMQexXVJ1TLZVEH0E7bhlY9d8O1ozR
oQs/FiZNAx2iijCWyv0lpjE73+kCgYEA9mZtyhkHkFDpwrSM1APaL8oNAbbjwEy7Z5Mqfql+lIp1
YkriL0DbLXlvRAH+yHPRit2hHOjtUNZh4Axv+cpg09qbUI3+43eEy24B7G/Uh+GTfbjsXsOxQx/x
p9otyVwc7hsQ5TA5PZb+mvkJ5OBEKzet9XcKwONBYELGhnEPe7cCgYEA06Vgov6YHleHui9kHuws
ayav0elc5zkxjF9nfHFJRry21R1trw2Vdpn+9g481URrpzWVOEihvm+xTtmaZlSp//lkq75XDwnU
WA8gkn6O3QE3fq2yN98BURsAKdJfJ5RL1HvGQvTe10HLYYXpJnEkHv+Unl2ajLivWUt5pbBrKbUC
gYBjbO+OZk0sCcpZ29sbzjYjpIddErySIyRX5gV2uNQwAjLdp9PfN295yQ+BxMBXiIycWVQiw0bH
oMo7yykABY7Ozd5wQewBQ4AdSlWSX4nGDtsiFxWiI5sKuAAeOCbTosy1s8w8fxoJ5Tz1sdoxNeGs
Arq6Wv/G16zQuAE9zK9vvwKBgF+09VI/1wJBirsDGz9whVWfFPrTkJNvJZzYt69qezxlsjgFKshy
WBhd4xHZtmCqpBPlAymEjr/TOlbxyARmXMnIOWIAnNXMGB4KGSyl1mzSVAoQ+fqR+cJ3d0dyPl1j
jjb0Ed/NY8frlNDxAVHE8BSkdsx2f6ELEyBKJSRr9snRAoGAMrTwYneXzvTskF/S5Fyu0iOegLDa
NWUH38v/nDCgEpIXD5Hn3qAEcju1IjmbwlvtW+nY2jVhv7UGd8MjwUTNGItdb6nsYqM2asrnF3qS
VRkAKKKYeGjkpUfVTrW0YFjXkfcrR/V+QFL5OndHAKJXjW7a4ejJLncTzmZSpYzwApc=
—–END RSA PRIVATE KEY—– ”
When the key pair is created, use new console, old console, AWS CLI or PowerShell to import the keys to Amazon AWS. Go to Amazon EC2 to access the Amazon EC2 console and import the just created keys. Just like with creating a key pair, choose key pairs but instead of creating a new key pair, select import key pairs.
Once again, give it a name that you can easily associate with your instance. Here you can either browse through your files to select your file containing the key you can copy and paste the key contents into the Public key contents field. Also, make sure that the key pair you just imported appears in the list of key pairs. Now you have named, created, and saved your own AWS EC2 server key.
Security can be easily overlooked when building a product, especially when working with an outsourced engineering team. You want to trust them, so you give them access to your servers. But then you discover fraudulent activity, and, well, you start to panic.
In hindsight, you realize you never should have shared your Secure Shell (SSH) key, instead storing it in a vault with restricted user access. If, however, someone has a private SSH key to your Amazon Web Services (AWS) Elastic Compute Cloud (EC2) instance and you’re worried about a malicious attack, you have two options to revoke their access:
- Create a new key-pair in the AWS console and boot up a new instance (assuming the attacker is removed from IAM users). This requires configuring the instance, which can be time-consuming — especially when you have several of them.
- Replace the public key in ~/.ssh/authorized_keys on your existing instance so the attacker can no longer unlock it with their private key.
Here’s a summary of how to replace the keys mentioned in option No. Parallels 7 activation key generator mac. 2 above:
(For more, DigitalOcean has a great tutorial on setting up SSH keys.)
Generate New Key Pair Ec2 Number
- On your local machine in the terminal, generate a new key pair:
ssh-keygen -t rsa - When prompted to save the file, hit Enter for the default location or choose your own path.
- When prompted for a passphrase, you can leave the field empty. Although it does not hurt to have more security, if the key pair is used elsewhere for CI or automation, you will need to leave the passphrase empty — machines cannot guess passphrases.
- Copy the public key you just saved on your machine to your EC2 authorized keys file:
cat ~/.ssh/id_rsa.pub ssh [email protected] 'mkdir -p ~/.ssh && cat >> ~/.ssh/authorized_keyswhere ~/.ssh/id_rsa.pub is the new key on your machine and [email protected] is the username and IP address of your EC2 instance. - At this point, your new public key should be on your EC2 instance in the authorized_keys file, and all you have to do is remove the old one. Make sure you can SSH into your EC2 instance with the new key first.
- Once you’re in, you can remove the old key using
vim ~/.ssh/authorized_keysJust go to the line with the old key and remove it:ddNote: If you tried editing the file and didn’t save it, or the connection was interrupted, an .authorized_keys.swp file will be created, and the next time you try to edit your authorized_keys, you will get a nasty message. Just delete the .swp file, and you should be good to edit. - Save the file.
Generate New Key Pair Ec2 User
Make sure to update the key if you’re using it elsewhere, like on a continuous integration (CI) server. Otherwise you’ll be scratching your head when none of your builds are working.