To generate a new Key pair, run the following commands on your home computer. Open your terminal and run the following command under your username. local$ ssh-keygen -t rsa This creates a public/private keypair of the type (-t) rsa. Oct 06, 2018 Thats your SSH keys created, the private key is the idrsa and the public one is the idrsa.pub, don’t give out the private one always keep that one only on your local machine. Sharing the Public Key. Create an authorizedkeys in the.ssh directory of.
Jul 09, 2019 Can I generate a new Private Key for my Certificate if I lose the old one? It looks like a block of encoded data, starting and ending with headers, such as —–BEGIN RSA PRIVATE KEY—– and —–END RSA PRIVATE KEY—–. You may not get to see. The Keychain tool in the Server application of Mac OS X won’t allow you to access the. May 27, 2010 H ow do I generate ssh RSA keys under Linux operating systems? You need to use the ssh-keygen command as follows to generate RSA keys (open terminal and type the following command): ssh-keygen -t rsa OR ssh-keygen Sample outputs.
Avg pc tuneup 2014 product key generator. Dec 23, 2013 TuneUp Utilities 2014 - AvG PC TuneUp Utilities 2014 Crack - Duration: 10:23. Ridvan demirov 43,187 views.
Generate New Rsa Key Mac Pro
How do I generate ssh RSA keys under Linux operating systems?
You need to use the ssh-keygen command as follows to generate RSA keys (open terminal and type the following command):ssh-keygen -t rsa
ORssh-keygen
Sample outputs:
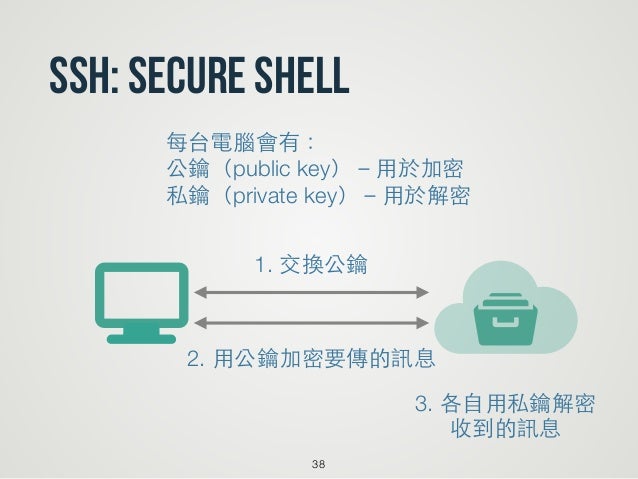
The -t type option specifies the type of key to create. The possible values “rsa†or “dsa†for protocol version 2. The $HOME/.ssh stores the following two files:
I am using blowfish-448, until now the keys have been generated usinga crypto random number generator full filling the 448bits vector.This is fine assuming your cryptographic (pseudo-) random number generator is actually good. It will (most likely) be faster and likely more secure and you won't suffer from small-block attacks like. Generate 448 bit encryption key file. If this wasn't a valid strategy, this would have produced strong warnings about using Blowfish already.I read about exploit in case of weak keys and reflection keys attack.Yes, there exist weak keys for blowfish, but hitting them when utilizing the full space has negligible probability (also it appears that they don't even break the full blowfish but rather a larger part than with normal keys).Mine concern is if the generation approach we are using is secure orif does exist a more secure way.Yes, you really should migrate off Blowfish to.
- $HOME/.ssh/id_rsa – Your private RSA key
- $HOME/.ssh/id_rsa.pub – Your public RSA key
Please do not share keys file with anyone else. You can upload keys to remote server as follows:ssh-copy-id [email protected]
Finally, you can login to remote server as follows:ssh [email protected]
scp file.txt [email protected]:~/data2/
See also:
- Howto Linux / UNIX setup SSH with DSA public key authentication (password less login)
- sshpass: Login To SSH Server / Provide SSH Password Using A Shell Script
- keychain: Set Up Secure Passwordless SSH Access For Backup Scripts
Generate Rsa Public Key
ADVERTISEMENTS