To create and use SSH keys on Windows, you need to download and install both PuTTY, the utility used to connect to remote servers through SSH, and PuTTYgen, a utility used to create SSH keys. On the PuTTY website, download the.msi file in the Package files section at the top of the page, under MSI (‘Windows Installer’). How to Generate SSH Keys on PuTTY Step 1 — Downloading PuTTYgen. Step 2 — Generating your SSH Key pair. Step 3 — Setting up your private key on PuTTY. Step 4 – Adding public key to server. Go to Windows Start menu → All Programs → PuTTY→ PuTTYgen. Creating a new key pair for Authentication. To create a new key pair, select the type of key to generate from the bottom of the screen (using SSH-2 RSA with 2048 bit key size is good for most use cases. Then click the Generate button and start moving the mouse within the Window.
To make a connection to a database more secure, some services require SSH or SSL usage.
SSL
The following procedure describes the SSL configuration that suits most databases. For some databases, you need to use another approach for a successful connection. You can see configuration examples for Cassandra and Heroku Postgres in the DataGrip documentation.
Connect to a database with SSL
In the Database tool window (View Tool Windows Database), click the Data Source Properties icon .
Select a data source profile where you want to change connection settings.
Click the SSH/SSL tab and select the Use SSL checkbox.
In the CA file field, navigate to the CA certificate file (for example, mssql.pem).
In the Client certificate file field, navigate to the client certificate file (for example, client-cert.pem).
In the Client key file field, navigate to the client key file (for example, client-key.pem).
From the Mode list, select the verification mode:
Require: verifies that the server accepts SSL connections for this IP address and recognizes the client certificate.
Verify CA: verifies the server by checking the certificate chain up to the root certificate that is stored on the client.
Full verification: verifies the server host to ensure that it matches the name stored in the server certificate. The SSL connection fails if the server certificate cannot be verified.
To ensure that the connection to the data source is successful, click Test Connection.
It is recommended to use PEM certificates.
With self-signed certificates and in some cases with certificates issued by the trusted root entity, you might experience errors when you use the latest JDBC driver version. The SSL connection might fail if your Java keystore does not accept the certificate chains. As a temporary solution, try to downgrade the JDBC driver (for example, for the MySQL connector, you need to switch to the 5.1.40 version.)
Copy SSL settings from other data sources
If you configured SSL settings for one data source, you can copy them for another data source.
In the Database tool window (View Tool Windows Database), click the Data Source Properties icon .
Select a data source profile where you want to change connection settings.
Click the SSH/SSL tab and select the Use SSL checkbox.
Click the Copy from link and select the configuration that you want to copy.
SSH
Secure Shell or SSH is a network protocol that is used to encrypt a connection between a client and a server.
All created SSH connections are shared between all the data sources that you have in a project. If you do not want to share a connection between projects, select the Visible only for this project checkbox in the SSH connection settings.
Connect to a database with SSH
In the Database tool window (View Tool Windows Database), click the Data Source Properties icon .
Select a data source profile where you want to change connection settings.
Click the SSH/SSL tab and select the Use SSH tunnel checkbox.
Click the Add SSH configuration button ().
In the SSH dialog, click the Add button.
If you do not want to share the configuration between projects, select the Visible only for this project checkbox.
In Host, User name, and Port fields, specify your connection details.
From the Auth type list, you can select an authentication method:
Password: to access the host with a password. To save the password in RubyMine, select the Save password checkbox.
It shows how to play the guitar but they lack numbers of stuff that makes it unmanageable for a passionate or professional person which keen to learn how to play the guitar. It has lots of features that guide the people to learn to play the guitar from scratch. Guitar pro 6 offline activation key generator mac.
Key pair (OpenSSH or PuTTY): to use SSH authentication with a key pair. To apply this authentication method, you must have a private key on the client machine and a public key on the remote server. RubyMine supports private keys that are generated with the OpenSSH utility.
Specify the path to the file where your private key is stored and type the passphrase (if any) in the corresponding fields. To have RubyMine remember the passphrase, select the Save passphrase checkbox.
OpenSSH config and authentication agent: to use SSH keys that are managed by a credentials helper application (for example, Pageant on Windows or ssh-agent on macOS and Linux).
Mar 31, 2011 Need for Speed Shift 2 Unleashed Keygen XxQmanxX11. Unsubscribe from XxQmanxX11? Licensed to YouTube by WMG; UNIAO BRASILEIRA DE EDITORAS DE MUSICA - UBEM, BMI.
 SHIFT 2 UNLEASHED features an all-new rendering engine with a massive graphics overhaul that puts the player in the heart of the racing action. With an all new helmet camera view simulating the physical experience of driving at 200mph, the thrilling experience of night racing and authentic degradation of tracks and cars.This is going to be the next step in simulation racing games.
SHIFT 2 UNLEASHED features an all-new rendering engine with a massive graphics overhaul that puts the player in the heart of the racing action. With an all new helmet camera view simulating the physical experience of driving at 200mph, the thrilling experience of night racing and authentic degradation of tracks and cars.This is going to be the next step in simulation racing games.
To ensure that the connection to the data source is successful, click Test Connection.
See the Generating a new SSH key and adding it to the ssh-agent tutorial for details on working with SSH keys.
Create the SSH tunnel with PuTTY (Windows)
Download and run the latest version of the PuTTY SSH and Telnet client (download the client from https://www.putty.org/).
In the PuTTY Configuration dialog, navigate to Connection SSH Auth.
In the Private key file for authentication field, specify the path to your private key file and click Open.
In the command line window, specify the username that you use for the SSH tunnel and press Enter. Do not close the command line window.
In the Database window (View Tool Windows Database), click the Data Source Properties icon on the toolbar.
Select a data source profile where you want to change connection settings.
Click the SSH/SSL tab and select the Use SSH tunnel checkbox.
From the Auth type list, select OpenSSH config and authentication agent.
In Proxy host, Proxy user, and Port fields, specify connection details.
To ensure that the connection to the data source is successful, click Test Connection.
Create the SSH tunnel with Pageant (Windows)
Pageant is an SSH authentication agent for PuTTY, PSCP, PSFTP, and Plink. Pageant stores your private key, and as long as it is running, it provides the unlocked private key to PuTTY or other tools like RubyMine. You can find the Pageant icon in the Windows taskbar.
Download the latest version of Pageant (download the client from https://www.putty.org/).
In the Windows taskbar, right-click the Pageant icon and select Add Key.
In the Select Private Key File dialog, navigate to the private key file (the PPK file) and click Open.
(Optional) Enter the private key passphrase and press Enter.
In the Database window (View Tool Windows Database), click the Data Source Properties icon on the toolbar.
Select a data source profile where you want to change connection settings.
Click the SSH/SSL tab and select the Use SSH tunnel checkbox.
From the Auth type list, select OpenSSH config and authentication agent.
In Proxy host, Proxy user, and Port fields, specify connection details.
To ensure that the connection to the data source is successful, click Test Connection.
Create the SSH tunnel with the ssh-agent (macOS and Linux)
Run all commands for ssh-agent in the command line.
Ensure that ssh-agent is running.
Add your key to the agent (in the following example, the key path is ~/.ssh/id_rsa).
ssh-add ~/.ssh/id_rsa(Optional) On macOS, you can add
-Koption to thessh-addcommand to store passphrases in your keychain. On macOS Sierra and later, you need to create the config file in ~/.ssh/ with the following text:Host *UseKeychain yesAddKeysToAgent yesIdentityFile ~/.ssh/id_rsaIf you have other private keys in the .ssh directory, add an
IdentityFileline for each key. For example, if the second key has the id_ed25519 name, addIdentityFile ~/.ssh/id_ed25519as an additional line for the second private key.List all added keys.
In the Database window (View Tool Windows Database), click the Data Source Properties icon on the toolbar.
Select a data source profile where you want to change connection settings.
Click the SSH/SSL tab and select the Use SSH tunnel checkbox.
From the Auth type list, select OpenSSH config and authentication agent.
In Proxy host, Proxy user, and Port fields, specify connection details.
To ensure that the connection to the data source is successful, click Test Connection.
3min Read
SSH keys are one of the most secure SSH authentication options. It is definitely more secure than the usual SSH password authentication. Therefore, it is highly recommended to use SSH Key authentication method for connections to your servers.
With password authentication, you can connect to your server from any location, you only need to fill in your password. However, if your password gets leaked, it is a major risk as anyone who knows your password will be able to get into the server.
SSH Key authentication only allows connections from clients whose key matches the one on the server. Basically, you generate a key pair (private key and public key). The private key is placed on your local machine and the public key is uploaded to the server. When connecting to the server, a validation of these two keys is made and if the key pair passes the validation you are allowed to connect. Of course, you can upload keys of multiple users so that you or other authorized users would be able to connect to the server from different computers.
As you can see this is a much safer connection method. In this tutorial, we will focus on Windows users who use PuTTY for connections to the server and show how to generate PuTTYSSH Keys. If you want to generate SSH Keys on Linux or Mac, see this tutorial.
What you’ll need
Before you begin this guide you’ll need the following:
- Access to your Linux server / VPS
- PuTTY and PuTTYgen installed on your computer (Download here)
Step 1 — Downloading PuTTYgen
Most of you have PuTTY installed on your computers already, however, to generate SSH Keys you also will need PuTTYgen.
- Download PuTTYgenhere
- You should be able to see this file downloaded:
No installation is required for PuTTYgen, it will run when you execute the file.
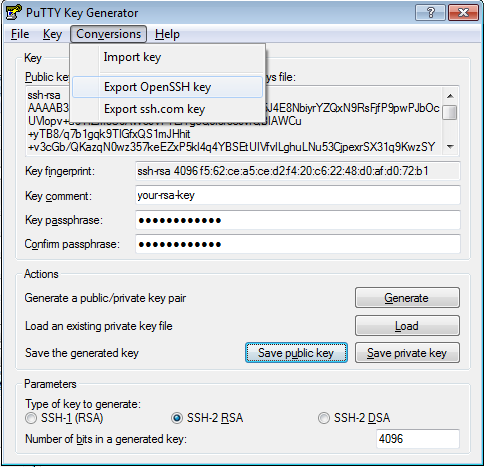
Step 2 — Generating your SSH Key pair
- Open up PuTTYgen by double clicking on the puttygen.exe file you have downloaded in Step 1.
- You should be able to see a window like this:
- Before generating your SSH Key pair, you can edit some settings, for example, key length, however, in most cases the default options will work just fine.
- Generate your SSH Key pair by clicking the Generate button.
- When the progress bar starts loading, move your mouse randomly across the area to load up the bar and generate your key pair.
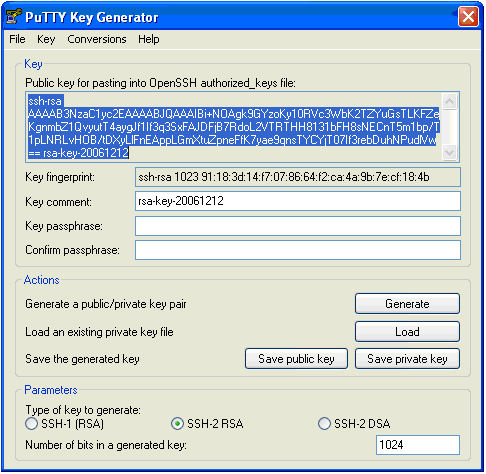
- Your public SSH key will be displayed on the screen:
- For additional security it is highly recommended to think of a passphrase for your SSH key (However, you can also leave it empty):
- Save your private key to any desired location on your computer and name it anything you like.
- Save your public key to the same location on your computer and name it anything you like.
And that is it, you have generated your SSH Key pair. The private key will stay on your computer (do not provide it to anyone) while your public key needs to be uploaded to the server you wish to connect to.
Step 3 — Setting up your private key on PuTTY
In order for the server to recognize your computer when connecting from PuTTY, you need to attach the private key to PuTTY.
- Open up PuTTY.
- Navigate to Connection -> SSH -> Auth in the left sidebar.
- Browse for your private key file in the field Private key for authentication
- Select the private key file with .ppk ending and click Open.
Step 4 – Adding public key to server
Lastly, you need to upload your public key to the server:
- On your local computer, open public key file (id_rsa.pub) you generated in Step 2 with any text editor and copy its contents (public key).
- Connect to your VPS using Putty. See this guide for detailed steps.
- If .ssh folder does not exist, create it together with authorized_keys file with the following command:
mkdir ~/.ssh touch ~/.ssh/authorized_keys - Secure SSH Key file by changing permissions:
chmod 0700 ~/.ssh; chmod 0644 ~/.ssh/authorized_keys - Open authorized_keys file with vim text editor:
vim ~/.ssh/authorized_keys - Press i key on your keyboard and right mouse button to paste the public key.
- Press Esc button and type in
:x, hit Enter button. This command will save changes made to the file.
That is it, you can now use SSH keys instead of SSH password authentication to connect to your VPS.
Conclusion
How To Generate Ssh Key Pair
You have learned how to generate PuTTY SSH Keys using PuTTYgen. This will make your connection to the server a lot more secure and convenient as you will not need to fill in the password each time. We recommend using this way of SSH authentication at all times and disable password authentication for good to completely secure your server. To find out how to completely disable SSH Password authentication on your server and use SSH Key authentication instead, follow this tutorial: How to disable SSH Password authentication on VPS.