- Create Ssh Key Git Bash Windows
- Generate Ssh Key Without Git Bash File
- Generate Ssh Key Without Git Bash Download
- List Ssh Keys Git Bash
- Generate Ssh Key Without Git Bash 2017
- Generate Ssh Key Without Git Bash Download
On Windows, you can create SSH keys in many ways. This document explains how to use two SSH applications, PuTTY and Git Bash.
Joyent recommends RSA keys because the node-manta CLI programs work with RSA keys both locally and with the ssh agent. DSA keys will work only if the private key is on the same system as the CLI, and not password-protected.
Jul 20, 2019 Welcome to my first official guide on Dev.to. Today I want to explain how you can setup SSH and Git on your Windows 10 computer. Note: This is not about 100% securing your keys but about how to generate keys for use with GitHub. Thanks to garethdd for his constructive feedback. If you're unsure whether you already have an SSH key, check for existing keys. If you don't want to reenter your passphrase every time you use your SSH key, you can add your key to the SSH agent, which manages your SSH keys and remembers your passphrase. Generating a new SSH key. Open Terminal Terminal Git Bash.
The.pub file is your public key, and the other file is your private key. If you don’t have these files (or you don’t even have a.ssh directory), you can create them by running a program called ssh-keygen, which is provided with the SSH package on Linux/Mac systems and comes with the MSysGit package on Windows. Nov 03, 2016 how to generate ssh key on windows by using git bash Yuthear THY. Unsubscribe from Yuthear THY? BitBucket - Set up SSH key pair for Git - Duration: 1:28.
PuTTY
PuTTY is an SSH client for Windows. You can use PuTTY to generate SSH keys. PuTTY is a free open-source terminal emulator that functions much like the Terminal application in macOS in a Windows environment. This section shows you how to manually generate and upload an SSH key when working with PuTTY in the Windows environment.
About PuTTY
PuTTY is an SSH client for Windows that you will use to generate your SSH keys. You can download PuTTY from www.chiark.greenend.org.uk.
When you install the PuTTY client, you also install the PuTTYgen utility. PuTTYgen is what you will use to generate your SSH key for a Windows VM.
| This page gives you basic information about using PuTTY and PuTTYgen to log in to your provisioned machine. For more information on PuTTY, see the PuTTY documentation |
|---|
Generating an SSH key
To generate an SSH key with PuTTYgen, follow these steps:
- Open the PuTTYgen program.
- For Type of key to generate, select SSH-2 RSA.
- Click the Generate button.
- Move your mouse in the area below the progress bar. When the progress bar is full, PuTTYgen generates your key pair.
- Type a passphrase in the Key passphrase field. Type the same passphrase in the Confirm passphrase field. You can use a key without a passphrase, but this is not recommended.
- Click the Save private key button to save the private key. You must save the private key. You will need it to connect to your machine.
- Right-click in the text field labeled Public key for pasting into OpenSSH authorized_keys file and choose Select All.
- Right-click again in the same text field and choose Copy.
Importing your SSH key
Now you must import the copied SSH key to the portal.
- After you copy the SSH key to the clipboard, return to your account page.
- Choose to Import Public Key and paste your SSH key into the Public Key field.
- In the Key Name field, provide a name for the key. Note: although providing a key name is optional, it is a best practice for ease of managing multiple SSH keys.
- Add the key. It will now appear in your table of keys under SSH.
PuTTY and OpenSSH use different formats of public SSH keys. If the text you pasted in the SSH Key starts with —— BEGIN SSH2 PUBLIC KEY, it is in the wrong format. Be sure to follow the instructions carefully. Your key should start with ssh-rsa AAAA….
Once you upload your SSH key to the portal, you can connect to your virtual machine from Windows through a PuTTY session.
Create Ssh Key Git Bash Windows
Git Bash
The Git installation package comes with SSH. Using Git Bash, which is the Git command line tool, you can generate SSH key pairs. Git Bash has an SSH client that enables you to connect to and interact with Triton containers on Windows.
To install Git:
- (Download and initiate the Git installer](https://git-scm.com/download/win).
- When prompted, accept the default components by clicking Next.
- Choose the default text editor. If you have Notepad++ installed, select Notepad++ and click Next.
- Select to Use Git from the Windows Command Prompt and click Next.
- Select to Use OpenSSL library and click Next.
- Select to Checkout Windows-style, commit Unix-style line endings and click Next.
- Select to Use MinTTY (The default terminal of mYSYS2) and click Next.
- Accept the default extra option configuration by clicking Install.
When the installation completes, you may need to restart Windows.
Launching GitBash
To open Git Bash, we recommend launching the application from the Windows command prompt:
- In Windows, press Start+R to launch the Run dialog.
- Type
C:Program FilesGitbinbash.exeand press Enter.
Generating SSH keys
First, create the SSH directory and then generate the SSH key pair.
One assumption is that the Windows profile you are using is set up with administrative privileges. Given this, you will be creating the SSH directory at the root of your profile, for example:
- At the Git Bash command line, change into your root directory and type.
Change into the .ssh directory
C:Usersjoetest.ssh- To create the keys, type:
- When prompted for a password, type apassword to complete the process. When finished, the output looks similar to:
Uploading an SSH key
To upload the public SSH key to your Triton account:
- Open Triton Service portal, select Account to open the Account Summary page.
- From the SSH section, select Import Public Key.
- Enter a Key Name. Although naming a key is optional, labels are a best practice for managing multiple SSH keys.
- Add your public SSH key.
When Triton finishes the adding or uploading process, the public SSH key appears in the list of SSH keys.
What are my next steps?
- Adding SSH keys to agent.
- Set up the Triton CLI and CloudAPI on Windows.
- Set up the Triton CLI and CloudAPI.
- Create an instance in the Triton Service Portal.
- Set up the
triton-dockercommand line tool. - Visit PuTTYgen to learn more about the PuTTYgen and to seethe complete installation and usage guide.
Today’s post is for developers. If you use the Git version control system with a service such as GitHub, GitLab or Bitbucket to host and manage your projects source codes, you know that by default Git connects to remotes using the HTTPS protocol, which requires you to enter username and password every time you run a command such as git pull or git push.
Using the SSH protocol, you can connect and authenticate to servers to use their services. The three mentioned services allow Git to connect via SSH instead of HTTPS. Connecting with public key encryption dispenses typing username and password for every Git command.
You are going to see in this post how to use GitHub, GitLab and Bitbucket with SSH.
Make sure an SSH client in installed
In order to connect using the SSH protocol, an SSH client must be installed on your system. If you use openSUSE, it should be already installed by default.
Just to make sure, open the terminal and run:
That command should output the version number of the SSH client being used:
In case the system informs that the ssh command was not found, you can install the OpenSSH client running:
Check for existing SSH keys
To connect using the SSH protocol, you need an SSH key pair (one private and the other public). If you have never used SSH, you can safely skip this topic and move on to the next. If you have ever used SSH (for instance, to remotely access a server), probably you already have an SSH key pair, in which case you don’t need to generate a new key pair.
To see if existing SSH keys are present, run:
That command should list the contents of the ~/.ssh folder, in which the SSH client stores its configuration files:
If you receive an error that there is no ~/.ssh directory or there are no files in it, don’t worry: it means you haven’t created an SSH key pair yet. If that is the case, proceed to the next topic.
By default, public SSH keys are named:
- id_dsa.pub;
- id_ecdsa.pub;
- id_ed25519.pub; or
- id_rsa.pub.
Inside my ~/.ssh folder, I have an SSH key pair (id_rsa.pub is the public key and id_rsa is the private key) created a year ago (Jul 18 2018).
For security reasons, it is recommended that you generate a new SSH key pair at least once a year. If you already have an SSH key pair that was created more than a year ago, it is recommended that you proceed to the next topic.
If you already have an SSH key pair and want to reuse it, you can skip the next topic.
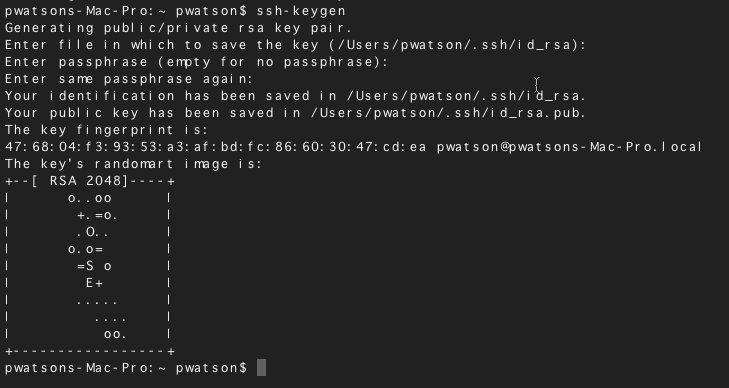
Generate a new SSH key pair
To generate a new SSH key pair, run the following command (replace [email protected] with your email address):
It asks you where to save the private key (id_rsa).
Press Enter to accept the default location.
If you already have a private key, it asks whether it should overwrite:
If that happens, type y and press Enter.
Then, enter and re-enter a passphrase (think of it as a kind of password):
The SSH key pair is created in ~/.ssh.
The whole interaction should look similar to the following:
Add the private SSH key to the ssh-agent
If you don’t want to type your passphrase each time you use your SSH keys, you need to add it to the ssh-agent, which is a program that runs in background while you are logged in to the system and stores your keys in memory.
To start the ssh-agent in background, run the following:
That command outputs the ssh-agentprocess identifier:
Then, add your SSH private key to the ssh-agent:
Type your passphrase and press Enter:
The command confirms that the private SSH key has been added to the ssh-agent:
Add the public SSH key to your account
Once you have an SSH key and have added it to the ssh-agent, you can set up connecting via SSH. Let’s see how to do that for each of the three servers: GitHub, GitLab and Bitbucket.
In all the three cases, the process is similar. Start by copying your public SSH key (~/.ssh/id_rsa.pub) file contents to the clipboard using the xclip command:
xclip is a command line utility that allows access to the graphical interface clipboard from the terminal. If it is not installed, you can install it running:
GitHub
Using a browser, go to the GitHub home page at github.com and sign in to your account.
In the upper-right corner of the page, click your profile photo, then click Settings:
In the user settings sidebar, click SSH and GPG keys. Then click New SSH key.
Fill in the Title field with a descriptive label for the new key (for example, the name of your computer) and paste your public key into the Key field. Finally, click Add SSH key:
Camtasia 2 mac key generator. Now the key appears in the list of SSH keys associated with your account:
GitLab
Using a browser, go to the GitLab home page at gitlab.com and sign in to your account.
In the upper-right corner of the page, click your profile photo, then click Settings:
In the User Settings sidebar, click SSH Keys.
Paste your public key in the Key field. Fill in the Title field with a descriptive label for the new key (for example, the name of your computer). Finally, click Add key:
Now the key appears in the list of SSH keys associated with your account:
Bitbucket
Using a browser, go to the Bitbucket home page at bitbucket.org and log in to your account.
In the lower-left corner of the page, click your profile photo, then click Bitbucket settings:
In the Settings sidebar, in the Security section, click SSH keys. Then, click Add key.
Fill in the Label field with a descriptive label for the new key (for example, the name of your computer) and paste your public key into the Key field. Finally, click Add key:
Now the key appears in the list of SSH keys associated with your account:
Test connecting via SSH
GitHub, GitLab and Bitbucket allow you to test whether SSH connection has been set up correctly before actually using it with Git.
GitHub
After you’ve added your SSH key to your GitHub account, open the terminal and run:
That command attempts an SSH remote access to GitHub.
If that is the first time you connect to GitHub via SSH, the SSH client asks you if it can trust the public key of the GitHub server:
Type yes and press Enter. The SSH client adds GitHub to the list of trusted hosts:
Once added to the list of known hosts, you won’t be asked about GitHub’s public key again.
As this remote access via SSH is provided by GitHub just for testing, not for actual use, the server informs that you have successfully authenticated and terminates the connection:
If you completed the test successfully, now you can use SSH with GitHub.
The whole interaction should look similar to the following:
GitLab
If you have added your SSH key to your GitLab account, the test is very similar:
If you completed the test successfully, now you can use SSH with GitLab.
Bitbucket
If you have added your SSH key to your Bitbucket account, the test is very similar:
If you completed the test successfully, now you can use SSH with Bitbucket.
Clone a repository using SSH
Now that we’ve got our SSH keys set up, let’s see how to clone a Git repository using SSH instead of HTTPS.
GitHub
At GitHub, go to a project’s repository, click Clone or download and copy the URL to clone the repository using SSH:
Generate Ssh Key Without Git Bash File
The URL of a GitHub repository looks like:
Open the terminal and run the git clone command passing the copied URL as argument.
Tip: to paste into the terminal, use Ctrl + Shift + V.
Note that now Git clones the repository without asking for a password:
GitLab
At GitLab, go to a project’s repository, click Clone and copy the URL to clone the repository using SSH:
The URL of a GitLab repository looks like:
Open the terminal and run the git clone command passing the copied URL as argument:
Note that now Git clones the repository without asking for a password.
Bitbucket
At Bitbucket, go to a project’s repository, click Clone and copy the command to clone the repository using SSH:
Note that, differently from GitHub and GitLab that present the URL, Bitbucket presents the entire git clone command, including the URL.
The URL of a Bitbucket repository looks like:
Generate Ssh Key Without Git Bash Download
Open the terminal, paste and run the command you copied from Bitbucket:
Note that now Git clones the repository without asking for a password.
Reconfigure existing repositories to use SSH
List Ssh Keys Git Bash
The repositories we clone from now on using SSH will continue to use SSH for future Git commands such as git pull and git push. But existing local repositories, previously cloned with HTTPS, will continue to use HTTPS, unless we set them up to use SSH.
To do that, open the terminal and change the current directory to a local repository.
List the existing remote repositories and their URLs with:
That command should output something like:
Change your remote repository’s URL with:
Run git remote -v once more to verify that the remote repository’s URL has changed:
Generate Ssh Key Without Git Bash 2017
Great. That done, Git will use SSH, instead of HTTPS, to synchronize that local repository with its remote equivalent.
Generate Ssh Key Without Git Bash Download
References
I hope those tips can be useful to you as they have been to me since I started using Git. If you have any questions or trouble, don’t hesitate to comment! See you!
And always remember: have a lot of fun…