To generate an SSH key, you will need to open Terminal.app found in 'Applications Utilities Terminal'. To create a 4096-bit RSA key pair, enter: ssh-keygen -b 4096. Generate ssh key mac 4096. Generate 4098 Bit Key Generate 4096 Bit DSA Key. RSA is very old and popular asymmetric encryption algorithm. It is used most of the systems by default. There are some alternatives to RSA like DSA. We can not generate 4096 bit DSA keys because it algorithm do not supports. Generate 2048 Bit Key. The default key size for the ssh-keygen.
Why does putty require its own key generator reviews. PuTTYgen is an key generator tool for creating SSH keys for PuTTY. It is analogous to the ssh-keygen tool used in some other SSH implementations. The basic function is to create public and private key pairs. PuTTY stores keys in its own format in.ppk files. However, the tool can also convert keys to and from other formats.
- Previously, BIND always used a fixed UDP source port when sending DNS queries. BIND used either a port configured using the query-source (and query-source-v6) directive, or one randomly chosen at startup.When a static query source port is used, TXID offers insufficient protection against spoofed replies and allows an attacker to efficiently perform cache-poisoning attacks.
- Previously, rndc.key was generated during package installation (via `rndc-confgen -a` command), but this feature was removed in RHEL 6.1 because users reported that installation of bind package sometimes hung due to lack of entropy in /dev/random.
Rndc Key Bind
The rndc.key file defines a default command channel and authentication key allowing rndc to communicate with named on the local host with no further configuration. Running rndc-confgen -a allows BIND 9 and rndc to be used as drop-in replacements for BIND 8 and ndc, with no changes to the existing BIND 8 named.conf file. Rndc communicates with the name server over a TCP connection, sending commands authenticated with digital signatures. In the current versions of rndc and named, the only supported authentication algorithm is HMAC-MD5, which uses a shared secret on each end of the connection. BINDには、rndcというユーティリティコマンドが含まれています。それを使用することで、ローカルホスト又はリモートホストからのnamed デーモンのコマンドライン管理ができるようになります。. Namedデーモンへの権限のないアクセス防止するために、BIND は共有秘密鍵認証方法.
My problem is that the bind service will always go and create /etc/rndc.key regardless of whether there is an rndc.conf in place. This then generates a warning everytime I invoke an rndc command ..Generating Etc Rndc.key Bind Key
# rndc reload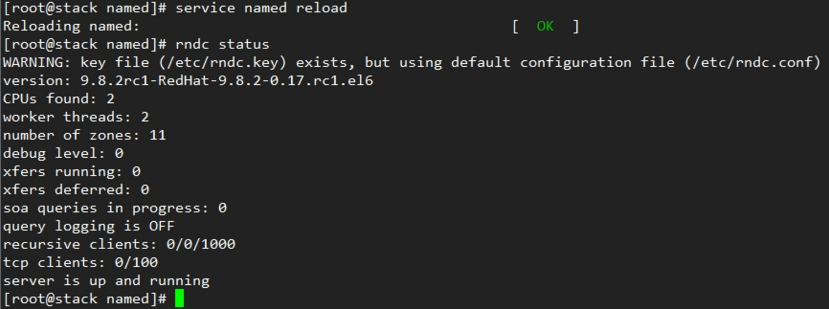
Bind Generate Rndc Key
WARNING: key file (/etc/rndc.key) exists, but using default configuration file (/etc/rndc.conf)Is there any way to stop this? In CentOS 6 I just modified the init script but before I go modifying systemd services in 7, I want to be sure there isn't a more sensible way to do it.