- Keygenerator.getinstance Algorithm Generate Key Codes
- Keygenerator.getinstance Algorithm Generate Key Generator
- Keygenerator.getinstance Algorithm Generate Key Code
- Keygenerator.getinstance Algorithm Generate Key File
“There is some good in this world, and it’s worth fighting for.” ― J.R.R. Tolkien, The Two Towers
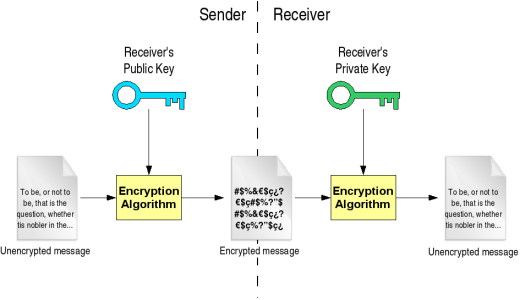
Symmetric key algorithms tend to be be much faster than asymmetric key algorithms. In addition, as you saw in the first tip, the size of the text that can be encrypted depends on the size of the product of the two primes used to generate the public and private keys.
Contents
- Conclusion
1. Introduction
A Message Authentication Code or a MAC provides a way to guarantee that a message (a byte array) has not been modified in transit. It is similar to a message digest to calculate a hash, but uses a secret key so that only a person with the secret key can verify the authenticity of the message.
Using a MAC to ensure safe transmission of messages requires that the two parties share a secret key to be able to generate and verify the MAC. There are two approaches available here – the two parties can share a secret key directly. Or the secret key can be generated using a password. We investigate both approaches below.
2. Java Imports
The following java imports are required.
3. Generating a Key
Let us now look into generating a secret key that the parties exchanging messages can share. Either party can generate the key as shown here and send it to the other party via a secure channel.
The following KeyGenerator algorithms are supported in my version of java. Of these, ones starting with HMAC are useful as a secret key for a MAC.
Unrar the maps into your haloce/maps directory. Put it in your Halo Custom Edition game Directory and run the patch from there 4. Halo ce cd key. Download Halo CE here and install 3.
4. Saving and Restoring a Key
You will need to send the key to the receiver to enable verification. So you need to be able to save and restore the key. Here is how you can save it to a file.
And restoring the key is also quite simple.
Keygenerator.getinstance Algorithm Generate Key Codes
5. Generating the Message Authentication Code (MAC)
Keygenerator.getinstance Algorithm Generate Key Generator
Once you generate the key, you can proceed with generating the MAC for a message.
Use one of the following values for the algorithm (algo):
The static method processFile() is defined as follows:
Once the MAC is obtained, you can send it to the other party along with the file for verification.
6. Using a Password for Key Generation
While one way of generating a secret key is to directly use a KeyGenerator as shown above, sometimes it is more convenient to use a password to generate the key. This can be accomplished using a SecretKeyFactory.
Keygenerator.getinstance Algorithm Generate Key Code
One aspect of using a password for key generation is that it requires the use of a salt. This salt can be generated using the SecureRandom class while generating the key, but the same salt must be used again for verification. This means the salt also must be communicated to the message receiver, but it need not be kept secret – it can be transmitted as plain-text.
The following code generates and prints the salt for transmission.
Keygenerator.getinstance Algorithm Generate Key File
And now for the generation of the secret key.
Use one of the following values for the algorithm (algo):
Once you have the SecretKey, the procedure for computing the MAC is the same as above. However, you will need to use one of the following algorithms:
Parallel desktop 12 activation key generator. More, the screen catch is likewise empowered and you can record the screen of your PC.Parallels Desktop Serial Key for Mac is likewise perfect with numerous other working frameworks.
Conclusion
In this article, we learned how to compute a MAC (Message Authentication Code) for a message. A MAC requires a secret key which needs to be shared among the parties in the exchange. A password can be used for generating the secret key too.
 This class provides the functionality of a secret (symmetric) key generator.
This class provides the functionality of a secret (symmetric) key generator. Key generators are constructed using one of the getInstance class methods of this class.
KeyGenerator objects are reusable, i.e., after a key has been generated, the same KeyGenerator object can be re-used to generate further keys.
There are two ways to generate a key: in an algorithm-independent manner, and in an algorithm-specific manner. The only difference between the two is the initialization of the object:
- Algorithm-Independent Initialization
All key generators share the concepts of a keysize and a source of randomness. There is an
initmethod in this KeyGenerator class that takes these two universally shared types of arguments. There is also one that takes just akeysizeargument, and uses the SecureRandom implementation of the highest-priority installed provider as the source of randomness (or a system-provided source of randomness if none of the installed providers supply a SecureRandom implementation), and one that takes just a source of randomness.Since no other parameters are specified when you call the above algorithm-independent
initmethods, it is up to the provider what to do about the algorithm-specific parameters (if any) to be associated with each of the keys. - Algorithm-Specific Initialization
For situations where a set of algorithm-specific parameters already exists, there are two
initmethods that have anAlgorithmParameterSpecargument. One also has aSecureRandomargument, while the other uses the SecureRandom implementation of the highest-priority installed provider as the source of randomness (or a system-provided source of randomness if none of the installed providers supply a SecureRandom implementation).
In case the client does not explicitly initialize the KeyGenerator (via a call to an init method), each provider must supply (and document) a default initialization. See the Keysize Restriction sections of the JDK Providers document for information on the KeyGenerator defaults used by JDK providers. However, note that defaults may vary across different providers. Additionally, the default value for a provider may change in a future version. Therefore, it is recommended to explicitly initialize the KeyGenerator instead of relying on provider-specific defaults.
Every implementation of the Java platform is required to support the following standard KeyGenerator algorithms with the keysizes in parentheses:
AES(128)DES(56)DESede(168)HmacSHA1HmacSHA256