Using key file as password with OpenSSL. Ask Question Asked 6 years, 10 months ago. I know how to decrypt if the key is a passphrase by using. Openssl enc -d -aes-256-cbc -in file.out In this case, the key is a binary file. How do I use it? How do you use the AES key wrap cipher with the OpenSSL. The EVP functions support the ability to generate parameters and keys if required for EVPPKEY objects. 2) use the key generator to generate a valid serial. Since these functions use random numbers you should ensure that the random number generator is appropriately seeded as discussed here. Here is the simple “How to do AES-128 bit CBC mode encryption in c programming code with OpenSSL” First you need to download standard cryptography library called OpenSSL to perform robust AES(Advanced Encryption Standard) encryption, But before that i will tell you to take a look at simple C code for AES encryption and decryption, so that you are familiar with AES cryptography APIs which. Jun 23, 2012 The OpenSSL API differentiates between Seal & Open for encrypting with public keys and decrypting with private keys and Sign & Verify for encrypting with private keys and decrypting with public keys. Since I will eventually be dropping this in a server, I want to be encrypting with public keys so I’m using the Seal functions here.
You cannot combine auto-generated keys with batch update. In any case if it is supported by your driver than your statement prepare should be changed to the code below to instruct the driver to retrieve generated keys: ps = con.prepareStatement(insert, Statement.RETURNGENERATEDKEYS). Is there a way to get all the generated keys of a batch insert? Is there a way to get all the generated keys of a batch insert? Batch insert generated keys #487. Closed bardam opened this issue Jan 27, 2016 7 comments. It's not possible for now because JDBC Batch API returns only an array of update count. Spring jdbc batch insert. Therefore, we'll use the JDBCTemplate update method which supports the retrieval of primary keys generated by the database. This method takes an instance of the PrepareStatementCreator interface as the first argument and the other argument is the KeyHolder. With the IBM® Data Server Driver for JDBC and SQLJ, you can use JDBC 3.0 methods to retrieve the keys that are automatically generated when you execute an INSERT statement. Procedure To retrieve automatically generated keys that are generated by an INSERT statement, you need to.
Openssl C++ Generate Aes Key Size
Chilkat • HOME • Android™ • Classic ASP • C • C++ • C# • Mono C# • .NET Core C# • C# UWP/WinRT • DataFlex • Delphi ActiveX • Delphi DLL • Visual FoxPro • Java • Lianja • MFC • Objective-C • Perl • PHP ActiveX • PHP Extension • PowerBuilder • PowerShell • PureBasic • CkPython • Chilkat2-Python • Ruby • SQL Server • Swift 2 • Swift 3/4 • Tcl • Unicode C • Unicode C++ • Visual Basic 6.0 • VB.NET • VB.NET UWP/WinRT • VBScript • Xojo Plugin • Node.js • Excel • Go
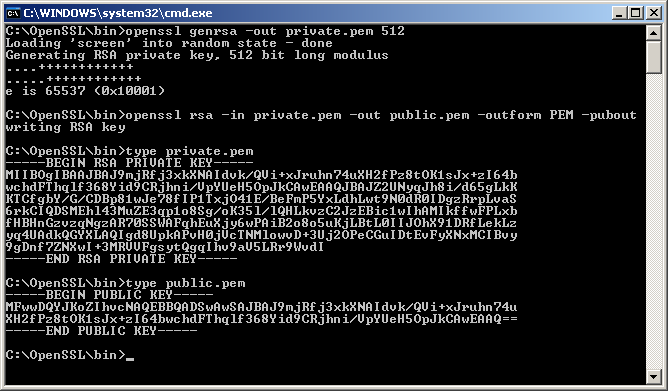
| Demonstrates how to use RSA to protect a key for AES encryption. It can be used in this scenario: You will provide your RSA public key to any number of counterparts. Your counterpart will generate an AES key, encrypt data (or a file) using it, then encrypt the AES key using your RSA public key. Your counterpart sends you both the encrypted data and the encrypted key. Since you are the only one with access to the RSA private key, only you can decrypt the AES key. You decrypt the key, then decrypt the data using the AES key. This example will show the entire process. (1) Generate an RSA key and save both private and public parts to PEM files. (2) Encrypt a file using a randomly generated AES encryption key. (3) RSA encrypt the AES key. (4) RSA decrypt the AES key. (5) Use it to AES decrypt the file or data.
| |||||
© 2000-2020 Chilkat Software, Inc. All Rights Reserved.
How to do AES decryption using OpenSSL (1)
I'd like to use the OpenSSL library to decrypt some AES data. The code has access to the key. This project already uses libopenssl for something else, so I'd like to stick to this library.
I went looking directly into /usr/include/openssl/aes.h since the OpenSSL site is light on documentation. The only decrypt function is this one:
Unfortunately, this doesn't have a way to specify the length of the in pointer, so I'm not sure how that would work.
Openssl C Generate Aes Key Generator
There are several other functions which I believe take a numeric parm to differentiate between encryption and decryption. For example:
From what I understand using Google, the enc parm gets set to AES_ENCRYPT or AES_DECRYPT to specify which action needs to take place.
Which brings me to my 2 questions:
- What do these names mean? What is ecb, cbc, cfb128, etc.., and how do I decide which one I should be using?
- What is the
unsigned char *ivecparm needed for most of these, and where do I get it from?
There's no size given because the block sizes for AES are fixed based on the key size; you've found the ECB mode implementation, which isn't suitable for direct use (except as a teaching tool).
ECB, CBC, CFB128, etc, are all short names for the modes of operation that are in common use. They have different properties, but if you never touch ECB mode, you should be alright.
I suggest staying further away from the low-level code; use the EVP_* interfaces instead, if you can, and you can move some of these decisions into a text configuration file, so your users could easily select between the different ciphers, block sizes, and modes of operation if there should ever be a good reason to change away from the defaults.
Openssl Aes 256
My sympathies, OpenSSL documentation feels worse than it is, and it isn't that great. You may find Network Security with OpenSSL a useful book. I wish I had found it sooner the last time I needed to use OpenSSL. (Don't let the silly title fool you -- it should have been titled just 'OpenSSL'. Oh well.)
Edit I forgot to mention the initialization vectors. They are used to make sure that if you encrypt the same data using the same key, the ciphertext won't be identical. You need the IV to decrypt the data, but you don't need to keep the IV secret. You should either generate one randomly for each session (and send it along with an RSA or El Gamal or DH-encrypted session key) or generate it identically on both endpoints, or store it locally with the file, something like that.