Updated by LinodeWritten by Linode
Mar 25, 2015 Showing how to make a certificate (with root CA and intermediate CA properly chained) with OpenSSL. The certificate can be used for code signing. Use my online page to generate. Jun 01, 2018 -newkey rsa:4096: Create a 4096 bit RSA key for use with the certificate. RSA 2048 is the default on more recent versions of OpenSSL but to be sure of the key size, you should specify it during creation.-x509: Create a self-signed certificate.-sha256: Generate the certificate request using 265-bit SHA (Secure Hash Algorithm).
Contribute on GitHub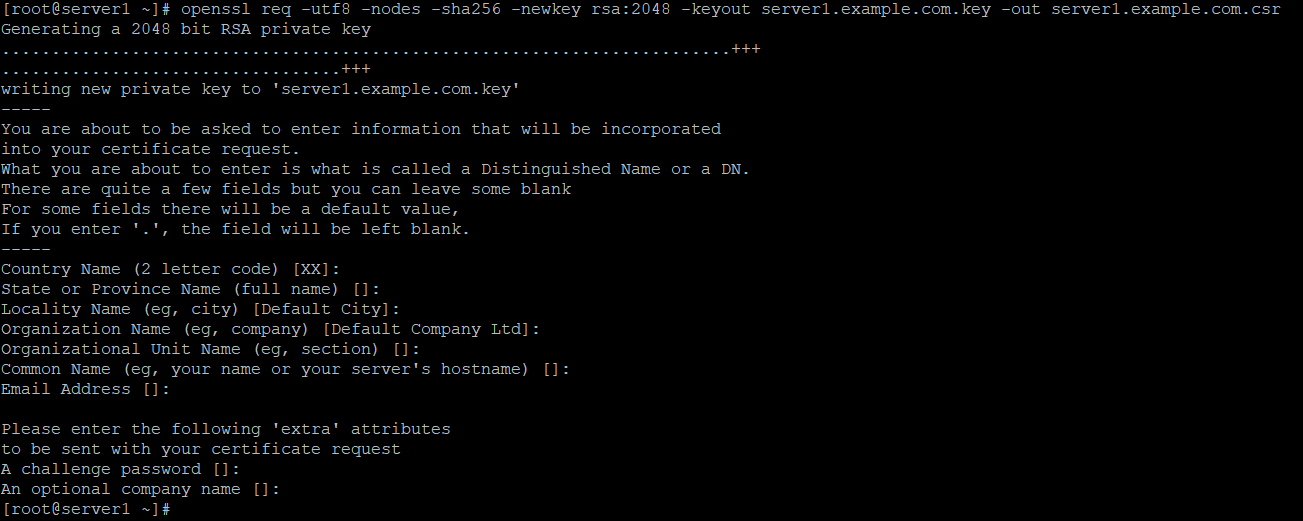
Report an Issue View File Edit File
Openssl Self Signed Certificate Linux
What is a Self-Signed TLS Certificate?
Self-signed TLS certificates are suitable for personal use or for applications that are used internally within an organization. If you intend to use your SSL certificate on a website, see our guide on enabling TLS for NGINX once you’ve completed the process outlined in this guide.
Create the Certificate
Change to the
rootuser and change to the directory in which you want to create the certificate and key pair. That location will vary depending on your needs. Here we’ll use/root/certs:Create the certificate:
You will be prompted to add identifying information about your website or organization to the certificate. Since a self-signed certificate won’t be used publicly, this information isn’t necessary. If this certificate will be passed on to a certificate authority for signing, the information needs to be as accurate as possible.
The following is a breakdown of the OpenSSL options used in this command. There are many other options available, but these will create a basic certificate which will be good for a year. For more information, see
man opensslin your terminal.-newkey rsa:4096: Create a 4096 bit RSA key for use with the certificate.RSA 2048is the default on more recent versions of OpenSSL but to be sure of the key size, you should specify it during creation.-x509: Create a self-signed certificate.-sha256: Generate the certificate request using 265-bit SHA (Secure Hash Algorithm).-days: Determines the length of time in days that the certificate is being issued for. For a self-signed certificate, this value can be increased as necessary.-nodes: Create a certificate that does not require a passphrase. If this option is excluded, you will be required to enter the passphrase in the console each time the application using it is restarted.
Here is an example of the output:
64-bit wep key length. Restrict the key’s permissions so that only
rootcan access it:Back up your certificate and key to external storage. This is an important step. Do not skip it!
Join our Community
Self Signed Certificate Iis
This guide is published under a CC BY-ND 4.0 license.
