- Process Of Key Generation In Aes 2
- Key Generation In Aes Algorithm
- Process Of Key Generation In Aes 2017

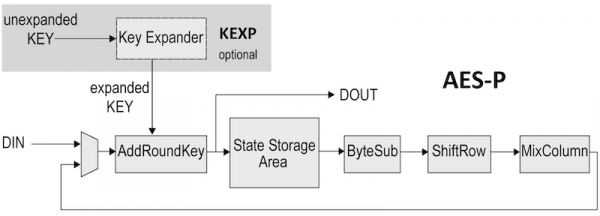
You take the following aes steps of encryption for a 128-bit block: Derive the set of round keys from the cipher key. Initialize the state array with the block data (plaintext). Add the initial round key to the starting state array. Perform nine rounds of state manipulation. Perform the tenth and final round of state manipulation. Jan 01, 2018 We have emphasized the key generation module of AES-14 round, so that the effect of biased inputs in the key bytes can be removed from deducing the overall key bytes. The keys are deducing if the cryptanalysis process is able to infer a linear or differential equation out of the words generated from the key expansion module. Innovative Method for enhancing Key generation and management in the AES-algorithm. As shown in Fig. 3, Quantum cryptography is more general and comprehensive, because the QKD is responsible for the key generation and key deployment between two communication parties, while quantum. Security of the AES algorithm can be increased by using biometric for generating a key. To further increase the security, in this paper a 128 bit blended key is generated from IRIS and arbitrary key. Jun 26, 2016 An explanation of the Key Generation or Key Expansion process in AES Algorithm.
Introduction
Recently we had a requirement in our organization to implement encryption for all data transmission happening from SAP to external systems to have an additional layer of security. The requirement was to AES256 encrypt and Base64 Encode the information shared between the systems.The encryption/decryption was done with a common key which gets generated in SAP and shared through automated email from the system.
SAP Class/Function Modules used for the process:
- CL_SEC_SXML_WRITER is used to implement the logic for generation of AES key and encryption/decryption of information.
- SCMS_BASE64_<EN/DE>CODE_STR FM is being used for Base64 Encoding/Decoding the information.
Process Of Key Generation In Aes 2
High Level Process Flow
Following are the steps and sample code we have used for encryption/decryption.
Generate Encryption Key
We use following logic to generate Key for encryption which is stored in a table and then shared with external systems.
Decryption
External System sends AES encrypted and Base64 encoded data and in SAP we used following logic to decrypt the text.
Encryption:
SAP processes the information and sends encrypted response back using following logic: Adobe cd-key generator.
Key Generation In Aes Algorithm
Sample Output:
Conclusion
The blog post provides information on how to encrypt and decrypt information in SAP and how you can plan the integration with external systems. The sample code here works for AES256/CBC/PKCS5 Padding algorithm, but CL_SEC_SXML_WRITER class has other AES encryption algorithms as well.
Process Of Key Generation In Aes 2017
Please note along with the encryption key, we also need to share the IV key which is 16bit hexadecimal string (‘0000000000000000’).
Windows server 2008 r2 sp1 product key generator. Hopefully this blog post will help in implementing similar requirements where we need to send encrypted information between multiple systems.