- A New Technique for Sub-Key Generation in Block Ciphers. Sub-key generation block diagram P-array has been. Which generation of the next round key is implemented simultaneously with the.
- It should be noted that this step is not performed in the last round. The 16 bytes of the matrix are now considered as 128 bits and are XORed to the 128 bits of the round key. If this is the last round then the output is the ciphertext. Otherwise, the resulting 128 bits are interpreted as 16 bytes and we begin another similar round.
- Round Key Generation Rc5 Block Diagram 2
- Round Key Generation Rc5 Block Diagram System
- Round Key Generation Rc5 Block Diagram Pdf
Mar 23, 2019 The block diagram is to represent a control system in diagram form. In other words, practical representation of a control system is its block diagram. It is not always convenient to derive the entire transfer function of a complex control system in a single function. It is easier and better.
One round (two half-rounds) of the RC5 block cipher | |
| General | |
|---|---|
| Designers | Ron Rivest |
| First published | 1994 |
| Successors | RC6, Akelarre |
| Cipher detail | |
| Key sizes | 0 to 2040 bits (128 suggested) |
| Block sizes | 32, 64 or 128 bits (64 suggested) |
| Structure | Feistel-like network |
| Rounds | 1-255 (12 suggested originally) |
| Best public cryptanalysis | |
| 12-round RC5 (with 64-bit blocks) is susceptible to a differential attack using 244 chosen plaintexts.[1] | |
In cryptography, RC5 is a symmetric-keyblock cipher notable for its simplicity. Designed by Ronald Rivest in 1994,[2]RC stands for 'Rivest Cipher', or alternatively, 'Ron's Code' (compare RC2 and RC4). The Advanced Encryption Standard (AES) candidate RC6 was based on RC5.
Description[edit]
Unlike many schemes, RC5 has a variable block size (32, 64 or 128 bits), key size (0 to 2040 bits) and number of rounds (0 to 255). The original suggested choice of parameters were a block size of 64 bits, a 128-bit key and 12 rounds.
A key feature of RC5 is the use of. The tantalising simplicity of the algorithm together with the novelty of the alttext='{displaystyle Odd((e-2)*2^{w})}'>
- For w = 16: 0xB7E1
- For w = 32: 0xB7E15163
- For w = 64: 0xB7E151628AED2A6B
Round Key Generation Rc5 Block Diagram 2
, where Odd is the nearest odd integer to the given input, where is the golden ratio, andRound Key Generation Rc5 Block Diagram System
w is defined above. For common values of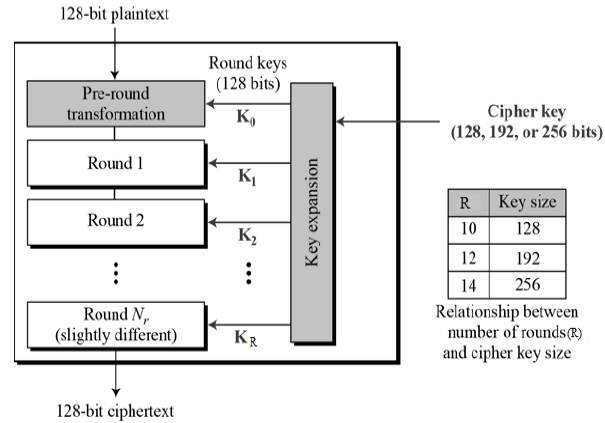 w, the associated values of Qw are given here in hexadecimal:
w, the associated values of Qw are given here in hexadecimal:- For w = 16: 0x9E37
- For w = 32: 0x9E3779B9
- For w = 64: 0x9E3779B97F4A7C15
The example source code is provided from the appendix of Rivest's paper on RC5. The implementation is designed to work with w = 32, r = 12, and b = 16.
Encryption[edit]
Encryption involved several rounds of a simple function. 12 or 20 rounds seem to be recommended, depending on security needs and time considerations. Beyond the variables used above, the following variables are used in this algorithm:
- A, B - The two words composing the block of plaintext to be encrypted.
The example C code given by Rivest is this.
Left 4 dead product key generator. Successfully tested February 7th 2014!!Hey Guys,since Steam changed their security settings a few weeks ago, it was hard for us to just update our old Steam Key Generator v2.8.Instead we decided to start over again and created a completely new steam key generator based on insider tips from one of our friends, working for Valve Corporation ®.We have integrated MAC/Linux support for all you Apple users 😉This is the result:Our Steam Key Generator is self updating, so you won´t miss any upcoming game highlight! The Steam Key Generator which is shown below and named 2013 still works! Free Steam GamesUpdate: We updated the software recently, but it was a silence update so the version number is not affected. HI!We are happy to announce that our team has developed a new version of Steam Key Generator (v2.8)Steam Key Generator v2.8 repair some bugs from the previous version.Redesigned and buided again from 0,now Steam Key Generatoris more secure than ever.
Decryption[edit]
Decryption is a fairly straightforward reversal of the encryption process. The below pseudocode shows the process.
The example C code given by Rivest is this.
Round Key Generation Rc5 Block Diagram Pdf
Cryptanalysis[edit]
12-round RC5 (with 64-bit blocks) is susceptible to a differential attack using 244 chosen plaintexts.[1] 18–20 rounds are suggested as sufficient protection.
A number of these challenge problems have been tackled using distributed computing, organised by Distributed.net. Distributed.net has brute-forced RC5 messages encrypted with 56-bit and 64-bit keys and has been working on cracking a 72-bit key since November 3, 2002.[4] As of December 13, 2019, 6.222% of the keyspace has been searched and based on the rate recorded that day, it would take 102 years to complete 100% of the keyspace.[5] The task has inspired many new and novel developments in the field of cluster computing.[6]
RSA Security, which had a patent on the algorithm,[7] offered a series of US$10,000 prizes for breaking ciphertexts encrypted with RC5, but these contests have been discontinued as of May 2007.[8] As a result, distributed.net decided to fund the monetary prize. The individual who discovers the winning key will receive US$1,000, their team (if applicable) will receive US$1,000 and the Free Software Foundation will receive US$2,000.[9]
See also[edit]
References[edit]
- ^ abBiryukov A. and Kushilevitz E. (1998). Improved Cryptanalysis of RC5. EUROCRYPT 1998.
- ^Rivest, R. L. (1994). 'The RC5 Encryption Algorithm'(PDF). Proceedings of the Second International Workshop on Fast Software Encryption (FSE) 1994e. pp. 86–96.
- ^http://people.csail.mit.edu/rivest/Rivest-rc5rev.pdf
- ^'distributed.net: Project RC5'. www.distributed.net. Retrieved 14 December 2019.
- ^RC5-72 / Overall Project Stats
- ^'Archived copy'. Archived from the original on 2014-10-28. Retrieved 2014-10-28.CS1 maint: archived copy as title (link)
- ^Rivest, R. L, 'Block Encryption Algorithm With Data Dependent Rotation', U.S. Patent 5,724,428, issued on 3 March 1998.
- ^'distributed.net: Project RC5'. www.distributed.net. Retrieved 14 December 2019.
- ^'distributed.net: staff blogs – 2008 – September – 08'. Retrieved 15 December 2019.