- Rsa Vs Dsa Key
- Rsa And Dsa Key Generation Utility Trailer
- Rsa And Dsa Key Generation Utility Download
- Rsa And Dsa Key Generation Utility Bill
| Developer(s) | The OpenBSD Project |
|---|---|
| Written in | C |
| Operating system | Unix, Unix-like, Microsoft Windows |
| Type | Command |
| License | BSD, ISC, public domain |
| Website | www.openssh.com |
Rsa Vs Dsa Key
ssh-keygen is a standard component of the Secure Shell (SSH) protocol suite found on Unix, Unix-like and Microsoft Windows computer systems used to establish secure shell sessions between remote computers over insecure networks, through the use of various cryptographic techniques. The ssh-keygen utility is used to generate, manage, and convert authentication keys.
Overview[edit]
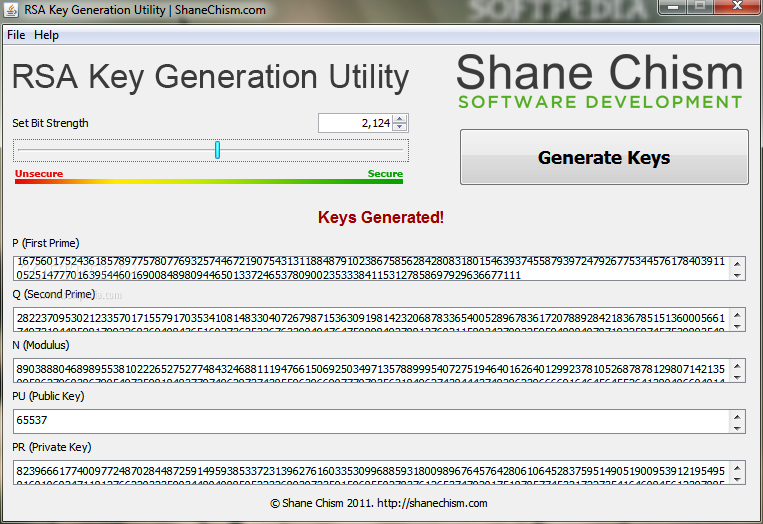
May 03, 2014 RSA Key Generation Utility is a Java-based software application that can generate RSA keys based on a user-defined set of rules. It does not feature. You can use the ssh-keygen command line utility to create RSA and DSA keys for public key authentication, to edit properties of existing keys, and to convert file formats. When no options are specified, ssh-keygen generates a 2048-bit RSA key pair and queries you for a key name and a passphrase to protect the private key.
ssh-keygen is able to generate a key using one of three different digital signature algorithms. With the help of the ssh-keygen tool, a user can create passphrase keys for any of these key types (to provide for unattended operation, the passphrase can be left empty, at increased risk). These keys differ from keys used by the related tool GNU Privacy Guard.
OpenSSH-based client and server programs have been included in Windows 10 since version 1803. The SSH client and key agent are enabled and available by default and the SSH server is an optional Feature-on-Demand.[1][2]
Key formats supported[edit]
| Protocol | Generation |
|---|---|
| RSA | 1 |
| DSA | 2 |
| ECDSA | 3 |
| ed25519 | 4 |
Originally, with SSH protocol version 1 (now deprecated) only the RSA algorithm was supported. As of 2016, RSA is still considered strong, but the recommended key length has increased over time.
The SSH protocol version 2 additionally introduced support for the DSA algorithm. As the DSA algorithm has ties to the American National Security Agency (NSA), aspects of its security have been called into question by Edward Snowden's global surveillance disclosures, particularly in light of the Bullrun decryption program.
Subsequently, OpenSSH added support for a third digital signature algorithm, ECDSA (this key format no longer uses the previous PEM file format for private keys, nor does it depend upon the OpenSSL library to provide the cryptographic implementation).
A fourth format is supported using ed25519, originally developed by independent cryptography researcher Daniel J. Bernstein.
ssh-keygen command syntax[edit]
The syntax of the ssh-keygen command is as follows:
Some important options of the ssh-keygen command are as follows:
| ssh-keygen command options | description |
|---|---|
| -b bits | Specifies the number of bits in the key to create. The minimum bit length is 1024 bits and the default length is 2048 bits. |
| -C comment | Provides new comment. |
| -p | Requests changing the passphrase of a private key file instead of creating a new private key. |
| -t | Specifies the type of key to create. |
| -o | Use the new OpenSSH format. |
| -q | quiets ssh-keygen. It is used by the /etc/rc file while creating a new key. |
| -N | Provides a new Passphrase. |
| -F (or -B) | For ssh-keygen2, dumps the key's fingerprint in Bubble Babble format |
Files used by the ssh-keygen utility[edit]
The ssh-keygen utility uses various files for storing public and private keys. The files used by ssh-keygen utility are as follows:
- $HOME/.ssh/identity: The $HOME/.ssh/identity file contains the RSA private key when using the SSH protocol version 1.
- $HOME/.ssh/identity.pub: The $HOME/.ssh/identity.pub file contains the RSA public key for authentication when you are using the SSH protocol version 1. A user should copy its contents in the $HOME/.ssh/authorized_keys file of the remote system where a user wants to log in using RSA authentication.
- $HOME/.ssh/id_dsa: The $HOME/.ssh/id_dsa file contains the protocol version 2 DSA authentication identity of the user.
- $HOME/.ssh/id_dsa.pub: The $HOME/.ssh/id_dsa.pub file contains the DSA public key for authentication when you are using the SSH protocol version 2. A user should copy its contents in the $HOME/.ssh/authorized_keys file of the remote system where a user wants to log in using DSA authentication.
- $HOME/.ssh/id_rsa: The $HOME/.ssh/id_rsa file contains the protocol version 2 RSA authentication identity of the user. This file should not be readable by anyone but the user.
- $HOME/.ssh/id_rsa.pub: The $HOME/.ssh/id_rsa.pub file contains the protocol version 2 RSA public key for authentication. The contents of this file should be added to $HOME/.ssh/authorized_keys on all computers where a user wishes to log in using public key authentication.
References[edit]
- ^https://devblogs.microsoft.com/commandline/windows10v1803/
- ^https://devblogs.microsoft.com/powershell/using-the-openssh-beta-in-windows-10-fall-creators-update-and-windows-server-1709/
External links[edit]
| The Wikibook OpenSSH has a page on the topic of: ssh-keygen |
- Generating an SSH key, a guide from GitHub
- ssh-keygen manual from the OpenBSD project
- Linux man page from die.net
RSA vs DSA
When dealing with cryptography and encryption algorithms, there are two names that will appear in every once in a while. These are DSA and RSA. Both of these are encryption systems that are in common use when encrypting content. Both of them give good results and can be employed at will. However, if there is need of their specific abilities, some differences are noted. A thorough comparison of the two is discussed below.
The DSA commonly refers to the Digital Signature Algorithm. The RSA on the other hand refers to the initials of the people who created it. These are Ron Rivest, Adi Shamir, and Leonard Adleman. The DSA was designed as an encryption algorithm. The DSA was developed by the NSA to be used by the US government as a standard for digital signatures. This signature borrows heavily from the ElGamal Signature Algorithm from which most ideas were borrowed from. RSA, on the other hand, looks at the difficulty of factoring numbers as the main aspect of its development.
The name DSA spells out its main function. This is a program that is mainly built for signing, and therefore it is quite popular with digital signatures. This however does not extend beyond the signature to the message itself. RSA, on the other hand, covers signing in encryption and encryption of the message contained as well.
As a result of dealing with digital signatures only, the use of DSA is preferred when faster key generation is needed. This is because DSA produces the keys very quickly. When faster encryption is required, RSA is preferred as it encrypts both message and signature for signing in. When in need of decryption, DSA is faster mainly due to the fact that it is specialized for a single function only. Digital signature generation work best with DSA while verification of the digital signature is faster when RSA is employed. In looking at how quickly either DSA or RSA handles a given task, it should be assessed whether fewer computer resources are used.
A perfect balance must be found which employs both DSA and RSA, as no single encryption algorithm can be rolled out alone. Both the RSA and DSA are crucial in rolling out encryption algorithms that can be employed in the server environment and with the client as well.
Both the RSA and DSA can be said to have similar cryptographic strengths. It is however the performance advantages when rolling out at specific points that make one or the other the preferred choice to be used at that specific point in time.
It can be generally concluded that the DSA is best suited for signing in and decrypting while verification and encryption can be left to the RSA. If any issue is noted with the performance, an evaluation can be done to find out if the right encryption algorithm has been rolled out.
Summary
DSA and RSA are two common encryption algorithms that can be said to be of equal strength
For everyone who is confused: If you are deploying a frontend-only application you cannot hide anything from your deployed site.If your code needs to access a value to make an API request that value will be visible in the browser's dev tools to any user who feels like checking. Any API request you make will be visible in the Network tab and will show the full URL and any headers, which will expose the key.Using the method in the gist above will stop your key being pushed to GitHub, but you cannot deploy your app without including the key. If I'm wrong someone please correct me! If I deploy a page on gh-pages and I have API keys in a config file, how can I hide the config file and at the same time, have them used in the website?Currently, the website says that it cannot recognise the API key variables because it cannot find any file called config.js.Can someone help me?I was just having this same issue, but then I realized: if my gh-pages site needs an API key and its being used in the website, that's essentially the same thing as sharing my API key openly (since the site uses it each time the site loads). Generate github api authetication key in java. The only way to hide it is to proxy your request through your own server.
The performance of the two is what distinguishes one from the other
DSA is faster when generating a key than RSA
RSA on the other hand is faster at encryption than DSA
When decrypting, DSA is faster, mainly due to its great decryption capability
If you need digital signing, DSA is the encryption algorithm of choice
For verification of the digital signature RSA is the best choice.
Rsa And Dsa Key Generation Utility Trailer
Depending on the circumstances, a choice will need to be made, but both DSA and RSA have equal encryption capabilities and the option with less demand on the resources should be chosen.
Rsa And Dsa Key Generation Utility Download
- The Difference Between Mediation and Conciliation - April 15, 2018
- Difference Between the Jscripts and Java Scripts - November 17, 2013
- Difference Between EJB 2.1 and EJB 3.0 - November 16, 2013