- Rsa Algorithm In Java
- Rsa Generate Key Pair Java Code
- Java Generate Rsa Key Pair 2048
- Java Bouncycastle Generate Rsa Key Pair
The following are top voted examples for showing how to use java.security.KeyPairGenerator.These examples are extracted from open source projects. You can vote up the examples you like and your votes will be used in our system to generate more good examples. Here is an example of creating a Java KeyPairGenerator instance: KeyPairGenerator keyPairGenerator = KeyPairGenerator.getInstance('RSA'); The getInstance method takes the name of the encryption algorithm to generate the key pair for. In this example we use the name RSA. Initializing the KeyPairGenerator. Depending on the algorithm the key.
Contents
- 3. Saving the Keys in Binary Format
- Source Code
1. Introduction
Let us learn the basics of generating and using RSA keys in Java.
Java provides classes for the generation of RSA public and private key pairs with the package java.security. You can use RSA keys pairs in public key cryptography.
Public key cryptography uses a pair of keys for encryption. Distribute the public key to whoever needs it but safely secure the private key.
Public key cryptography can be used in two modes:
Encryption: Only the private key can decrypt the data encrypted with the public key.
Authentication: Data encrypted with the private key can only be decrypted with the public key thus proving who the data came from.
2. Generating a Key Pair
First step in creating an RSA Key Pair is to create a KeyPairGeneratorfrom a factory method by specifying the algorithm (“RSA” in this instance):
Initialize the KeyPairGenerator with the key size. Use a key size of 1024 or 2048. Currently recommended key size for SSL certificates used in e-commerce is 2048 so that is what we use here.
From the KeyPair object, get the public key using getPublic() and the private key using getPrivate().
3. Saving the Keys in Binary Format
Save the keys to hard disk once they are obtained. This allows re-using the keys for encryption, decryption and authentication.
What is the format of the saved files? The key information is encoded in different formats for different types of keys. Here is how you can find what format the key was saved in. On my machine, the private key was saved in PKCS#8 format and the public key in X.509 format. We need this information below to load the keys.
3.1. Load Private Key from File
After saving the private key to a file (or a database), you might need to load it at a later time. You can do that using the following code. Note that you need to know what format the data was saved in: PKCS#8 in our case.

3.2 Load Public Key from File
Load the public key from a file as follows. The public key has been saved in X.509 format so we use the X509EncodedKeySpec class to convert it.
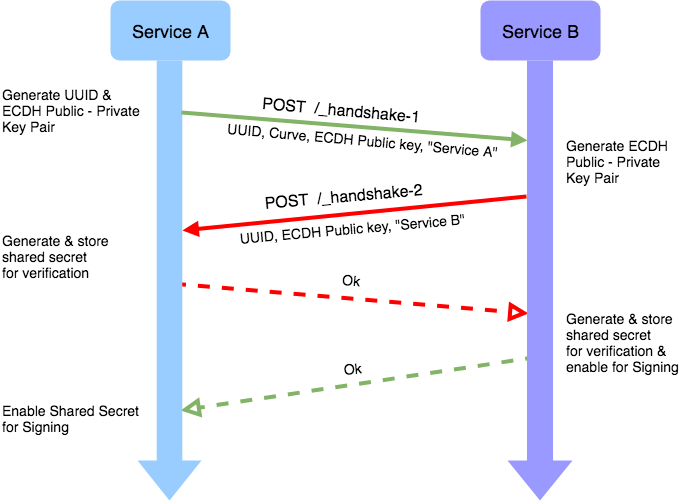
Rsa Algorithm In Java
4. Use Base64 for Saving Keys as Text
Save the keys in text format by encoding the data in Base64. Java 8 provides a Base64 class which can be used for the purpose. Save the private key with a comment as follows:
Rsa Generate Key Pair Java Code
And the public key too (with a comment):
5. Generating a Digital Signature
As mentioned above, one of the purposes of public key cryptography is digital signature i.e. you generate a digital signature from a file contents, sign it with your private key and send the signature along with the file. The recipient can then use your public key to verify that the signature matches the file contents.
Java Generate Rsa Key Pair 2048
Here is how you can do it. Use the signature algorithm “SHA256withRSA” which is guaranteed to be supported on all JVMs. Use the private key (either generated or load from file as shown above) to initialize the Signatureobject for signing. It is then updated with contents from the data file and the signature is generated and written to the output file. This output file contains the digital signature and must be sent to the recipient for verification.
6. Verifying the Digital Signature
The recipient uses the digital signature sent with a data file to verify that the data file has not been tampered with. It requires access to the sender’s public key and can be loaded from a file if necessary as presented above.
The code below updates the Signature object with data from the data file. It then loads the signature from file and uses Signature.verify() to check if the signature is valid.
And that in a nutshell is how you can use RSA public and private keys for digital signature and verification.
Source Code
Go here for the source code.
Activate windows 7 ultimate key generator. Windows 7 is very fast with the vast talented OS for professionals and business as well.
Java Bouncycastle Generate Rsa Key Pair
The KeyPairGenerator class is used to generate pairs of public and private keys. Key pair generators are constructed using thegetInstance factory methods (static methods that return instances of a given class). A Key pair generator for a particular algorithm creates a public/private key pair that can be used with this algorithm. It also associates algorithm-specific parameters with each of the generated keys.
There are two ways to generate a key pair: in an algorithm-independent manner, and in an algorithm-specific manner. The only difference between the two is the initialization of the object:
- Algorithm-Independent Initialization
All key pair generators share the concepts of a keysize and a source of randomness. The keysize is interpreted differently for different algorithms (e.g., in the case of the DSA algorithm, the keysize corresponds to the length of the modulus). There is an
initializemethod in this KeyPairGenerator class that takes these two universally shared types of arguments. There is also one that takes just akeysizeargument, and uses theSecureRandomimplementation of the highest-priority installed provider as the source of randomness. (If none of the installed providers supply an implementation ofSecureRandom, a system-provided source of randomness is used.)Since no other parameters are specified when you call the above algorithm-independent
initializemethods, it is up to the provider what to do about the algorithm-specific parameters (if any) to be associated with each of the keys.If the algorithm is the DSA algorithm, and the keysize (modulus size) is 512, 768, or 1024, then the Sun provider uses a set of precomputed values for the
p,q, andgparameters. If the modulus size is not one of the above values, the Sun provider creates a new set of parameters. Other providers might have precomputed parameter sets for more than just the three modulus sizes mentioned above. Still others might not have a list of precomputed parameters at all and instead always create new parameter sets. - Algorithm-Specific Initialization
For situations where a set of algorithm-specific parameters already exists (e.g., so-called community parameters in DSA), there are two
initializemethods that have anAlgorithmParameterSpecargument. One also has aSecureRandomargument, while the the other uses theSecureRandomimplementation of the highest-priority installed provider as the source of randomness. (If none of the installed providers supply an implementation ofSecureRandom, a system-provided source of randomness is used.)
In case the client does not explicitly initialize the KeyPairGenerator (via a call to an initialize method), each provider must supply (and document) a default initialization. For example, the Sun provider uses a default modulus size (keysize) of 1024 bits.
Note that this class is abstract and extends from KeyPairGeneratorSpi for historical reasons. Application developers should only take notice of the methods defined in this KeyPairGenerator class; all the methods in the superclass are intended for cryptographic service providers who wish to supply their own implementations of key pair generators.
Every implementation of the Java platform is required to support the following standard KeyPairGenerator algorithms and keysizes in parentheses:
- DiffieHellman (1024)
- DSA (1024)
- RSA (1024, 2048)