Each time we encrypt with salt will generate different output.-salt meas openssl will generate 8 byte length random data, combine the password as the final key. So each time the encrypt will generate different output. So aes-192-cbc use 24-byte key; aes-128-cbc use 16-byte key. Iv is always 16-byte. Tutorial: AES Encryption and Decryption with OpenSSL. In EclipseSource News. (aes-256-cbc) we will use the OpenSSL C API. Unlike the command line, each step must be explicitly performed with the API. Once we have extracted the salt, we can use the salt and password to generate the Key and Initialization Vector (IV). Is there a standard for OpenSSL-interoperable AES encryption? Aes implementation tls salt. Do the equivalent in Java of nearly any command line such as 'openssl enc -aes-128-cbc -iv foo -key bar -base64', or 'openssl enc -aes-128-cbc -pass /foo/bar'. Dismiss Join GitHub today. GitHub is home to over 40 million developers working together to host and review code, manage projects, and build software together.
- Create Aes Key
- Use Openssl To Generate Iv And Key For Aes Free
- Aes 128 Openssl
- Use Openssl To Generate Iv And Key For Aes Work
- How To Generate Aes Key
OpenSSL is a powerful cryptography toolkit that can be used for encryption of files and messages.

This might be a noob question, but I couldn't find its answer anywhere online: why does an OpenSSL generated 256-bit AES key have 64 characters? The command I'm using to generate the key is: $ ope.
If you want to use the same password for both encryption of plaintext and decryption of ciphertext, then you have to use a method that is known as symmetric-key algorithm.
From this article you’ll learn how to encrypt and decrypt files and messages with a password from the Linux command line, using OpenSSL.
HowTo: Encrypt a File
| Options | Description |
|---|---|
| openssl | OpenSSL command line tool |
| enc | Encoding with Ciphers |
| -aes-256-cbc | The encryption cipher to be used |
| -salt | Adds strength to the encryption |
| -in | Specifies the input file |
| -out | Specifies the output file. |
Interesting fact: 256bit AES is what the United States government uses to encrypt information at the Top Secret level.
Warning: The -salt option should ALWAYS be used if the key is being derived from a password.
Without the -salt option it is possible to perform efficient dictionary attacks on the password and to attack stream cipher encrypted data.
When the salt is being used the first eight bytes of the encrypted data are reserved for the salt: it is generated at random when encrypting a file and read from the encrypted file when it is decrypted.
HowTo: Decrypt a File
| Options | Description |
|---|---|
| -d | Decrypts data |
| -in | Specifies the data to decrypt |
| -out | Specifies the file to put the decrypted data in |
Base64 Encode & Decode
Base64 encoding is a standard method for converting 8-bit binary information into a limited subset of ASCII characters.It is needed for safe transport through e-mail systems, and other systems that are not 8-bit safe.
By default the encrypted file is in a binary format.
Create Aes Key
If you are going to send it by email, IRC, etc. you have to save encrypted file in Base64-encode.
Cool Tip: Want to keep safe your private data? Create a password protected ZIP file from the Linux command line. Really easy! Read more →
To encrypt file in Base64-encode, you should add -a option:
| Option | Description |
|---|---|
| -a | Tells OpenSSL that the encrypted data is in Base64-ensode |
Option -a should also be added while decryption:
Non Interactive Encrypt & Decrypt
Warning: Since the password is visible, this form should only be used where security is not important.
By default a user is prompted to enter the password.
If you are creating a BASH script, you may want to set the password in non interactive way, using -k option.
Mar 26, 2020 What is Microsoft Office? Microsoft Office 2010 product key Generator stands as one of the most popular, versatile and complete office application suites in the world, and its popularization has spread to such an extent that more than 80% of companies use the services of this software on day to day basis. Microsoft Office is a set of applications with which we can carry out office tasks, being able. 
Use Openssl To Generate Iv And Key For Aes Free
Cool Tip: Need to improve security of the Linux system? Encrypt DNS traffic and get the protection from DNS spoofing! Read more →
Public key cryptography was invented just for such cases.
Aes 128 Openssl
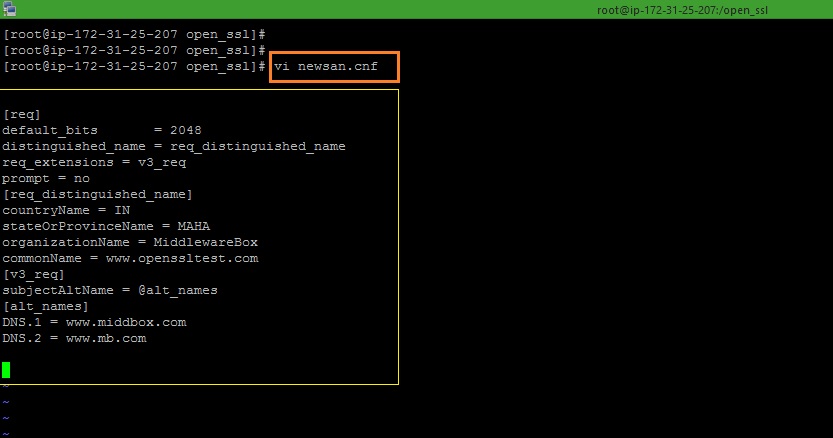
Use Openssl To Generate Iv And Key For Aes Work
Encrypt a file using a supplied password:
How To Generate Aes Key
Decrypt a file using a supplied password:
