
- By contrast with the rudimentary deterministic wallet described in Section 1, child public keys Q i can be computed using only knowledge of i, the master public key Q^, and the function hash. It is this fact that gives rise to the master public key feature of BIP32 HD wallets.
- BIP32 Deterministic Key Generator. Passphrase BIP32 Key.
- Client-side Bitcoin address and deterministic wallets generator. Bitcoin address generator. Toggle navigation BIP32 Generator. BIP32 Extended Key.
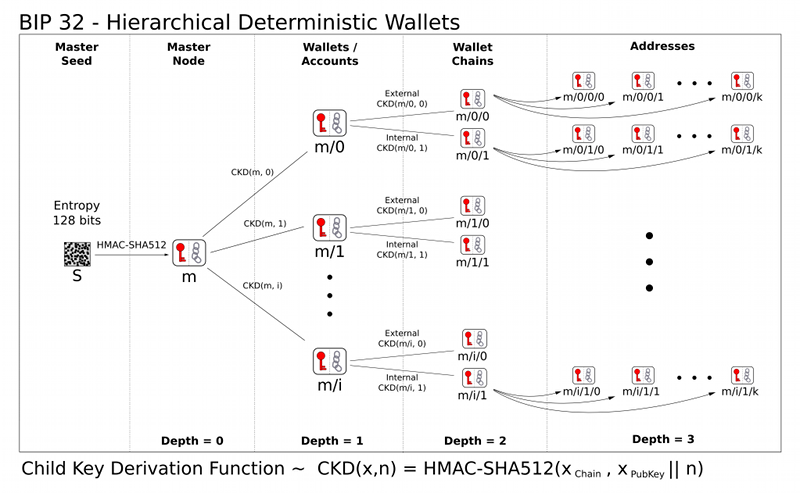
Derivation of child public key Hierarchical Deterministic Wallets have very useful characteristics that can generate child public key from a parent public key without using a private key. 1.Hash the below combination in HMAC-SHA 512 Parent Public Key(264-bit), Parent Chain Code(256-bit), Index number(32-bit).
List of tools/services for working with Hierarchical Deterministic Wallets, aka hd-wallets aka bip32 wallets.
Tools listed on this page can typically perform some form of key derivation and list hd-wallet addresses.
When you have an SSH key you need the public key to setup SSH passwordless login with SSH-key. But if you have lost the public key part but still have the private key, there is a way to regenerate the key. With the public key missing, the following command will show you that there is no public key for this SSH key. Generate private key with public key. To generate private (d,n) key using openssl you can use the following command: openssl genrsa -out private.pem 1024 To generate public (e,n) key from the private key using openssl you can use the following command: openssl rsa -in private.pem -out public.pem -pubout.
Warning: You should never give an online service your master extended private key (xprv) as they could use it to drain your entire wallet. Even sharing an extended public key entails risks. If using an online hosted javascript tool, be careful to work with it offline only.
See also Deterministic Wallet.
- 3Risks associated with sharing extended keys with a third party
Online Services
- Blockpath: Automatically scan all derivation paths for an xPub/yPub/zPub and view the balance of each used address, or generate all addresses and export them as text.
- bip32.org: A tool for displaying information derived from bip32 extended key, or nmenonic phrase. Appears to list only the first address.
- Mnemonic Code Converter: A tool for listing keys and addresses from a bip39 mnemonic phrase. The tool can be saved as a file and used without any internet connection.
- WebHDWallet: Implementing the Hierarchical Deterministic Wallet proposal BIP32, with the aim of creating easy to use, secure, and powerful tools for managing HD wallets and the funds within.
- mybitprices.info: A tool that can derive all used wallet addresses from an extended public key and can further lookup historic price information for all wallet transactions and create gain/loss reports.
- bitcore playground: Derive HD keys from a private or public extended key and a path.
Offline Command-line software
- python-mnemonic: Reference implementation of BIP-0039: Mnemonic code for generating deterministic keys
- hd-wallet-derive: A command-line tool that derives bip32 addresses and private keys from bip32 extended keys or mnemonic, and can generate new master keys as well. Supports segwit (p2sh,bech32) and hundreds of altcoins.
- hd-wallet-addrs: A command-line tool for finding bitcoin hd-wallet addresses that have actually received funds, including change addresses. (note: key derivation occurs offline, but funds lookup requires internet connection.)
- pybitcointools: Simple, common-sense Bitcoin-themed Python ECC library. by Vitalik Buterin.
- python-trezor: Client side implementation for TREZOR-compatible Bitcoin hardware wallets.
Risks associated with sharing extended keys with a third party
Risks of Sharing an Extended Private Key (xprv) DO-NOT-DO-THIS!!!
- The recipient can spend (steal) all your wallet funds.
- The recipient can obtain all your wallet keys and addresses, private and public.
- The recipient can identify and view all your historic transactions.
- The recipient can link all your wallet transactions together, possibly linking anonymous transactions with those associated with your identity.
Risks of Sharing an Extended Public Key (xpub)
Using The Bip32 Deterministic Key Generator Free
In general it is safest NOT to share an extended public key.
- The recipient can obtain all your wallet public keys and addresses, but not your private keys.
- The recipient can identify and view all your historic transactions.
- The recipient can link all your wallet transactions together, possibly linking anonymous transactions with those associated with your identity.
- If, and only if, the recipient also obtains a single private key from your wallet, the recipient can obtain all your private keys and steal your funds, just as if they had your xprv key.