Mar 02, 2020 Asymmetric Encryption. I am supposed to use asymmetric encryption to exchange the keys securely. The standard being RSA 2048, but the new recommended option is ED25519 256 as it's smaller key, more secure and faster. I speak under correction but ED25519 is a variant of ECDSA. Use public key cryptography pairs to encrypt and decrypt login information for your Amazon EC2 instance. Generate a key pair with a third-party tool of your choice. Save the public key to a local file. For example, /.ssh/my-key-pair.pub (Linux) or C:keysmy-key-pair.pub (Windows). The file name extension for this file is not important.
If you want to purchase or activate this particular software, then there are three different ways. It can create archives in Zip file format and unpack some other archives. Winzip 18.5 key generator for sale.
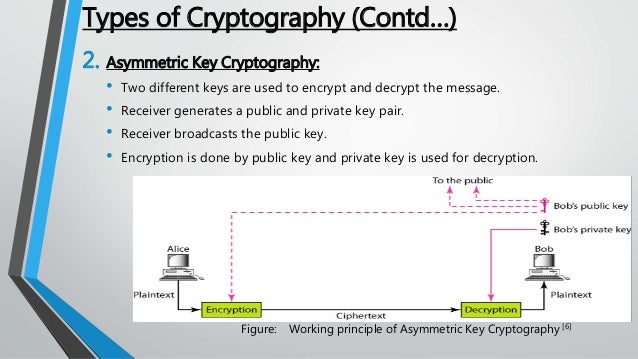
Private Key and public key are a part of encryption that encodes the information. Both keys work in two encryption systems called symmetric and asymmetric. Symmetric encryption (private-key encryption or secret-key encryption) utilize the same key for encryption and decryption. Asymmetric encryption utilizes a pair of keys like public and private key for better security where a message sender encrypts the message with the public key and the receiver decrypts it with his/her private key.
What Generates The Key Pair Used In Asymmetric Cryptography Model
Public and Private key pair helps to encrypt information that ensures data is protected during transmission.
- Which of the following generates the key pair used in asymmetric cryptography? CA CRL OCSP CPS CSP. Which cryptography system generates encryption keys that could be used with DES, AES, IDEA, RC5 or any other symmetric cryptography solution? MerkleHellman Knapsack RSA Elliptical Curve.
- RSA key pair generation is generally only performed once. A new RSA key pair only need to be generated when the old pair is revoked. Such a key pair can be used to encrypt/decrypt a lot of messages. The RSA public and private key are linked; it is not possible to generate new private keys that use the same public key.
Public Key
Public key uses asymmetric algorithms that convert messages into an unreadable format. A person who has a public key can encrypt the message intended for a specific receiver. The receiver with the private key can only decode the message, which is encrypted by the public key. The key is available via the public accessible directory.
Private Key
The private key is a secret key that is used to decrypt the message and the party knows it that exchange message. In the traditional method, a secret key is shared within communicators to enable encryption and decryption the message, but if the key is lost, the system becomes void. To avoid this weakness, PKI (public key infrastructure) came into force where a public key is used along with the private key. PKI enables internet users to exchange information in a secure way with the use of a public and private key.
Key Size and Algorithms
There are RSA, DSA, ECC (Elliptic Curve Cryptography) algorithms that are used to create a public and private key in public key cryptography (Asymmetric encryption). Due to security reason, the latest CA/Browser forum and IST advises to use 2048-bit RSA key. The key size (bit-length) of a public and private key pair decides how easily the key can be exploited with a brute force attack. The more computing power increases, it requires more strong keys to secure transmitting data.