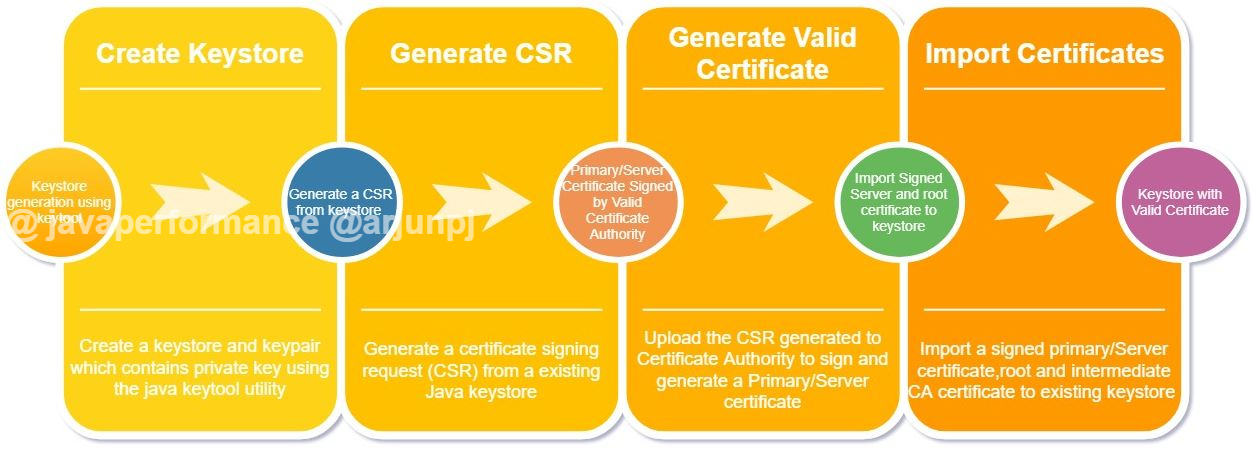
However, it only generates the CSR. Where is the private key? I was told that the key is generated at the time of CSR generation. I am using Windows 10. I plan to use node.js Express. Are there alternative tools we can use to generate CSR on Windows 10? Create a certificate request with PowerShell. UseExistingKeySet – This parameter is used to specify whether or not an existing key pair should be used in building a certificate request. RequestType – Determines the standard that is used to generate and send the certificate request. Note: If the CSR was never generated on this system then find the correct system. Its a glitch with processing pending requests associated with IIS and Exchange Systems. Troubleshoot the missing pending request or missing private key by performing the following. Step 1: Create an MMC Snap-in for Managing Certificates on a Windows server system. In order to create a CSR, users need two types of keys known as private and public keys. Next, in order for the CSR to be generated by all keys, the password and certificate must contain the same.
1. Open the notepad and copy and paste the configuration lines below and replace some parameters below accordance with your own company information. Such as: CN etc.
Save the following file as request.inf on your server editing the subject according to the comment:
Jun 09, 2019 Log on to the computer that issued the certificate request by using an account that has administrative permissions. Click Start, click Run, type mmc, and then click OK. On the File menu, click. Add/Remove Snap-in. In the Add/Remove Snap-in dialog box, click Add. Click Certificates, and then click.
;----------------- request.inf -----------------
[Version]
Signature='$Windows NT$'
[NewRequest]
;Change to your,country code, company name and common name
Subject = 'C=US, O=Example Co, CN=something.example.com'
KeySpec = 1
KeyLength = 2048
Exportable = TRUE
MachineKeySet = TRUE
SMIME = False
PrivateKeyArchive = FALSE
UserProtected = FALSE
UseExistingKeySet = FALSE
ProviderName = 'Microsoft RSA SChannel Cryptographic Provider'
ProviderType = 12
RequestType = PKCS10
KeyUsage = 0xa0
[EnhancedKeyUsageExtension]
OID=1.3.6.1.5.5.7.3.1 ; this is for Server Authentication / Token Signing
;-----------------------------------------------
2. Open command prompt and make sure you have the full admin rights on the server to do this step:
C:>certreq -new request.inf request.csr
3. Open the request.csr using notepad and copy the contents to your order screen or on your CMS portal.
Windows Generate Csr From Existing Key And Certificate
Generate A Certificate Windows 10
Installing Certificate: When your certificate is issued you'll typically receive a file called entrustcert.crt, Save it on the server and from the same directory run: C:>certreq -accept store_acmesafe_com.cer This will install the cert in the Windows certificate store and it will be available in IIS , MMC , Exchange , LDAP/Active Directory , Terminal Services and those products that make use of the Windows certificate store. For more information, please visit: http://support.microsoft.com/kb/321051 Hours of Operation:
|