Objective
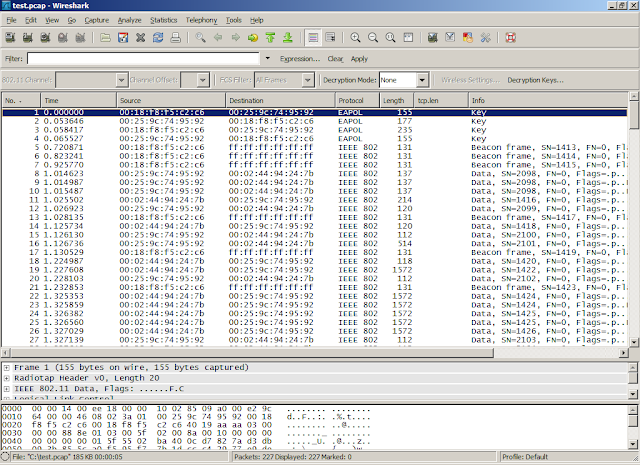
WLAN Key Generator Character Set 0-9, A-Z, a-z (ASCII 48-57, 65-90, 97-122) 0-9, A-Z, a-z + special characters (ASCII 33-126) 0-9. Feb 14, 2018 Wi-Fi Protected Access 2 - Pre-Shared Key (WPA-PSK), is a method of securing the network using WPA2 with Pre-Shared Key (PSK) authentication, designed for home networks that utilize keys, which are 64 hexadecimal digits long.
Wi-Fi Protected Access (WPA) is one of the security protocol used for wireless networks. When compared to Wired Equivalent Privacy (WEP) security protocol, WPA has improved the authentication and encryption features. If WPA is configured on the AP, a WPA Pre-Shared Key (PSK) is chosen to securely authenticate clients. When WPA-PSK Complexity is enabled, complexity requirements for the key used in the authentication process can be configured. More complex keys provide increased security.
This article explains how to configure WPA-PSK Complexity on the WAP121 and WAP321 access points.
Applicable Devices
• WAP121
• WAP321
Software Version
Generate random string in python for secret key. • 1.0.3.4
WPA-PSK Complexity Configuration
Step 1. Log in to the web configuration utility and choose System Security > WPA-PSK Complexity. The WPA-PSK Complexity page opens:
Step 2. Check the Enable check box in the WPA-PSK Complexity field to enable the AP to check new WPA-PSK keys for complexity.
Step 3. Choose the minimum number of character classes that must be represented in the key string from the WPA-PSK Minimum Character Class drop-down list. The four possible character classes are uppercase letters, lowercase letters, numbers, and the special characters available on a standard keyboard.
Step 4. (Optional) To configure a different key when the current key expires check the Enable check box in the WPA-PSK Different From Current field. Uncheck the Enable check box to allow the user to reenter the previous key when the current key expires.
Step 5. Enter the maximum length that the pre-shared key can be in the Maximum WPA-PSK Length field. The value ranges from 32 to 63.
Step 6. Enter the minimum length that the pre-shared key can be in the Minimum WPA-PSK Length field. The value ranges from 8 to 16.
Step 7. Click Save to save the settings.
Wpa-psk Pre-shared Key Generator Key
Contents
Introduction
This document describes a sample configuration for Wireless Protected Access (WPA) and WPA2 with a pre-shared key (PSK).
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Familiarity with the GUI or the command-line interface (CLI) for the Cisco IOS® software
- Familiarity with the concepts of PSK, WPA, and WPA2
Components Used
The information in this document is based on Cisco Aironet 1260 Access Point (AP) that runs Cisco IOS Software Release 15.2JB.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Configure
Configuration with GUI
This procedure describes how to configure WPA and WPA2 with a PSK in the Cisco IOS software GUI:
- Set up the Encryption Manager for the VLAN defined for the Service Set Identifier (SSID). Navigate to Security > Encryption Manager, ensure Cipher is enabled, and select AES CCMP + TKIP as the cipher to be used for both SSIDs.
- Enable the correct VLAN with the encryption parameters defined in Step 1. Navigate to Security > SSID Manager, and select the SSID from the Current SSID List. This step is common for both WPA and WPA2 configuration.
- In the SSID page, set Key Management to Mandatory, and check the Enable WPA checkbox. Select WPA from the drop-down list in order to enable WPA. Enter the WPA Pre-shared Key.
- Select WPA2 from the drop-down list in order to enable WPA2.
Configuration with CLI
Notes:
Use the Command Lookup Tool (registered customers only) in order to obtain more information on the commands used in this section.
The Output Interpreter Tool (registered customers only) supports certain show commands. Use the Output Interpreter Tool in order to view an analysis of show command output.
This is the same configuration done within the CLI:
Verify
In order to confirm that the configuration works properly, navigate to Association, and verify that the client is connected:
You can also verify the client association in the CLI with this syslog message:
Troubleshoot
Note: Refer to Important Information on Debug Commands before you use debug commands.
Use these debug commands in order to troubleshoot connectivity issues:
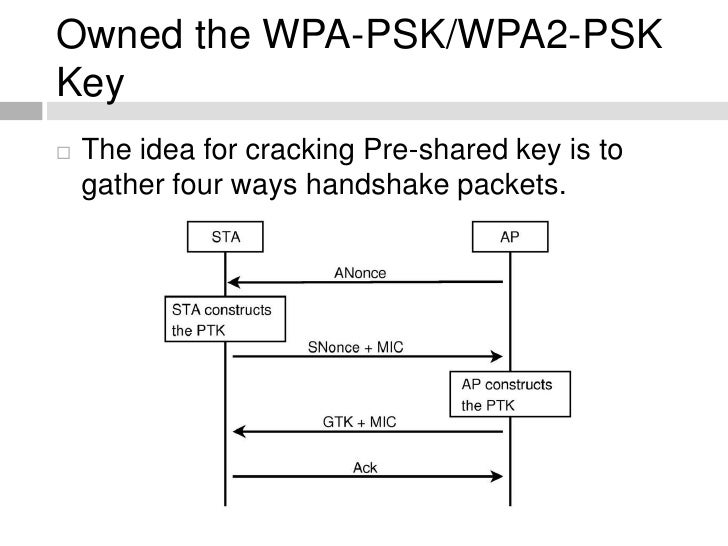
- debug dot11 aaa manager keys - This debug shows the handshake that occurs between the AP and the client as the pairwise transient key (PTK) and group transient key (GTK) negotiate.
- debug dot11 aaa authenticator state-machine - This debug shows the various states of negotiations that a client passes through as the client associates and authenticates. The state names indicate these states.
- debug dot11 aaa authenticator process - This debug helps you diagnose problems with negotiated communications. The detailed information shows what each participant in the negotiation sends and shows the response of the other participant. You can also use this debug in conjunction with the debug radius authentication command.
- debug dot11 station connection failure - This debug helps you determine if the clients are failing the connection and helps you determine the reason for failures.