- Jul 09, 2019 If the Private Key key file is lost, you’ll need to reissue your Certificate. Can I generate a new Private Key for my Certificate if I lose the old one? You can generate a new private key and CSR, or use the automatic CSR and key generation during Certificate reissue (this option is available for all Certificates except for the Multi.
- The following are ways to create a certificate in Key Vault: Create a self-signed certificate: This will create a public-private key pair and associate it with a certificate. The certificate will be signed by its own key. Create a new certificate manually: This will create a public-private key pair and generate an X.509 certificate signing.
- Online CSR and Key Generator SSL.com’s public CSR and Key Generator is currently down for maintenance as part of our website’s redesign and update. We will be back soon with a new and updated version.
- Jul 08, 2009 You can also generate self signed SSL certificate for testing purpose. In this article, let us review how to generate private key file (server.key), certificate signing request file (server.csr) and webserver certificate file (server.crt) that can be used on Apache server with modssl. Key, CSR and CRT File Naming Convention.
Generate online private and public key for ssh, putty, github, bitbucket Save both of keys on your computer (text file, dropbox, evernote etc)!!! The generated keys are RANDOM and CAN'T be restored.
A Key Vault (KV) certificate can be either created or imported into a key vault. When a KV certificate is created the private key is created inside the key vault and never exposed to certificate owner. The following are ways to create a certificate in Key Vault:
Create a self-signed certificate: This will create a public-private key pair and associate it with a certificate. The certificate will be signed by its own key.
Create a new certificate manually: This will create a public-private key pair and generate an X.509 certificate signing request. The signing request can be signed by your registration authority or certification authority. The signed x509 certificate can be merged with the pending key pair to complete the KV certificate in Key Vault. Although this method requires more steps, it does provide you with greater security because the private key is created in and restricted to Key Vault. This is explained in the diagram below.
These types ofapplications expose their API keys publicly, so we recommendusing a instead.Seefor examples.Use IP addresses to limit API key access to certain IP addresses.Use Android apps for Android applications. Youcan only set one restriction type per API key.Choose the restriction type based on the needs of your application.Use None for testing purposes only.Use HTTP referrers for API clients that run on a webbrowser, so that only the specified pages can call the API. Add application restrictions based on your application type. Unrestricted keys are insecure becausethey can be viewed publicly, such as from within a browser, or they can beaccessed on a device where the key resides.For production applications, set both application and API restrictions.To add API key restrictions:.Navigate to thepanel in Cloud Console.Select the name of an existing API key.Application restrictionsApplication restrictions specify which web sites, IP addresses, or apps can usean API key. Generating api key for google map android api on my project 2019.
The following descriptions correspond to the green lettered steps in the preceding diagram.
- In the diagram above, your application is creating a certificate which internally begins by creating a key in your key vault.
- Key Vault returns to your application a Certificate Signing Request (CSR)
- Your application passes the CSR to your chosen CA.
- Your chosen CA responds with an X509 Certificate.
- Your application completes the new certificate creation with a merger of the X509 Certificate from your CA.
- Create a certificate with a known issuer provider: This method requires you to do a one-time task of creating an issuer object. Once an issuer object is created in you key vault, its name can be referenced in the policy of the KV certificate. A request to create such a KV certificate will create a key pair in the vault and communicate with the issuer provider service using the information in the referenced issuer object to get an x509 certificate. The x509 certificate is retrieved from the issuer service and is merged with the key pair to complete the KV certificate creation.
The following descriptions correspond to the green lettered steps in the preceding diagram.
Php artisan key:generate command 1. Dec 07, 2016 The key:generate command is used to generate a random key. This command will update the key stored in the application's environment file. The command also supports an optional -show flag. Specifying this flag will simply show the generated key instead of updating any configuration or environment files. When running. Php artisan key:generate. I can see the generated key in my shell, but the variable 'key' in app.php remains empty. Running on localhost with windows-apache-php 5.4 - mysql. You can generate a key by the following command: php artisan key:generate The key will be written automatically in your.env file. APPKEY=YOURGENERATEDKEY If you want to see your key after generation use -show option. Php artisan key:generate -show Note: The.env is.
- In the diagram above, your application is creating a certificate which internally begins by creating a key in your key vault.
- Key Vault sends an TLS/SSL Certificate Request to the CA.
- Your application polls, in a loop and wait process, for your Key Vault for certificate completion. The certificate creation is complete when Key Vault receives the CA’s response with x509 certificate.
- The CA responds to Key Vault's TLS/SSL Certificate Request with an TLS/SSL X.509 certificate.
- Your new certificate creation completes with the merger of the TLS/SSL X.509 certificate for the CA.
Asynchronous process
KV certificate creation is an asynchronous process. This operation will create a KV certificate request and return an http status code of 202 (Accepted). The status of the request can be tracked by polling the pending object created by this operation. The full URI of the pending object is returned in the LOCATION header.
When a request to create a KV certificate completes, the status of the pending object will change to “completed” from “inprogress”, and a new version of the KV certificate will be created. This will become the current version.
First creation
When a KV certificate is created for the first time, an addressable key and secret is also created with the same name as that of the certificate. If the name is already in use, then the operation will fail with an http status code of 409 (conflict).The addressable key and secret get their attributes from the KV certificate attributes. The addressable key and secret created this way are marked as managed keys and secrets, whose lifetime is managed by Key Vault. Managed keys and secrets are read-only. Note: If a KV certificate expires or is disabled, the corresponding key and secret will become inoperable.
If this is the first operation to create a KV certificate then a policy is required. A policy can also be supplied with successive create operations to replace the policy resource. If a policy is not supplied, then the policy resource on the service is used to create a next version of KV certificate. Note that while a request to create a next version is in progress, the current KV certificate, and corresponding addressable key and secret, remain unchanged.
Self-issued certificate
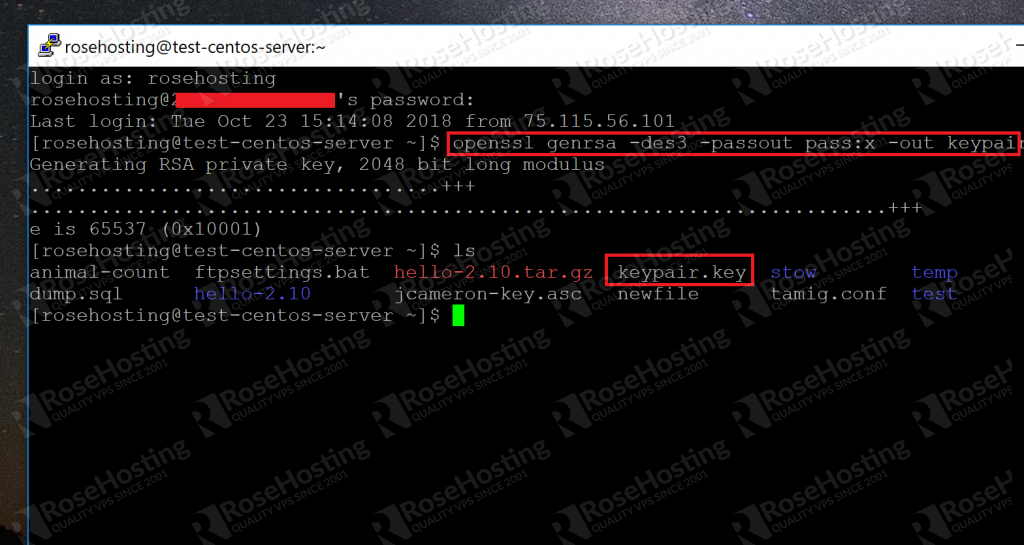
Generate Certificate With Private Key
To create a self-issued certificate, set the issuer name as 'Self' in the certificate policy as shown in following snippet from certificate policy.
If the issuer name is not specified, then the issuer name is set to 'Unknown'. When issuer is 'Unknown', the certificate owner will have to manually get a x509 certificate from the issuer of his/her choice, then merge the public x509 certificate with the key vault certificate pending object to complete the certificate creation.
Partnered CA Providers
Certificate creation can be completed manually or using a “Self” issuer. Key Vault also partners with certain issuer providers to simplify the creation of certificates. The following types of certificates can be ordered for key vault with these partner issuer providers.
| Provider | Certificate type |
|---|---|
| DigiCert | Key Vault offers OV or EV SSL certificates with DigiCert |
| GlobalSign | Key Vault offers OV or EV SSL certificates with GlobalSign |
A certificate issuer is an entity represented in Azure Key Vault (KV) as a CertificateIssuer resource. It is used to provide information about the source of a KV certificate; issuer name, provider, credentials, and other administrative details.
Note that when an order is placed with the issuer provider, it may honor or override the x509 certificate extensions and certificate validity period based on the type of certificate.
Authorization: Requires the certificates/create permission.