- Generate Dlp Client Bypass Key Code
- Generate Dlp Client Bypass Key Switch
- Generate Dlp Client Bypass Key Not Working
- Generate Dlp Client Bypass Key Card
- Generate Dlp Client Bypass Key Fob
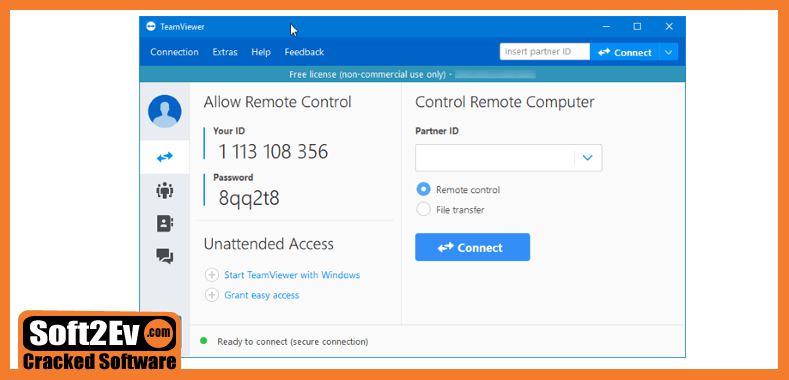
DLP may gain complete control of your mailbox to generate and send e-mail with virus attachments, e-mail hoaxes, spam and other types of unsolicited e-mail to other people. Download Exterminate It! TOP10 Alerts Top 100 Alerts. Jul 28, 2016 Albeit we only had this issue on 5 computers, that would take a lot of time to do. We wound up having to re-install DLP on the server, push out the McAfee Agent to the client(s), update the DLP agent on the clients, then run the removal policy from the EPO software. Talk about a headache! Action: DLP Generate Client Bypass Key Details: Generated for X (email@domain) on computer Y. The bypass duration is Z Minutes. The business reason for generating this key is AA You can create a custom query: Queries & Reports - New Query - Database type: ePO - Feature Group: Logging - Result Types: Audit Log Entries.
Data loss prevention is a compliance feature of Office 365 that is designed to help your organization prevent the intentional or accidental exposure of sensitive information to unwanted parties. DLP has its roots in Exchange Server and Exchange Online, and is also applicable in SharePoint Online and OneDrive for Business.
Jan 16, 2020 Choose the option to Generate DLP Client Override Key. Leave the Key Type as Client Bypass key. Provide the End User Name and End User Email Address. In the Client Bypass Password section, select Get Password from Policy. Choose the Policy assigned to the system and provide the Revision Number. You can find this number in the DLP Console on the endpoint. RandomKeygen is a free mobile-friendly tool that offers randomly generated keys and passwords you can use to secure any application, service or device. KEY RandomKeygen - The Secure Password & Keygen Generator.
DLP uses a content analysis engine to examine the contents of email messages and files, looking for sensitive information such as credit card numbers and personally identifiable information (PII). Sensitive information should typically not be sent in email, or included in documents, without taking additional steps such as encrypting the email message or files. Using DLP you can detect sensitive information, and take action such as:
- Log the event for auditing purposes
- Display a warning to the end user who is sending the email or sharing the file
- Actively block the email or file sharing from taking place
Sometimes customers dismiss DLP because they don't consider themselves to have the type of data that needs protecting. The assumption is that sensitive data, such as medical records or financial information, only exists for industries like health care or for companies that run online stores. But any business can handle sensitive information on a regular basis, even if they don't realize it. A spreadsheet of employee names and dates of birth is just as sensitive as a spreadsheet of customer names and credit card details. And this type of information tends to float around more than you might expect, as employees quietly go about their day to day tasks, thinking nothing of export a CSV file from a system and emailing it to someone. You might also be surprised how often employees send emails containing credit card or banking details without considering the consequences.
How sensitive information is detected by DLP
Sensitive information is identified by regular expression (RegEx) pattern matching, in combination with other indicators such as the proximity of certain keywords to the matching patterns. An example of this is credit card numbers. A VISA credit card number has 16 digits. However, those digits can be written in different ways, such as 1111-1111-1111-1111, 1111 1111 1111 1111, or 1111111111111111.
Any 16 digit string is not necessarily a credit card number, it could be a ticket number from a help desk system, or a serial number of a piece of hardware. To tell the difference between a credit card number and a harmless 16-digit string, a calculation is performed (checksum) to confirm that the numbers match a known pattern from the various credit card brands.
Furthermore, the proximity of keywords such as 'VISA' or 'AMEX', along with the proximity to date values that might be the credit card expiry date, is also considered to make a decision about whether the data is a credit card number or not.
In other words, DLP is usually smart enough to recognize the difference between these two texts in an email:
- 'Can you order me a new laptop. Use my VISA number 1111-1111-1111-1111, expiry 11/22, and send me the estimated delivery date when you have it.'
- 'My laptop serial number is 2222-2222-2222-2222 and it was purchased on 11/2010. By the way, is my travel visa approved yet?'
Generate Dlp Client Bypass Key Code
A good reference to keep bookmarked is this topic on sensitive information types that explains how each information type is detected.
Where to start with data loss prevention
When the risks of data leakage aren't entirely obvious, it's difficult to work out where exactly you should start with implementing DLP. Fortunately, DLP policies can be run in 'test mode', allowing you to gauge their effectiveness and accuracy before you turn them on.
DLP policies for Exchange Online can be managed through the Exchange admin center. But you can configure DLP policies for all workloads through the Security & Compliance Center, so that's what I'll use for demonstrations in this article. In the Security & Compliance Center you'll find the DLP policies under Data loss prevention > Policy. Click on Create a policy to start.
Office 365 provides a range of DLP policy templates you can use to create DLP policies. Let's say that you're an Australian business. You can filter the policy templates to display only those that are relevant to Australia, which fall into the general categories of Financial, Medical and Health, and Privacy.
For this demonstration I'll choose Australian Personally Identifiable Information (PII) Data, which includes the information types of Australian Tax File Number (TFN) and Driver's License Number.
Give your new DLP policy a name. The default name will match the DLP policy template, but you should choose a more descriptive name of your own, because multiple policies can be created from the same template.
Choose the locations that the policy will apply to. DLP policies can apply to Exchange Online, SharePoint Online, and OneDrive for Business. I am going to leave this policy configured to apply to all locations.
At the first Policy Settings step just accept the defaults for now. There is quite a lot of customization you can do in DLP policies, but the defaults are a fine place to start.
After clicking Next you'll be presented with an additional Policy Settings page with more customization options. For a policy that you are just testing, here's where you can start to make some adjustments.
- I've turned off policy tips for now, which is a reasonable step to take if you're just testing things out and don't want to display anything to users yet. Policy tips display warnings to users that they're about to violate a DLP policy. For example, an Outlook user will see a warning that the file they've attached contains credit card numbers and will cause their email to be rejected. The goal of policy tips is to stop the non-compliant behaviour before it happens.
- I've also decreased the number of instances from 10 to 1, so that this policy will detect any sharing of Australian PII data, not just bulk sharing of the data.
- I've also added another recipient to the incident report email.
Finally, I've configured this policy to run in test mode initially. Notice there's also an option here to disable policy tips while in test mode. This gives you the flexibility to have policy tips enabled in the policy, but then decide whether to show or suppress them during your testing.
On the final review screen click Create to finish creating the policy.
Test a DLP policy
Your new DLP policy will begin to take effect within about 1 hour. You can sit and wait for it to be triggered by normal user activity, or you can try to trigger it yourself. Earlier I linked to this topic on sensitive information types, which provides you with information about how to trigger DLP matches.
As an example, the DLP policy I created for this article will detect Australian tax file numbers (TFN). According to the documentation, the match is based on the following criteria.
To demonstrate TFN detection in a rather blunt manner, an email with the words 'Tax file number' and a 9 digit string in close proximity will sail through without any issues. The reason it does not trigger the DLP policy is that the 9-digit string must pass the checksum that indicates it is a valid TFN and not just a harmless string of numbers.
In comparison, an email with the words 'Tax file number' and a valid TFN that passes the checksum will trigger the policy. For the record here, the TFN I'm using was taken from a website that generates valid, but not genuine, TFNs. Such sites are very useful because one of the most common mistakes when testing a DLP policy is using a fake number that's not valid and won't pass the checksum (and therefore won't trigger the policy).
The incident report email includes the type of sensitive information that was detected, how many instances were detected, and the confidence level of the detection.
If you leave your DLP policy in test mode and analyze the incident report emails, you can start to get a feel for the accuracy of the DLP policy and how effective it will be when it is enforced. In addition to the incident reports, you can use the DLP reports to see an aggregated view of policy matches across your tenant.
Tune a DLP policy
As you analyze your policy hits you might want to make some adjustments to how the policies behave. As a simple example, you might determine that one TFN in email is not a problem (I think it still is, but let's go with it for the sake of demonstration), but two or more instances is a problem. Multiple instances could be a risky scenario such as an employee emailing a CSV export from the HR database to an external party, for example an external accounting service. Definitely something you would prefer to detect and block.
In the Security & Compliance Center you can edit an existing policy to adjust the behaviour.
You can adjust the location settings so that the policy is applied only to specific workloads, or to specific sites and accounts.
You can also adjust the policy settings and edit the rules to better suit your needs.
When editing a rule within a DLP policy you can change:
- The conditions, including the type and number of instances of sensitive data that will trigger the rule.
- The actions that are taken, such as restricting access to the content.
- User notifications, which are policy tips that are displayed to the user in their email client or web browser.
- User overrides, which determines whether users can choose to proceed with their email or file sharing anyway.
- Incident reports, to notify administrators.
For this demonstration I've added user notifications to the policy (be careful of doing this without adequate user awareness training), and allowed users to override the policy with a business justification or by flagging it as a false positive. Note that you can also customize the email and policy tip text if you want to include any additional information about your organization's policies, or prompt users to contact support if they have questions.
The policy contains two rules for handling of high volume and low volume, so be sure to edit both with the actions that you want. This is an opportunity to treat cases differently depending on their characteristics. For example, you might allow overrides for low volume violations, but not allow overrides for high volume violations.
Also, if you want to actually block or restrict access to content that is in violation of policy, you need to configure an action on the rule to do so.
After saving those changes to the policy settings, I also need to return to the main settings page for the policy and enable the option to show policy tips to users while the policy is in test mode. This is an effective way to introduce DLP policies to your end users, and do user awareness training, without risking too many false positives that impact their productivity.
On the server side (or cloud side if you prefer), the change may not take effect immediately, due to various processing intervals. If you're making a DLP policy change that will display new policy tips to a user, the user may not see the changes take effect immediately in their Outlook client, which checks for policy changes every 24 hours. If you want to speed things up for testing, you can use this registry fix to clear the last download time stamp from the PolicyNudges key. Outlook will download the latest policy information the next time you restart it and begin composing an email message.
If you have policy tips enabled, the user will begin to see the tips in Outlook, and can report false positives to you when they occur.
Investigate false positives
DLP policy templates are not perfect straight out of the box. It's likely that you'll find some false positives occurring in your environment, which is why it's so important to ease your way into a DLP deployment, taking the time to adequately test and tune your policies.
Here's an example of a false positive. This email is quite harmless. The user is providing their mobile phone number to someone, and including their email signature.
But the user sees a policy tip warning them that the email contains sensitive information, specifically, an Australian driver's license number.
The user can report the false positive, and the administrator can look into why it has occurred. In the incident report email, the email is flagged as a false positive.
This driver's license case is a good example to dig into. The reason this false positive has occurred is that the 'Australian Driver's License' type will be triggered by any 9-digit string (even one that is part of a 10-digit string), within 300 characters proximity to the keywords 'sydney nsw' (not case sensitive). So it's triggered by the phone number and email signature, only because the user happens to be in Sydney.
One option is to remove the Australian driver's license information type from the policy. It's in there because it's part of the DLP policy template, but we're not forced to use it. If you're only interested in Tax File Numbers and not driver's licenses, you can just remove it. For example, you can remove it from the low volume rule in the policy, but leave it in the high volume rule so that lists of multiple drivers licenses are still detected.
Another option is to simply increase the instance count, so that a low volume of driver's licenses is only detected when there are multiple instances.
In addition to changing the instance count, you can also adjust the match accuracy (or confidence level). If your sensitive information type has multiple patterns, you can adjust the match accuracy in your rule, so that your rule matches only specific patterns. For example, to help reduce false positives, you can set the match accuracy of your rule so that it matches only the pattern with the highest confidence level. Understanding how confidence level is calculated is a bit tricky (and beyond the scope of this post), but here's a good explanation of how to use confidence level to tune your rules.
Finally, if you want to get even a bit more advanced, you can customize any sensitive information type -- for example, you can remove 'Sydney NSW' from the list of keywords for Australian Driver's License, to eliminate the false positive triggered above. To learn how to do this by using XML and PowerShell, see this topic on customizing a built-in sensitive information type.
Turn on a DLP policy
When you're happy that your DLP policy is accurately and effectively detecting sensitive information types, and that your end users are ready to deal with the policies being in place, then you can enable the policy.
If you're waiting to see when the policy will take effect, Connect to Security & Compliance Center PowerShell and run the Get-DlpCompliancePolicy cmdlet to see the DistributionStatus.
After turning on the DLP policy, you should run some final tests of your own to make sure that the expected policy actions are occurring. If you're trying to test things like credit card data, there are websites online with information on how to generate sample credit card or other personal information that will pass checksums and trigger your policies.
Policies that allow user overrides will present that option to the user as part of the policy tip.
Policies that restrict content will present the warning to the user as part of the policy tip, and prevent them from sending the email.
Summary
Data loss prevention policies are useful for organizations of all types. Testing some DLP policies is a low risk exercise due to the control you have over things like policy tips, end user overrides, and incident reports. You can quietly test some DLP policies to see what type of violations are already occurring in your organization, and then craft policies with low false positive rates, educate your users on what is allowed and not allowed, and then roll out your DLP policies to the organization.
-->When you create an application that needs access to secured services like the Office 365 Management APIs, you need to provide a way to let the service know if your application has rights to access it. The Office 365 Management APIs use Azure AD to provide authentication services that you can use to grant rights for your application to access them.
There are four key steps:
Register your application in Azure AD. To allow your application access to the Office 365 Management APIs, you need to register your application in Azure AD. This allows you to establish an identity for your application and specify the permission levels it needs to access the APIs.
Get Office 365 tenant admin consent. An Office 365 tenant admin must explicitly grant consent to allow your application to access their tenant data by means of the Office 365 Management APIs. The consent process is a browser-based experience that requires the tenant admin to sign in to the Azure AD consent UI and review the access permissions that your application is requesting, and then either grant or deny the request. After consent is granted, the UI redirects the user back to your application with an authorization code in the URL. Your application makes a service-to-service call to Azure AD to exchange this authorization code for an access token, which contains information about both the tenant admin and your application. The tenant ID must be extracted from the access token and stored for future use.
Request access tokens from Azure AD. Using your application's credentials as configured in Azure AD, your application requests additional access tokens for a consented tenant on an ongoing basis, without the need for further tenant admin interaction. These access tokens are called app-only tokens because they do not include information about the tenant admin.
Call the Office 365 Management APIs. The app-only access tokens are passed to the Office 365 Management APIs to authenticate and authorize your application.
The following diagram shows the sequence of consent and access token requests.
Important
Before you can access data through the Office 365 Management Activity API, you must enable unified audit logging for your Office 365 organization. You do this by turning on the Office 365 audit log. For instructions, see Turn Office 365 audit log search on or off.
Enabling unified audit logging isn't required if you're only using the Office 365 Service Communications API.
Register your application in Azure AD
The Office 365 Management APIs use Azure AD to provide secure authentication to Office 365 tenant data. To access the Office 365 Management APIs, you need to register your app in Azure AD, and as part of the configuration, you will specify the permission levels your app needs to access the APIs.
Prerequisites
To register your app in Azure AD, you need a subscription to Office 365 and a subscription to Azure that has been associated with your Office 365 subscription. You can use trial subscriptions to both Office 365 and Azure to get started. For more details, see Welcome to the Office 365 Developer Program.
Use the Azure Management Portal to register your application in Azure AD
After you have a Microsoft tenant with the proper subscriptions, you can register your application in Azure AD.
Sign into the Azure management portal, using the credential of your Microsoft tenant that has the subscription to Office 365 you wish to use. You can also access the Azure Management Portal via a link that appears in the left navigation pane in the Office admin portal.
In the left navigation panel, choose Active Directory (1). Make sure the Directory tab (2) is selected, and then select the directory name (3).
On the directory page, select Applications. Azure AD displays a list of the applications currently installed in your tenancy.
Choose Add.
Select Add an application my organization is developing.
Enter the NAME of your application and specify the Type as WEB APPLICATION AND/OR WEB API.
Enter the appropriate App properties:
SIGN-ON URL. The URL where users can sign in and use your app. You can change this later as needed.
APP ID URI. The URI used as a unique logical identifier for your app. The URI must be in a verified custom domain for an external user to grant your app access to their data in Windows Azure AD. For example, if your Microsoft tenant is contoso.onmicrosoft.com, the APP ID URI could be https://app.contoso.onmicrosoft.com.
Your app is now registered with Azure AD, and has been assigned a client ID. However, there are several important aspects of your app left to configure.
Configure your application properties in Azure AD
Now that your application is registered, there are several important properties you must specify that determine how your application functions within Azure AD and how tenant admins will grant consent to allow your application to access their data by using the Office 365 Management APIs.
For more information about Azure AD application configuration in general, see Application Object Properties.
CLIENT ID. This value is automatically generated by Azure AD. Your application will use this value when requesting consent from tenant admins and when requesting app-only tokens from Azure AD.
APPLICATION IS MULTI-TENANT. This property must be set to YES to allow tenant admins to grant consent to your app to access their data by using the Office 365 Management APIs. If this property is set to NO, your application will only be able to access your own tenant's data.
REPLY URL. This is the URL that a tenant admin will be redirected to after granting consent to allow your application to access their data by using the Office 365 Management APIs. You can configure multiple reply URLs as needed. Azure automatically sets the first one to match the sign-on URL you specified when you created the application, but you can change this value as needed.
Be sure to choose Save after making any changes to these properties.
Generate a new key for your application
Keys, also known as client secrets, are used when exchanging an authorization code for an access token.
In the Azure Management Portal, select your application and choose Configure in the top menu. Scroll down to keys.
Select the duration for your key, and choose Save.
Azure displays the app secret only after saving it. Select the Clipboard icon to copy the client secret to the Clipboard.
Important
Azure only displays the client secret at the time you initially generate it. You cannot navigate back to this page and retrieve the client secret later.
Configure an X.509 certificate to enable service-to-service calls
An application that is running in the background, such as a daemon or service, can use client credentials to request app-only access tokens without repeatedly requesting consent from the tenant admin after initial consent is granted.
For more information, see Service to Service Calls Using Client Credentials.
You must configure an X.509 certificate with your application to be used as client credentials when requesting app-only access tokens from Azure AD. There are two steps to the process:
Obtain an X.509 certificate. You can use a self-signed certificate or a certificate issued by publicly trusted certificate authority.
Modify your application manifest to include the thumbprint and public key of your certificate.
The following instructions show you how to use the Visual Studio or Windows SDK makecert tool to generate a self-signed certificate and export the public key to a base64-encoded file.
From the command line, run the following:
Note
When you are generating the X.509 certificate, make sure the key length is at least 2048. Shorter key lengths are not accepted as valid keys.
Open the Certificates MMC snap-in and connect to your user account.
Find the new certificate in the Personal folder and export the public key to a base64-encoded file (for example, mycompanyname.cer). Your application will use this certificate to communicate with Azure AD, so make sure you retain access to the private key as well.
Note
You can use Windows PowerShell to extract the thumbprint and base64-encoded public key. Other platforms provide similar tools to retrieve properties of certificates.
From the Windows PowerShell prompt, type and run the following:
Store the values for
$base64Thumbprint,$base64Value, and$keyidto be used when you update your application manifest in the next set of steps.Using the values extracted from the certificate and the generated key ID, you must now update your application manifest in Azure AD.
In the Azure Management Portal, select your application and choose Configure in the top menu.
In the command bar, choose Manage manifest, and then choose Download Manifest.
Open the downloaded manifest for editing and replace the empty KeyCredentials property with the following JSON:
Note
The KeyCredentials property is a collection, making it possible to upload multiple X.509 certificates for rollover scenarios or delete certificates for compromise scenarios.
Save your changes and upload the updated manifest by choosing Manage manifest in the command bar, choosing Upload manifest, browsing to your updated manifest file, and then selecting it.
Specify the permissions your app requires to access the Office 365 Management APIs
Generate Dlp Client Bypass Key Switch
Finally, you need to specify exactly what permissions your app requires of the Office 365 Management APIs. To do so, you add access to the Office 365 Management APIs to your app, and then you specify the permission(s) you need.
In the Azure Management Portal, select your application, and choose Configure in the top menu. Scroll down to permissions to other applications, and choose Add application.
Select the Office 365 Management APIs (1) so that it appears in the Selected column (2), and then select the check mark in the lower right (3) to save your selection and return to the main configuration page for your application.
The Office Management APIs now appear in the list of applications to which your application requires permissions. Under both Application Permissions and Delegated Permissions, select the permissions your application requires. Refer to the specific API reference for more details about each permission.
Note
There are currently four unused permissions related to activity reports and threat intelligence that will be removed in the future. Do not select any of these permissions because they are unnecessary.
Choose Save to save the configuration.
Get Office 365 tenant admin consent
Now that your application is configured with the permissions it needs to use the Office 365 Management APIs, a tenant admin must explicitly grant your application these permissions in order to access their tenant's data by using the APIs. To grant consent, the tenant admin must sign in to Azure AD by using the following specially constructed URL, where they can review your application's requested permissions. This step is not required when using the APIs to access data from your own tenant.
The redirect URL must match or be a sub-path under one of the Reply URLs configured for your application in Azure AD.
For example:
You can test the consent URL by pasting it into a browser and signing in using the credentials of an Office 365 admin for a tenant other than the tenant that you used to register the application. You will see the request to grant your application permission to use the Office Management APIs.
After choosing Accept, you are redirected to the specified page, and there will be a code in the query string.
For example:
Your application uses this authorization code to obtain an access token from Azure AD, from which the tenant ID can be extracted. After you have extracted and stored the tenant ID, you can obtain subsequent access tokens without requiring the tenant admin to sign in.
Request access tokens from Azure AD
There are two methods for requesting access tokens from Azure AD:
The Authorization Code Grant Flow involves a tenant admin granting explicit consent, which returns an authorization code to your application. Your application then exchanges the authorization code for an access token. This method is required to obtain the initial consent that your application needs to access the tenant data by using the API, and this first access token is needed in order to obtain and store the tenant ID.
The Client Credentials Grant Flow allows your application to request subsequent access tokens as old ones expire, without requiring the tenant admin to sign in and explicitly grant consent. This method must be used for applications that run continuously in the background calling the APIs once the initial tenant admin consent has been granted.
Request an access token using the authorization code
After a tenant admin grants consent, your application receives an authorization code as a query string parameter when Azure AD redirects the tenant admin to your designated URL.
 Also, this version also contains a set up that discovers all drivers that is suitable for your system. A simple click will display a list of concerning all corrupt or outdated drivers.
Also, this version also contains a set up that discovers all drivers that is suitable for your system. A simple click will display a list of concerning all corrupt or outdated drivers.
Your application makes an HTTP REST POST to Azure AD to exchange the authorization code for an access token. Because the tenant ID is not yet known, the POST will be to the 'common' endpoint, which does not have the tenant ID embedded in the URL:
The body of the POST contains the following:
Sample request
The body of the response will include several properties, including the access token.
Sample response
The access token that is returned is a JWT token that includes information about both the admin that granted consent and the application requesting access. The following shows an example of an un-encoded token. Your application must extract the tenant ID 'tid' from this token and store it so that it can be used to request additional access tokens as they expire, without further admin interaction.
Sample token
Request an access token by using client credentials
After the tenant ID is known, your application can make service-to-service calls to Azure AD to request additional access tokens as they expire. These tokens include information only about the requesting application and not about the admin that originally granted consent. Service-to-service calls require that your application use an X.509 certificate to create client assertion in the form of a base64-encoded, SHA256 signed JWT bearer token.
When you are developing your application in .NET, you can use the Azure AD Authentication Library (ADAL) to create client assertions. Other development platforms should have similar libraries.
Generate Dlp Client Bypass Key Not Working
An un-encoded JWT token consists of a header and payload that have the following properties.
Sample JWT token
The client assertion is then passed to Azure AD as part of a service-to-service call to request an access token. When using client credentials to request an access token, use an HTTP POST to a tenant-specific endpoint, where the previously extracted and stored tenant ID is embedded in the URL.
Generate Dlp Client Bypass Key Card
The body of the POST contains the following:
Generate Dlp Client Bypass Key Fob
Sample request
The response will be the same as before, but the token will not have the same properties, because it does not contain properties of the admin that granted consent.
Sample response
Sample access token
Build your app
Now that you have registered your app in Azure AD and configured it with the necessary permissions, you're ready to build your app. The following are some of the key aspects to consider when designing and building your app:
The consent experience. To obtain consent from your customers, you must direct them in a browser to the Azure AD website, using the specially constructed URL described previously, and you must have a website to which Azure AD will redirect the admin once they grant consent. This website must extract the authorization code from the URL and use it to request an access token from which it can obtain the tenant ID.
Store the tenant ID in your system. This will be needed when requesting access tokens from Azure AD and when calling the Office Management APIs.
Managing access tokens. You will need a component that requests and manages access tokens as needed. If your app calls the APIs periodically, it can request tokens on demand, or if it calls the APIs continuously to retrieve data, it can request tokens at regular intervals (for example, every 45 minutes).
Implement a webhook listener as needed by the particular API you are using.
Data retrieval and storage. You'll need a component that retrieves data for each tenant, either by using continuous polling or in response to webhook notifications, depending on the particular API you are using.