Several tools exist to generate SSH public/private key pairs. The following sections show how to generate an SSH key pair on UNIX, UNIX-like and Windows platforms.
Generating an SSH Key Pair on UNIX and UNIX-Like Platforms Using the ssh-keygen Utility
May 17, 2019 The command generates an SSH key pair consisting of a public key and a private key, and saves them in the specified path. The file name of the public key is created automatically by appending.pub to the name of the private key file. For example, if the file name of the SSH private key is idrsa, then the file name of the public key would be pub. Jan 22, 2019 Today I'll show you how to generate SSH keys. Generate SSH key with ssh-keygen. Ssh-keygen is a standard utility supplied with SSH package. If you have ssh command on your system, you probably have the ssh-keygen command as well. Without any command line options, ssh-keygen will ask you a few questions and create the key with default settings.
UNIX and UNIX-like platforms (including Solaris and Linux) include the ssh-keygen utility to generate SSH key pairs.
- Navigate to your home directory:
- Run the ssh-keygen utility, providing as
filenameyour choice of file name for the private key:The ssh-keygen utility prompts you for a passphrase for the private key.
- Enter a passphrase for the private key, or press Enter to create a private key without a passphrase:
Note:
While a passphrase is not required, you should specify one as a security measure to protect the private key from unauthorized use. When you specify a passphrase, a user must enter the passphrase every time the private key is used.
The ssh-keygen utility prompts you to enter the passphrase again.
- Enter the passphrase again, or press Enter again to continue creating a private key without a passphrase:
- The ssh-keygen utility displays a message indicating that the private key has been saved as
filenameand the public key has been saved asfilename.pub. It also displays information about the key fingerprint and randomart image.
Generating an SSH Key Pair on Windows Using the PuTTYgen Program
The PuTTYgen program is part of PuTTY, an open source networking client for the Windows platform.
- Download and install PuTTY or PuTTYgen.
To download PuTTY or PuTTYgen, go to http://www.putty.org/ and click the You can download PuTTY here link.
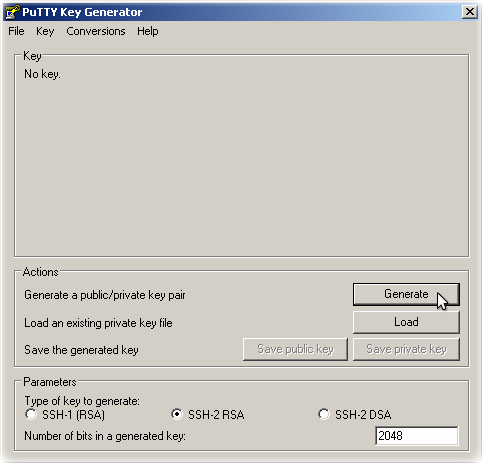
- Run the PuTTYgen program.
- Set the Type of key to generate option to SSH-2 RSA.
- In the Number of bits in a generated key box, enter 2048.
- Click Generate to generate a public/private key pair.
As the key is being generated, move the mouse around the blank area as directed.
- (Optional) Enter a passphrase for the private key in the Key passphrase box and reenter it in the Confirm passphrase box.
Note:
While a passphrase is not required, you should specify one as a security measure to protect the private key from unauthorized use. When you specify a passphrase, a user must enter the passphrase every time the private key is used.
- Click Save private key to save the private key to a file. To adhere to file-naming conventions, you should give the private key file an extension of
.ppk(PuTTY private key).Note:
The.ppkfile extension indicates that the private key is in PuTTY's proprietary format. You must use a key of this format when using PuTTY as your SSH client. It cannot be used with other SSH client tools. Refer to the PuTTY documentation to convert a private key in this format to a different format. - Select all of the characters in the Public key for pasting into OpenSSH authorized_keys file box.
Make sure you select all the characters, not just the ones you can see in the narrow window. If a scroll bar is next to the characters, you aren't seeing all the characters.
- Right-click somewhere in the selected text and select Copy from the menu.
- Open a text editor and paste the characters, just as you copied them. Start at the first character in the text editor, and do not insert any line breaks.
- Save the text file in the same folder where you saved the private key, using the
.pubextension to indicate that the file contains a public key. - If you or others are going to use an SSH client that requires the OpenSSH format for private keys (such as the
sshutility on Linux), export the private key:- On the Conversions menu, choose Export OpenSSH key.
- Save the private key in OpenSSH format in the same folder where you saved the private key in
.ppkformat, using an extension such as.opensshto indicate the file's content.
A step-by-step guide for enabling EFS keystore access while OpenSSH Public Key Authentication is used
Mac Generate Ssh Key
What is EFS?
In general, the Encrypted Files System (EFS) support on AIX enables individual users on the system to encrypt their data and also access it through keyed protection. Users will be able to setup keys and assign a default key for EFS. These keys are stored in cryptographically protected key store and upon successful login, the user's keys are loaded into the kernel and associated with the kernel processes.
Private keys are associated to users and groups. These keys are stored in keystores and are protected by passwords. A user keystore contains the user's private key and also password to open the user's group keystores; the group keystores contain the groups' private keys. Forza horizon 3 cd key generator.
When a process opens a keystore, either at user login time or using a specific EFS user command, the keys contained in this keystore (and related keystores) are loaded in the kernel and associated with the process credentials. Later on,when the process needs to open an EFS protected file, these credentials are tested. If a key matching the file protection is found, then the process is able to decrypt the file key and therefore the file content.
Keystore creation or opening can happen at login time, by the way of an EFS LAM (old) or PAM (new) module. These modules, as well as the commands (for example, chmod) make calls to some EFS APIs provided by a libefs.a library. Two user commands exist, efsmgr and efskeymgr, to give some control over EFS to the user and administrator.
How to setup Public Key Authentication in OpenSSH
Create a user on the client side and generate keys for this user. Public-private key pairs can be generated using the ssh-keygen command.
- On the client side, go to /etc/ssh/ssh_config file and set PubkeyAuthentication yes.
On the server side, go to /etc/ssh/sshd_config file to set PubkeyAuthentication yes.
- Configure OpenSSH server and client to use EFS logon while Public Key Authentication.
On the client side, go to /etc/ssh/ssh_config file and set 'AllowPKCS12keystoreAutoOpen yes'.
On the server side, go to /etc/ssh/sshd_config file and set 'AllowPKCS12keystoreAutoOpen yes'.
- Restart the server:
Generate keys with the following command using a user created as follows:
The command ssh-keygen prompts for passphrase. This passphrase will be used to encrypt the private-key file on the client side. Even ssh-keygen command will accept the empty passphrase, in which case, private-key file will not be encrypted.
Copy the public keys on to the server in the file ~/.ssh/authorized_keys.
How to generate rsa key pair. May 31, 2015 Configure SSH key based authentication on rhel 7/centos 7 Posted on May 31, 2015 December 16, 2016 by Vishwanath Mule In this post I am going to show you how to configure SSH key based authentication on rhel7/centos7. I need a way to generate an RSA asymmetrical key pair in Swift. I don't need to store it in the keychain or anything. I just need to generate a key pair and shove both keys into String variables. The keys do need to be compatible with PHP on the other end. I will use symmetrical encryption to secure the private key and store it on the phone. Aug 19, 2019 1. Start by logging into the source machine (local server) and creating a 2048-bit RSA key pair using the command: ssh-keygen -t rsa. If you want to tighten up security measures, you can create a 4096-bit key by adding the -b 4096 flag: ssh-keygen -t rsa -b 4096. After entering the command, you should see the following prompt. Apr 02, 2019 Step One: Creation of the RSA Key Pair. The first step in the installation process is to create the key pair on the client machine, which would, more often than not, be your own system. Users need to use the following command: ssh-keygen -o -b 4096 -t rsa. The above command kicks off the SSH Key installation process for users.
Similarly, any number of a Client user's public key can be copied in the file ~/.ssh/authorized_keys file on server user account.
AIX EFS Configurations
EFS has to be enabled on the server side using the efsenable command. This creates an admin keystore. The keystore gets created for a user in two cases.
- Whenever a new user is created.
- When passwd is assigned to the user or when user logs in.
The path where user keystore gets created on the system is /var/efs/users/<userlogin>/keystore.
The format of user keystore is in PKCS#12 which contains public and private objects. Private objects are protected by user access key. This user access key is nothing but a hash of a user-defined password (either login password or another password specific to EFS).
Public key cookie needs to be created and inserted into the keystore on server side. User invokes the efskeymgr command to insert the cookie. A public key cookie is the passwd encrypted with users public key.
The following steps show how to create a keystore for a user and insert the public key cookies.
When all the previous configuration setting are complete, run the ssh to log onto the remote machine using the public key authentication.
Run the following command to log on to the remote machine:
- Once the connection is established and public key authentication is successful, the ssh server checks if AllowPKCS12keystoreAutoOpen is set to 'yes' in the sshd_config file. If so, it sends the ssh client a data packet.
- The ssh client, on receiving this data packet, checks if the same option is enabled on the client side. That is, the ssh client is configured for this feature by checking if the AllowPKCS12keystoreAutoOpen is set to yes in the ssh_config file. If enabled, the client sends an acknowledgement to the server saying that it too supports this feature.
- On receiving the ACK from the ssh client, the sshd opens the user's efs keystore in /var/efs/user/<username>/keystore and reads the publickey cookie SSHPub(AK) and sends it to ssh client.
- The ssh client, on receiving the SSHPub from server, decrypts it with its private key and sends the accesskey(AK) back to server. With AK, sshd will open the user's private part of the user's keystore and call the EFS kernel extension to push this opened keystore into the kernel and associate it with the user's log on process.
Verify the authentication and EFS login
The OpenSSH client user ram is all set for Public Key authentication to user laxman on the OpenSSH server with EFS login. Verify the same with ssh login from client:
Applications for this setup
This setup can be used along with DB2 UDB DPF for which OpenSSH public key authentication can be used. The DB2 tables are encrypted using EFS.
Troubleshooting
Check if all the configurations listed above have been performed. Check if the public key cookie is inserted properly byefskeymgr command by verifying the keystore file size before and after the insertion. Enable debug for sshd and check if any failures. Also, verify once with password authentication if the account login and efs login succeed.
Downloadable resources
Related topics
Generate Public Ssh Key Aix 10
- Learn more about OpenSSH.
- You can download IBM version of OpenSSH for AIX.
- EFS on AIX : Learn more about EFS filesystem on AIX 6.1.