- Generate Rsa Key Cisco Switch
- Create Rsa Key Cisco Router
- Create Rsa Keys Cisco
- Generate Rsa Key Cisco 3750 Password
Contents
Hi When i'm trying to SSH to my 3750 switch i get the following error: Unable to negotiate with 192.168.1.250 port 22: no matching key exchange method found. Their offer: diffie-hellman-group1-sha1 I tried to use the command ip ssh dh min size 4096, but my switch doesn't know it. Here is the confi. Switch (config)# crypto key generate rsa Enables the SSH server for local and remote authentication on the switch and generates an RSA key pair. Generating an RSA key pair for the switch automatically enables SSH. We recommend that a minimum modulus size of 1024 bits. When you generate RSA keys, you are prompted to enter a modulus length. Jul 22, 2015 Authenticating to Cisco devices using SSH and your RSA Public Key Using an RSA Public/Private key pair instead of a password to authenticate an SSH session is popular on Linux/Unix boxes. Digital Ocean, a Virtual Private Server (VPS) provider, has this advice on how you should log into their Droplets: 'you should use public key authentication. Would you like to learn how to enable Cisco SSH remote access using the command-line? In this tutorial, we are going to show you all the steps required to configure the SSH remote access on a Cisco Switch 2960 or 3750 using the command-line.
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest feature information and caveats, see the release notes for your platform and software release.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Prerequisites for Configuring the Switch for Secure Shell (SSH) and Secure Copy Protocol (SCP)
The following are the prerequisites for configuring the switch for secure shell (SSH):
- For SSH to work, the switch needs an RSA public/private key pair. This is the same with Secure Copy Protocol (SCP), which relies on SSH for its secure transport.
- Before enabling SCP, you must correctly configure SSH, authentication, and authorization on the switch.
- Because SCP relies on SSH for its secure transport, the router must have an Rivest, Shamir, and Adelman (RSA) key pair.
- SCP relies on SSH for security.
- SCP requires that authentication, authorization, and accounting (AAA) authorization be configured so the router can determine whether the user has the correct privilege level.
- A user must have appropriate authorization to use SCP.
- A user who has appropriate authorization can use SCP to copy any file in the Cisco IOS File System (IFS) to and from a switch by using the copy command. An authorized administrator can also do this from a workstation.
Restrictions for Configuring the Switch for SSH
The following are restrictions for configuring the switch for secure shell.
- The switch supports Rivest, Shamir, and Adelman (RSA) authentication.
- SSH supports only the execution-shell application.
- The SSH server and the SSH client are supported only on DES (56-bit) and 3DES (168-bit) data encryption software.
- The switch supports the Advanced Encryption Standard (AES) encryption algorithm with a 128-bit key, 192-bit key, or 256-bit key. However, symmetric cipher AES to encrypt the keys is not supported.
- This software release does not support IP Security (IPSec).
- When using SCP, you cannot enter the password into the copy command. You must enter the password when prompted.
Information about SSH
Secure Shell (SSH) is a protocol that provides a secure, remote connection to a device. SSH provides more security for remote connections than Telnet does by providing strong encryption when a device is authenticated. This software release supports SSH Version 1 (SSHv1) and SSH Version 2 (SSHv2).
SSH and Switch Access
For SSH configuration examples, see the “SSH Configuration Examples” section in the “Configuring Secure Shell” section in the “Other Security Features” chapter of the Cisco IOS Security Configuration Guide, Cisco IOS Release 12.4.
SSH functions the same in IPv6 as in IPv4. For IPv6, SSH supports IPv6 addresses and enables secure, encrypted connections with remote IPv6 nodes over an IPv6 transport.
Note | For complete syntax and usage information for the commands used in this section, see the command reference for this release and the “Secure Shell Commands” section of the “Other Security Features” chapter of the Cisco IOS Security Command Reference, Release 12.4 and the Cisco IOS IPv6 Command Reference. |
SSH Servers, Integrated Clients, and Supported Versions
The SSH feature has an SSH server and an SSH integrated client, which are applications that run on the switch. You can use an SSH client to connect to a switch running the SSH server. The SSH server works with the SSH client supported in this release and with non-Cisco SSH clients. The SSH client also works with the SSH server supported in this release and with non-Cisco SSH servers.
The switch supports an SSHv1 or an SSHv2 server.
The switch supports an SSHv1 client.
SSH supports the Data Encryption Standard (DES) encryption algorithm, the Triple DES (3DES) encryption algorithm, and password-based user authentication.
SSH also supports these user authentication methods:
- TACACS+
- RADIUS
- Local authentication and authorization
SSH Configuration Guidelines
Follow these guidelines when configuring the switch as an SSH server or SSH client:
- An RSA key pair generated by a SSHv1 server can be used by an SSHv2 server, and the reverse.
- If the SSH server is running on a stack master and the stack master fails, the new stack master uses the RSA key pair generated by the previous stack master.
- If you get CLI error messages after entering the crypto key generate rsa global configuration command, an RSA key pair has not been generated. Reconfigure the hostname and domain, and then enter the crypto key generate rsa command. For more information, see Related Topics below.
- When generating the RSA key pair, the message No host name specified might appear. If it does, you must configure a hostname by using the hostname global configuration command.
- When generating the RSA key pair, the message No domain specified might appear. If it does, you must configure an IP domain name by using the ip domain-name global configuration command.
- When configuring the local authentication and authorization authentication method, make sure that AAA is disabled on the console.
Secure Copy Protocol Overview
The Secure Copy Protocol (SCP) feature provides a secure and authenticated method for copying switch configurations or switch image files. SCP relies on Secure Shell (SSH), an application and a protocol that provides a secure replacement for the Berkeley r-tools.
For SSH to work, the switch needs an RSA public/private key pair. This is the same with SCP, which relies on SSH for its secure transport.
Because SSH also relies on AAA authentication, and SCP relies further on AAA authorization, correct configuration is necessary.
- Before enabling SCP, you must correctly configure SSH, authentication, and authorization on the switch.
- Because SCP relies on SSH for its secure transport, the router must have an Rivest, Shamir, and Adelman (RSA) key pair.
Note | When using SCP, you cannot enter the password into the copy command. You must enter the password when prompted. On the bottom of the window select Support. Kaspersky pure 3.0 activation key generator. |
Secure Copy Protocol Concepts
The Secure Copy Protocol (SCP) feature provides a secure and authenticated method for copying switch configurations or switch image files. SCP relies on Secure Shell (SSH), an application and a protocol that provides a secure replacement for the Berkeley r-tools.
To configure the Secure Copy feature, you should understand the SCP concepts.
The behavior of SCP is similar to that of remote copy (rcp), which comes from the Berkeley r-tools suite, except that SCP relies on SSH for security. SCP also requires that authentication, authorization, and accounting (AAA) authorization be configured so the router can determine whether the user has the correct privilege level.
For information about how to configure and verify SCP, see the “Secure Copy Protocol” section in the Cisco IOS Security Configuration Guide: Securing User Services, Release 12.4.
How to Configure SSH
Setting Up the Switch to Run SSH
Beginning in privileged EXEC mode, follow these steps to set up your switch to run SSH:
Before You BeginConfigure user authentication for local or remote access. This step is required. For more information, see Related Topics below.
SUMMARY STEPS1.configureterminal
2.hostnamehostname
3.ip domain-namedomain_name
4.crypto key generate rsa
5.end
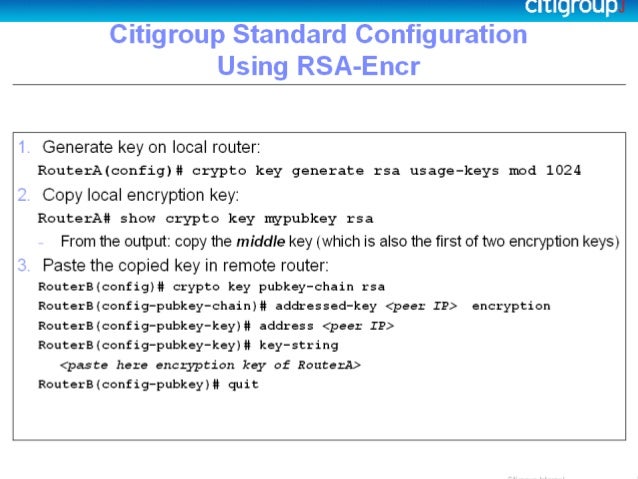
DETAILED STEPS
| Command or Action | Purpose | |||
|---|---|---|---|---|
| Step 1 | configureterminal Example: | Enters the global configuration mode. | ||
| Step 2 | hostnamehostname Example: | Configures a hostname and IP domain name for your switch.
| ||
| Step 3 | ip domain-namedomain_name Example: | Configures a host domain for your switch. | ||
| Step 4 | crypto key generate rsa Example: | Enables the SSH server for local and remote authentication on the switch and generates an RSA key pair. Generating an RSA key pair for the switch automatically enables SSH. We recommend that a minimum modulus size of 1024 bits. When you generate RSA keys, you are prompted to enter a modulus length. A longer modulus length might be more secure, but it takes longer to generate and to use.
| ||
| Step 5 | end Example: | Returns to privileged EXEC mode. |
Configuring the SSH Server
Beginning in privileged EXEC mode, follow these steps to configure the SSH server:
Note | This procedure is only required if you are configuring the switch as an SSH server. |
- transport input ssh
1.configureterminal
2.ip sshversion [12]
3.ip ssh {timeoutsecondsauthentication-retriesnumber}
4.Use one or both of the following:
5.end
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | configureterminal Example: | Enters the global configuration mode. |
| Step 2 | ip sshversion [12] Example: | (Optional) Configures the switch to run SSH Version 1 or SSH Version 2.
If you do not enter this command or do not specify a keyword, the SSH server selects the latest SSH version supported by the SSH client. For example, if the SSH client supports SSHv1 and SSHv2, the SSH server selects SSHv2. |
| Step 3 | ip ssh {timeoutsecondsauthentication-retriesnumber} Example: | Configures the SSH control parameters:
Repeat this step when configuring both parameters. |
| Step 4 | Use one or both of the following:
Example: or | (Optional) Configures the virtual terminal line settings.
|
| Step 5 | end Example: | Returns to privileged EXEC mode. |
Monitoring the SSH Configuration and Status
Command | Purpose |
|---|---|
show ip ssh | Shows the version and configuration information for the SSH server. |
show ssh | Shows the status of the SSH server. |
Generate Rsa Key Cisco Switch
For more information about these commands, see the “Secure Shell Commands” section in the “Other Security Features” chapter of the Cisco IOS Security Command Reference .
Additional References
Related Documents
| Related Topic | Document Title |
|---|---|
Configuring Identity Control policies and Identity Service templates for Session Aware networking. | Session Aware Networking Configuration Guide, Cisco IOS XE Release 3SE (Catalyst 3850 Switches) |
| Configuring RADIUS, TACACS+, Secure Shell, 802.1X and AAA. | Securing User Services Configuration Guide Library, Cisco IOS XE Release 3SE (Catalyst 3850 Switches) |
Error Message Decoder
| Description | Link |
|---|---|
To help you research and resolve system error messages in this release, use the Error Message Decoder tool. |
MIBs
| MIB | MIBs Link |
|---|---|
All supported MIBs for this release. | To locate and download MIBs for selected platforms, Cisco IOS releases, and feature sets, use Cisco MIB Locator found at the following URL: |
Create Rsa Key Cisco Router
Technical Assistance
| Description | Link |
|---|---|
The Cisco Support website provides extensive online resources, including documentation and tools for troubleshooting and resolving technical issues with Cisco products and technologies. To receive security and technical information about your products, you can subscribe to various services, such as the Product Alert Tool (accessed from Field Notices), the Cisco Technical Services Newsletter, and Really Simple Syndication (RSS) Feeds. Access to most tools on the Cisco Support website requires a Cisco.com user ID and password. |
Hi,
Are you aware of any inbound ACLs applied on the VTY lines? Maybe do a show access-list, show ip interface and show run commands to check if an ACL is blocking access on the terminal lines.
If its not an ACL issue, make sure you configured 'login local' on your VTY lines to make use of the local database when connecting in
Create Rsa Keys Cisco
Check also that you have not disabled SSH access into your VTY lines using the transport command.
Make sure 'transport input ssh telnet' or 'transport input telnet ssh' has been configured
Generate Rsa Key Cisco 3750 Password
Failing all that it could be an exec-timeout issue, maybe that has been set to low and its automatically logging you out, although this is more unlikely based on your report.