Generate Ssh Public Key Cygwin 4,6/5 9809 reviews
Feb 04, 2014 Install and start an SSH server on your Linux machine. Start the cygwin shell. Replace linuxuser with your user name on the linux machine and replace linuxmachine with the Linux computer name or IP address.Note that you will need to enter the password. How to generate an SSH key and add your public key to the server for authentication. Development Comments ( 2 ) SSH keys are a way to identify trusted computers, without involving passwords. The steps below will walk you through generating an SSH key and adding the public key to the server. First, check for existing SSH keys on your computer. Ssh-keygen is a tool for creating new authentication key pairs for SSH. Such key pairs are used for automating logins, single sign-on, and for authenticating hosts. SSH Keys and Public Key Authentication. The SSH protocol uses public key cryptography for authenticating hosts and users. Jul 16, 2014 OpenSSH - Using RSA Public Keys for SSH Connection (ssh-keygen, ssh-copy-id, ssh- keyscan) - Duration: 6:12. CodeCowboyOrg 37,713 views.
- Powershell Generate Ssh Key
- Ssh Public Key File
Linux > TOOLS > SFTP > CREATE SFTP SERVER using CYGWINThis blog is useful for you if :1. You want to setup SFTP on Windows 2. If you want to restrict user to a directory on SFTP (using openssh)
Some background inforamtion :What is SFTP read here What is OpenSSH read here What is cygwin read here Content- Install SFTP-server, Cygwin with OpenSSH
- Configure home-directory
- Configure SSH-server
- Start the SSH-service
- Generate SSH-keys
- Test login to SFTP-server
- Uninstall the SSH-service
- Restrict User to a directory
Install SFTP-server, Cygwin with OpenSSH- Download setup.exe from http://www.cygwin.com/ and save the file to 'c:cygwincygwin.install' (you will have to 1. create the directory).
- Run setup.exe and follow instructions below:
Configure home-directory
Note: This step is necessary if roaming profiles are used in Windows.
1. Start Cygwin
2. Open 'c:cygwinetcpasswd' with a text editor (Notepad for example)
3. In passwd, change home-dir from '/home' to 'C:Documents and Settings' (example below for user id:
dfc0364).
Change:
dfc0364:unused_by.....-1851:/home/dfc0364:/bin/bash
to:
dfc0364:unused_by.....-1851:/cygdrive/c/Documents and Settings/dfc0364:/bin/bash
1. Close Cygwin
Configure SSH-server
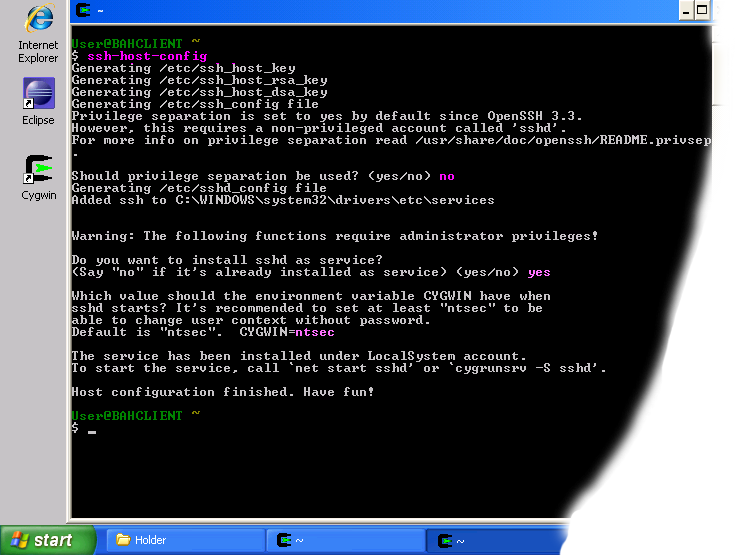
Configure the SSH-server (sshd) in a Cygwin window:
$ ssh-host-config
*** Info: Generating /etc/ssh_host_key
*** Info: Generating /etc/ssh_host_rsa_key
*** Info: Generating /etc/ssh_host_dsa_key
*** Info: Creating default /etc/ssh_config file
*** Info: Creating default /etc/sshd_config file
*** Info: Privilege separation is set to yes by default since OpenSSH 3.3.
*** Info: However, this requires a non-privileged account called 'sshd'.
*** Info: For more info on privilege separation read /usr/share/doc/openssh/README.privsep.
*** Query: Should privilege separation be used? (yes/no) yes
*** Info: Updating /etc/sshd_config file
*** Warning: The following functions require administrator privileges!
*** Query: Do you want to install sshd as a service?
*** Query: (Say 'no' if it is already installed as a service) (yes/no) yes
*** Info: Note that the CYGWIN variable must contain at least 'ntsec'
*** Info: for sshd to be able to change user context without password.
*** Query: Enter the value of CYGWIN for the daemon: [ntsec]
*** Info: The sshd service has been installed under the LocalSystem
*** Info: account (also known as SYSTEM). To start the service now, call
*** Info: `net start sshd' or `cygrunsrv -S sshd'. Otherwise, it
*** Info: will start automatically after the next reboot.
*** Info: Host configuration finished. Have fun!
InstallationGuideCygwinSetup - soi-toolkit - Cygwin setup for SFTP-s.. http://code.google.com/p/soi-
toolkit/wiki/InstallationGuideCygwinSetup
Start the SSH-service
Start the SSH-server (sshd) in a Cygwin window:
$ cygrunsrv --start sshd
Generate SSH-keys
Note: Remember your passphrase, you will have to configure it in your service components security-property-file in order to connect to your
local SFTP-server.
Generate the SSH-keys to use for public-key cryptography in a Cygwin window:
$ ssh-keygen -t dsa
Generating public/private dsa key pair.
Enter file in which to save the key (/cygdrive/c/Documents and Settings/dfc0364/.ssh/id_dsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /cygdrive/c/Documents and Settings/dfc0364/.ssh/id_dsa.
Your public key has been saved in /cygdrive/c/Documents and Settings/dfc0364/.ssh/id_dsa.pub.
The key fingerprint is:
07:5c:3f:f6:8e:b5:91:de:02:5c:c3:c8:3a:04:3f:aa dfc0364@dse31673
The key's randomart image is:
+--[ DSA 1024]----+
. .
. + o o
o + * +
+ = + o
S + o =
. . . * +
E . = .
.
+-----------------+
dfc0364@dse31673 ~
$ cat ~/.ssh/id_dsa.pub >> ~/.ssh/authorized_keys2
Test login to SFTP-server
Test to login to your local SFTP-server in a Cygwin window (example for user id: dfc0364):
$ sftp dfc0364@localhost
Connecting to localhost..
Enter passphrase for key '/cygdrive/c/Documents and Settings/dfc0364/.ssh/id_dsa':
sftp> exit
Uninstall the SSH-service
If you want to uninstall the SSH-service, open up Cygwin and execute commands:
cygrunsrv --stop sshd
cygrunsrv --remove sshd
Restrict User to a directory
Open etc folder in your cygwin installation. Two file need a edit to to implement chroot jail for user.
1. sshd_config
2. passwd
in sshd_config change below conigurtions
# override default of no subsystems
Subsystem sftp internal-sftp
ChrootDirectory /cygdrive/d/inetpub/ftproot
# Example of overriding settings on a per-user basis
Match User administrators
X11Forwarding no
AllowTcpForwarding no
ForceCommand internal-sftp
in passwd file
manually edit root user to change the group id (usually 544) to 0
for example as below :
SvcCOPSSH:unused_by_nt/2000/xp:0:545:U-WINDOWS-AU90FH5SvcCOPSSH,S-1-5-21-2943273595-299576109-709065550-1031:/var/:/bin/false
Restart OPENSSH service and Enjoy ! |
|
< Cryptography

Download and install the OpenSSL runtimes. If you are running Windows, grab the Cygwin package.
OpenSSL can generate several kinds of public/private keypairs.RSA is the most common kind of keypair generation.[1]Parallels desktop 13 activation key generator download.
Other popular ways of generating RSA public key / private key pairs include PuTTYgen and ssh-keygen.[2][3]
Generate an RSA keypair with a 2048 bit private key[edit]
Execute command: 'openssl genpkey -algorithm RSA -out private_key.pem -pkeyopt rsa_keygen_bits:2048'[4] (previously “openssl genrsa -out private_key.pem 2048”)
e.g.
Make sure to prevent other users from reading your key by executing chmod go-r private_key.pem afterward.
Extracting the public key from an RSA keypair[edit]
Execute command: 'openssl rsa -pubout -in private_key.pem -out public_key.pem'
e.g.
A new file is created, public_key.pem, with the public key.
It is relatively easy to do some cryptographic calculations to calculate the public key from the prime1 and prime2 values in the public key file.However, OpenSSL has already pre-calculated the public key and stored it in the private key file.So this command doesn't actually do any cryptographic calculation -- it merely copies the public key bytes out of the file and writes the Base64 PEM encoded version of those bytes into the output public key file.[5]
Viewing the key elements[edit]
Execute command: 'openssl rsa -text -in private_key.pem'
All parts of private_key.pem are printed to the screen. This includes the modulus (also referred to as public key and n), public exponent (also referred to as e and exponent; default value is 0x010001), private exponent, and primes used to create keys (prime1, also called p, and prime2, also called q), a few other variables used to perform RSA operations faster, and the Base64 PEM encoded version of all that data.[6](The Base64 PEM encoded version of all that data is identical to the private_key.pem file).
Password-less login[edit]
Often a person will set up an automated backup process that periodically backs up all the content on one 'working' computer onto some other 'backup' computer.
Because that person wants this process to run every night, even if no human is anywhere near either one of these computers, using a 'password-protected' private key won't work -- that person wants the backup to proceed right away, not wait until some human walks by and types in the password to unlock the private key.Many of these people generate 'a private key with no password'.[7]Some of these people, instead, generate a private key with a password,and then somehow type in that password to 'unlock' the private key every time the server reboots so that automated toolscan make use of the password-protected keys.[8][3]
Further reading[edit]
Powershell Generate Ssh Key
- ↑Key Generation
- ↑Michael Stahnke.'Pro OpenSSH'.p. 247.
- ↑ ab'SourceForge.net Documentation: SSH Key Overview'
- ↑'genpkey(1) - Linux man page'
- ↑'Public – Private key encryption using OpenSSL'
- ↑'OpenSSL 1024 bit RSA Private Key Breakdown'
- ↑'DreamHost: Personal Backup'.
- ↑Troy Johnson.'Using Rsync and SSH: Keys, Validating, and Automation'.
- Internet_Technologies/SSH describes how to use 'ssh-keygen' and 'ssh-copy-id' on your local machine so you can quickly and securely ssh from your local machine to a remote host.
Ssh Public Key File
Retrieved from 'https://en.wikibooks.org/w/index.php?title=Cryptography/Generate_a_keypair_using_OpenSSL&oldid=3622149'

