- How To Generate Ssh Keys
- Please Generate Rsa Keys To Enable Ssh File
- Please Generate Rsa Keys To Enable Ssh On Windows 7
Introduction
So, in short: if your router has RSA keys generated, but won't enable SSHv2, enable SSH with the name of the RSA keys, like so: ip ssh rsa keypair-name and then. No ip ssh version 1 Thankfully, this was a lab setup so no SSHv1 traffic was publicly sent, and no actual passwords were used, so mitigation from using a bad SSH version was.
This document describes how to generate a private secure shell (SSH) key and use that for username and authentication when logging into the command line interface (CLI) on the Cisco Email Security Appliance (ESA).
How to configure SSH Public Key Authentication for login to the ESA without a password
Oct 02, 2015 SSH Config and crypto key generate RSA command. Use this command to generate RSA key pairs for your Cisco device (such as a router). Keys are generated in pairs–one public RSA key and one private RSA key. If your router already has RSA keys when you issue this command, you will be warned and prompted to replace the existing keys with new keys. Nov 23, 2011 Hi, i have a switch 2960 24TC-L with c2960-lanbasek9-mz.150-1.SE.bin and SSH v1 enabled. When i try to enable SSH v2 the swith tell me that i have to create a crypto key rsa. I generated the crypto key rsa with 1024 bits and when i try to enable the SSH v2 i receive the same message.
Public-key authentication (PKI) is an authentication method that relies on a generated public/private keypair. With PKI, a special 'key' is generated which has a very useful property: Anyone who can read the public half of the key is able encrypt data which can then only be read by a person who has access to the private half of the key. In this way, having access to the public half of a key allows you to send secret information to anyone with the private half, and to also verify that a person does in fact have access to the private half. It's easy to see how this technique could be used to authenticate.
As a user, you can generate a keypair and then place the public half of the key on a remote system, such as your ESA. That remote system is then able to authenticate your user ID, and allow you to login just by having you demonstrate that you have access to the private half of the keypair. This is done at the protocol level inside SSH and happens automatically.
It does, however, mean that you need to protect the privacy of the private key. On a shared system where you do not have root this can be accomplished by encrypting the private key with a passphrase, which functions similarly to a password. Before SSH can read your private key in order to perform the public key authentication you'll be asked to supply the passphrase so that the private key can be decrypted. On more secure systems (like a machine where you are the only user, or a machine at your home where no strangers will have physical access) you can simplify this process either by creating an unencrypted private key (with no passphrase) or by entering your passphrase once and then caching the key in memory for the duration of your time at the computer. OpenSSH contains a tool called ssh-agent which simplifies this process.
ssh-keygen example for Linux/Unix
Complete the following steps to set up your a linux/unix workstation (or server) to connect to the ESA without a password. In this example, we will not specify as passphrase.
1) On your workstation (or server), generate a private key using the Unix command ssh-keygen:
(*the above was generated from an Ubuntu 14.04.1)
2) Open the public key file (id_rsa.pub) created in #1 and copy the output:
3) Login to your appliance and configure your ESA to recognize your workstation (or server) using the public SSH key that you created in #1, and commit the changes. Notice the password prompt during login:
Download now the serial number for Adobe Acrobat 9 Pro Extended. All serial numbers are genuine and you can find more results in our database for Adobe software. Updates are issued periodically and new results might be added for this applications from our community. Serial key for Adobe Acrobat 9.0 Pro Extended can be found and viewed here. We have the largest serial numbers data base. Don't add serial, keygen and so on to the search. Adobe Acrobat 9.0 Pro Extended serial number Rating 9.8 of 10 based on 629 user revies added to. Adobe acrobat 9 pro extended serial key generator. May 24, 2016 Adobe Acrobat 9 Pro Extended 1857 5164. Serialkey preview: 1380-1601-7539-9354-7032-1203 Leechers - Hackforums, Warezscene OR Serial: 1380-1601-7539-9354-7032-1203 OR 1380-1252-5771-0240-050-1709-6831-9981-4579-5085 1380-1. Added: Downloaded: 7444 times Rating: 26%.
4) Exit out of the appliance, and re-login. Notice the password prompt is removed, and access is directly granted:
ssh-keygen example for Windows
How To Generate Ssh Keys
Complete the following steps to set up your a Windows workstation (or server) to connect to the ESA without a password. In this example, we will not specify as passphrase.
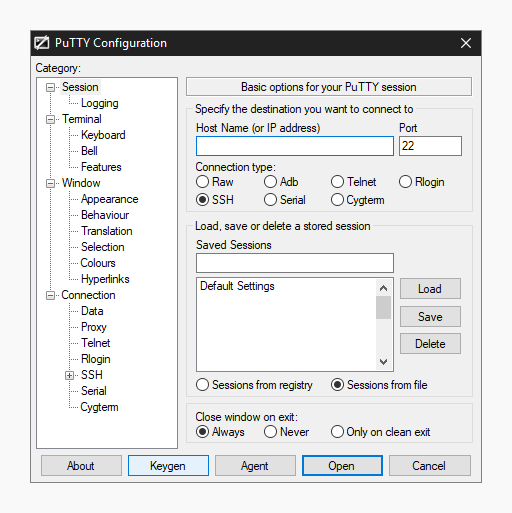
Note: There are a variation on console application used from Windows. You will need to research and find the solution that works best for your console application. This example will use PuTTy and PuTTyGen.
1) Open PuttyGen.
2) For Type of key to generate, select SSH-2 RSA.
3) Click the Generate button.
4) Move your mouse in the area below the progress bar. When the progress bar is full, PuTTYgen generates your key pair.
5) Type a passphrase in the Key passphrase field. Type the same passphrase in the Confirm passphrase field. You can use a key without a passphrase, but this is not recommended.
6) Click the Save private key button to save the private key.
Note: You must save the private key. You will need it to connect to your machine.
7) Right-click in the text field labeled Public key for pasting into OpenSSH authorized_keys file and choose Select All.
8) Right-click again in the same text field and choose Copy.
9) Using PuTTY, login to your appliance and configure your ESA to recognize your Windows workstation (or server) using the public SSH key that you saved and copied from #6 - #8, and commit the changes. Notice the password prompt during login:
10) From the PuTTy configuration window, and your pre-existing Saved Session for your ESA, choose Connection > SSH > Auth and in the Private key file for authentication field, click Browse and find your saved private key from step #6.
11) Save the Session (profile) in PuTTY, and click Open. Login with the username, if not already saved or specified from the pre-configured Session. Notice the inclusion of 'Authenticating with public key '[FILE NAME OF SAVED PRIVATE KEY]' when logging in:
Related Information
SSH keys are a way to identify trusted computers, without involving passwords. The steps below will walk you through generating an SSH key and adding the public key to the server.
Step 1: Check for SSH Keys
Please Generate Rsa Keys To Enable Ssh File
First, check for existing SSH keys on your computer. Open Git Bash, Cygwin, or Terminal, etc. and enter:
Check the directory listing to see if you already have a public SSH key. By default, the filenames of the public keys are one of the following:
- id_dsa.pub
- is_ecdsa.pub
- id_ed25519.pub
- id_rsa.pub
If you see an existing public and private key pair listed (for example id_rsa.pub and id_rsa) that you’d like to use, you can skip Step 2 and go straight to Step 3.
Step 2: Generate a new SSH key
With your command line tool still open, enter the text shown below. Make sure you substitute in your email address:
You’ll be asked to enter a passphrase, or simply press Enter to not enter a passphrase:
After you enter a passphrase (or just press Enter twice), review the fingerprint, or ‘id’ of your SSH key:
Step 3: Add your key to the ssh-agent
To configure the ssh-agent program to use your SSH key, first ensure ssh-agent is enabled.
If you are using Git Bash, turn on the ssh-agent with command shown below instead:
Please Generate Rsa Keys To Enable Ssh On Windows 7

Then, add your SSH key to the ssh-agent:
Google reCAPTCHAGoogle reCAPTCHA ensures that a human being, rather than a computer, is interacting with the site. Google recaptcha v2 generate key generator.
Step 4: Add your SSH key to the server
To add your public SSH key to the server, you’ll copy the public SSH key you just created to the server. Substitute “username” with your username on the server, and “server.address.com” with the domain address or IP address of your server:
The server will then prompt you for your password:
That’s it! You should now be set up to connect to the server without having to authenticate.