Mar 17, 2018 This is the best version of ARMA 2 CD-Key Generator.ARMA 2 Cd key generator updated latest working tool online.Get ARMA 2 Redeem Code Generator on PC, Xbox One, PS4, It is going to take time to generate unique ARMA 2 redeem key.ARMA 2 Key Generator. Hi everybody, and that’s why we decided to share with you ARMA 2 Key Generator. Arma 2 reinforcements cd key generator v1 2.
- Generate Aws_access_key_id And Aws_secret_access_key Data
- Generate Aws_access_key_id And Aws_secret_access_key Text
- Generate Aws_access_key_id And Aws_secret_access_key Free
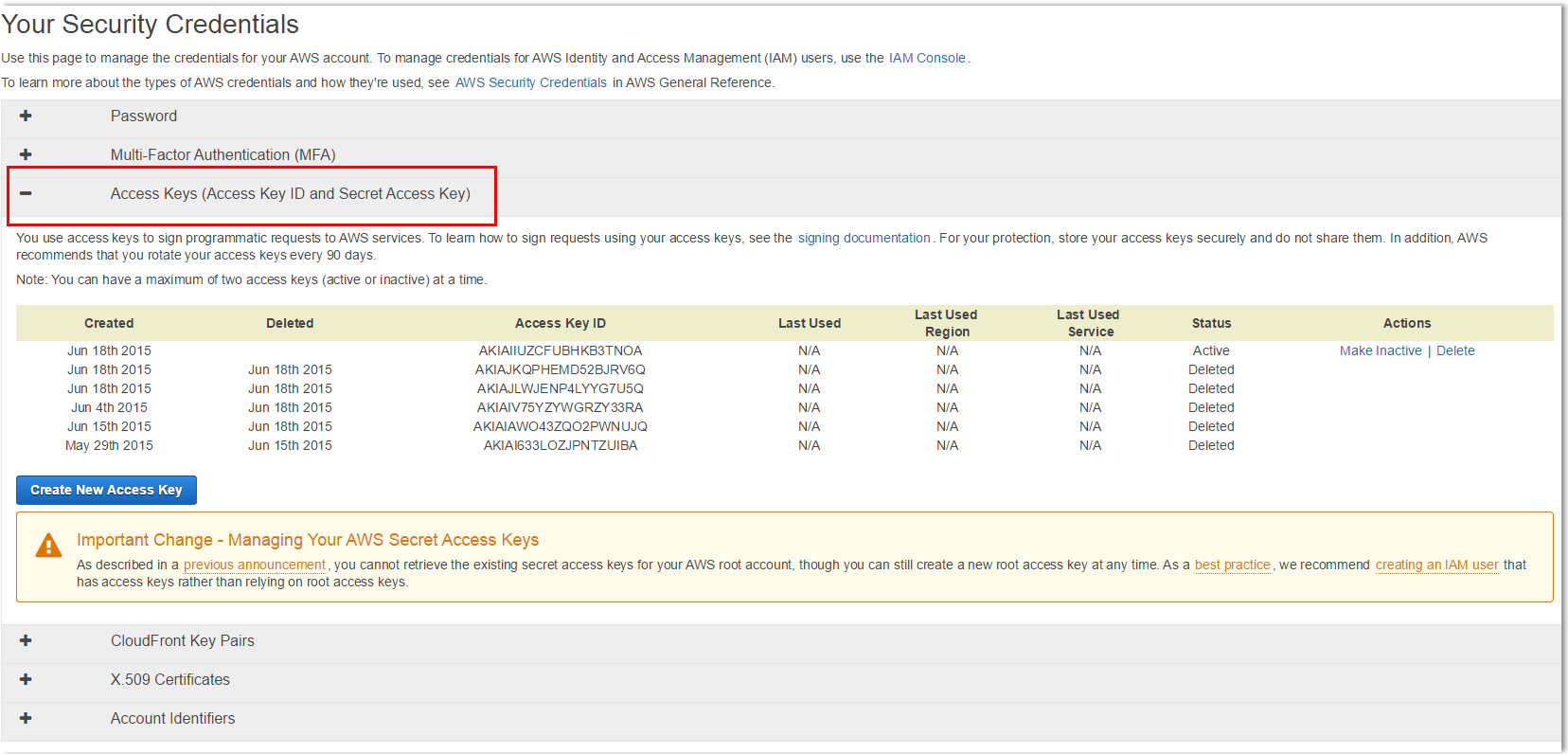
How to Create an Access Key and Secret Key in IAM The process for creating an access key is straightforward. Jump into the IAM console and find the user you want to create the access key for. Next, you’ll click the “security credentials” tab and then click the “create access key” button. Open the AWS Console. Click on your username near the top right and select My Security Credentials. Click on Users in the sidebar. Click on your username. Click on the Security Credentials tab. Click Create Access Key. Click Show User Security Credentials. Access Keys are used to sign the requests you send to Amazon S3. Like the Username/Password pair you use to access your AWS Management Console, Access Key Id and Secret Access Key are used for programmatic (API) access to AWS services. You can manage your Access Keys in AWS Management Console.
| #!/bin/bash |
| # |
| # Sample for getting temp session token from AWS STS |
| # |
| # aws --profile youriamuser sts get-session-token --duration 3600 |
| # --serial-number arn:aws:iam::012345678901:mfa/user --token-code 012345 |
| # |
| # Based on : https://github.com/EvidentSecurity/MFAonCLI/blob/master/aws-temp-token.sh |
| # |
| AWS_CLI=`which aws` |
| if [ $?-ne 0 ];then |
| echo'AWS CLI is not installed; exiting' |
| exit 1 |
| else |
| echo'Using AWS CLI found at $AWS_CLI' |
| fi |
| if [ $#-ne 1 ];then |
| echo'Usage: $0 <MFA_TOKEN_CODE>' |
| echo'Where:' |
| echo' <MFA_TOKEN_CODE> = Code from virtual MFA device' |
| exit 2 |
| fi |
| AWS_USER_PROFILE=userName |
| AWS_2AUTH_PROFILE=2auth |
| ARN_OF_MFA=GAKTxxxxxxxxxx |
| MFA_TOKEN_CODE=$1 |
| DURATION=129600 |
| echo'AWS-CLI Profile: $AWS_CLI_PROFILE' |
| echo'MFA ARN: $ARN_OF_MFA' |
| echo'MFA Token Code: $MFA_TOKEN_CODE' |
| set -x |
| read AWS_ACCESS_KEY_ID AWS_SECRET_ACCESS_KEY AWS_SESSION_TOKEN <<< |
| $( aws --profile $AWS_USER_PROFILE sts get-session-token |
| --duration $DURATION |
| --serial-number $ARN_OF_MFA |
| --token-code $MFA_TOKEN_CODE |
| --output text awk '{ print $2, $4, $5 }') |
| echo 'AWS_ACCESS_KEY_ID: ' $AWS_ACCESS_KEY_ID |
| echo 'AWS_SECRET_ACCESS_KEY: ' $AWS_SECRET_ACCESS_KEY |
| echo 'AWS_SESSION_TOKEN: ' $AWS_SESSION_TOKEN |
| if [ -z '$AWS_ACCESS_KEY_ID' ] |
| then |
| exit 1 |
| fi |
| `aws --profile $AWS_2AUTH_PROFILE configure set aws_access_key_id '$AWS_ACCESS_KEY_ID'` |
| `aws --profile $AWS_2AUTH_PROFILE configure set aws_secret_access_key '$AWS_SECRET_ACCESS_KEY'` |
| `aws --profile $AWS_2AUTH_PROFILE configure set aws_session_token '$AWS_SESSION_TOKEN'` |
AWS Access Keys. Access Keys are used to sign the requests you send to Amazon S3. Like the Username/Password pair you use to access your AWS Management Console, Access Key Id and Secret Access Key are used for programmatic (API) access to AWS services. It is worth noting, that as this is an operation being performed against a given IAM user, you do not need to be logged in as that user to generate keys. Any authorized user such as the root user, or another properly authorized IAM user can perform these actions.
Generate Aws_access_key_id And Aws_secret_access_key Data
| ~/.aws/credentials |
| [userName] |
| aws_access_key_id: AxxxxxxxxxxxxxxxxxQ |
| aws_secret_access_key: hxxxxxxxxxxxxxxxxxx4 |
| [2auth] |
| aws_access_key_id = AxxxxxxxxxxxxxxxxxA |
| aws_secret_access_key = pxxxxxxxxxxxxxxxxxxxxxy |
| aws_session_token = AxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxF |